EAP 配置
本文提供了为 VPN 配置文件创建可扩展身份验证协议 (EAP) 配置 XML 的分步指南,包括有关在 Windows 10 中筛选 EAP 证书的信息。
为 VPN 配置文件创建 EAP 配置 XML
若要使用随附在框中的 rasphone 工具从桌面获取 EAP 配置,请执行以下操作:
运行 rasphone.exe。
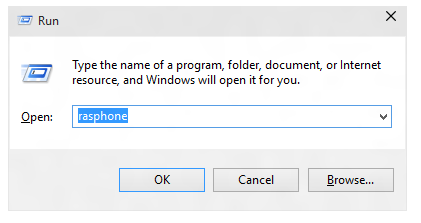
如果当前没有 VPN 连接,并且看到以下消息,请选择“ 确定”。
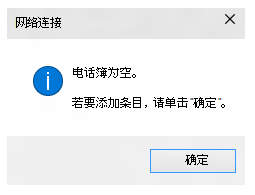
在向导中,选择“ 工作区网络”。
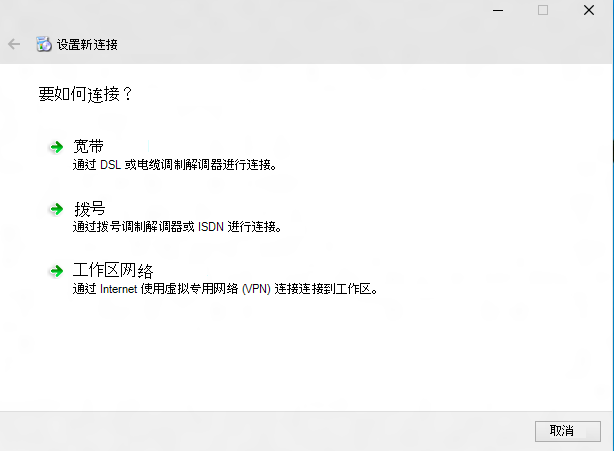
输入 Internet 地址和连接名称。 这些详细信息可能是虚假的,因为它不会影响身份验证参数。
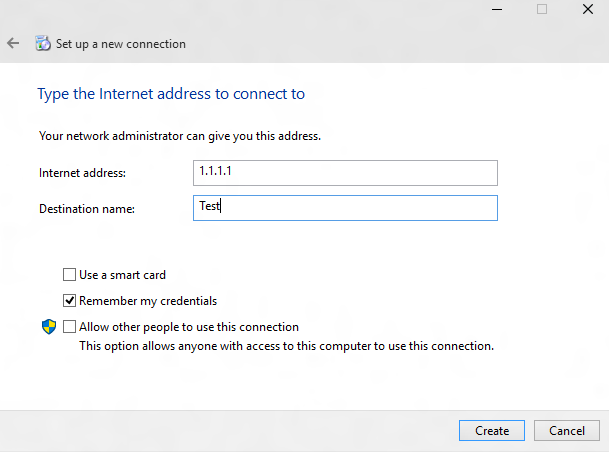
创建假 VPN 连接。 在此处显示的 UI 中,选择“ 属性”。
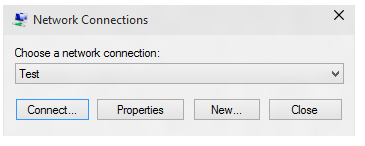
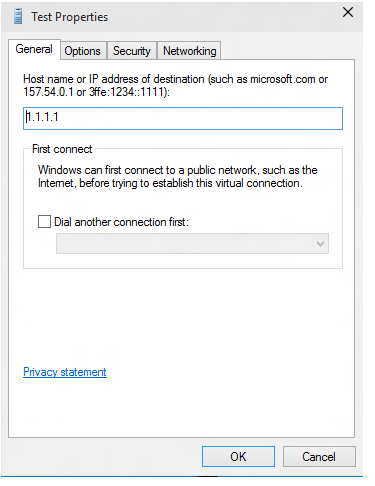
在“ 测试属性 ”对话框中,选择“ 安全性 ”选项卡。
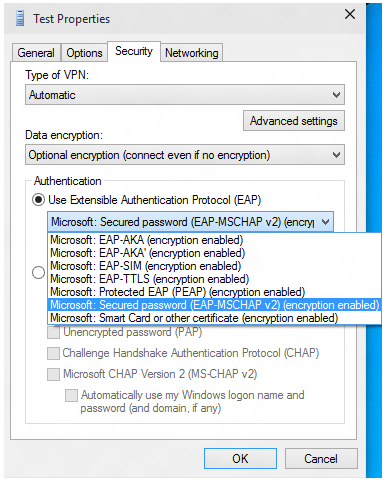
在“ 安全性 ”选项卡上,选择“ 使用可扩展身份验证协议 (EAP) 。

从下拉菜单中,选择要配置的 EAP 方法,然后选择 “属性” 以根据需要进行配置。
切换到 PowerShell 并使用以下 cmdlet 检索 EAP 配置 XML。
Get-VpnConnection -Name Test下面是一个示例输出。
Name : Test ServerAddress : 1.1.1.1 AllUserConnection : False Guid : {EC87F6C9-8823-416C-B92B-517D592E250F} TunnelType : Automatic AuthenticationMethod : {Eap} EncryptionLevel : Optional L2tpIPsecAuth : Certificate UseWinlogonCredential : False EapConfigXmlStream : #document ConnectionStatus : Disconnected RememberCredential : True SplitTunneling : False DnsSuffix : IdleDisconnectSeconds : 0$a = Get-VpnConnection -Name Test$a.EapConfigXmlStream.InnerXml下面是一个示例输出。
<EapHostConfig xmlns="http://www.microsoft.com/provisioning/EapHostConfig"> <EapMethod> <Type xmlns="http://www.microsoft.com/provisioning/EapCommon">13</Type> <VendorId xmlns="http://www.microsoft.com/provisioning/EapCommon">0</VendorId> <VendorType xmlns="http://www.microsoft.com/provisioning/EapCommon">0</VendorType> <AuthorId xmlns="http://www.microsoft.com/provisioning/EapCommon">0</AuthorId> </EapMethod> <Config xmlns="http://www.microsoft.com/provisioning/EapHostConfig"> <Eap xmlns="http://www.microsoft.com/provisioning/BaseEapConnectionPropertiesV1"> <Type>13</Type> <EapType xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV1"> <CredentialsSource> <CertificateStore> <SimpleCertSelection>true</SimpleCertSelection> </CertificateStore> </CredentialsSource> <ServerValidation> <DisableUserPromptForServerValidation>false</DisableUserPromptForServerValidation> <ServerNames /> </ServerValidation> <DifferentUsername>false</DifferentUsername> <PerformServerValidation xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV2">true</PerformServerValidation> <AcceptServerName xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV2">true</AcceptServerName> <TLSExtensions xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV2"> <FilteringInfo xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV3"> <ClientAuthEKUList Enabled="true" /> <AnyPurposeEKUList Enabled="true" /> </FilteringInfo> </TLSExtensions> </EapType> </Eap> </Config> </EapHostConfig>注意
如果需要以转义格式传递此 XML,则应检查移动设备管理 (MDM) 供应商。 所有 EAP 方法的 XSD 都随附在框中,可在以下位置找到:
- C:\Windows\schemas\EAPHost
- C:\Windows\schemas\EAPMethods
EAP 证书筛选
在部署中,如果在设备上预配了多个证书,并且预配的 Wi-Fi 配置文件没有严格的筛选条件,则连接到 Wi-Fi 时可能会看到连接失败。 解决方案是确保预配的 Wi-Fi 配置文件具有严格的筛选条件,以便仅匹配一个证书。
为 VPN 和 Wi-Fi 部署基于证书的 EAP 身份验证的企业可能会遇到多个证书满足默认身份验证条件的情况。 这种情况可能会导致以下问题:
- 系统可能会提示用户选择证书。
- 错误的证书可能是自动选择的,并导致身份验证失败。
生产就绪部署必须具有相应的证书详细信息,作为要部署的配置文件的一部分。 以下信息说明如何创建或更新 EAP 配置 XML,以便筛选掉无关的证书,并使用相应的证书进行身份验证。
必须使用环境的相关信息更新 EAP XML。 可以通过编辑以下 XML 示例或使用分步 UI 指南手动完成此任务。 更新 EAP XML 后,请参阅 MDM 中的说明部署更新的配置,如下所示:
- 对于 Wi-Fi,请查找
<EAPConfig>当前 WLAN 配置文件 XML 的 部分。 (此部分是你在 Wi-Fi CSP.) 中为 WLanXml 节点指定的内容。在这些标记中,你将找到完整的 EAP 配置。 将 下的<EAPConfig>部分替换为更新的 XML,并更新 Wi-Fi 配置文件。 可以参阅 MDM 有关如何部署新 Wi-Fi 配置文件的指南。 - 对于 VPN,EAP 配置是 MDM 配置中的单独字段。 请与 MDM 提供程序协作,以标识和更新相应的字段。
有关 EAP 设置的信息,请参阅 用于网络访问的可扩展身份验证协议 (EAP) 。
有关生成 EAP XML 的信息,请参阅 EAP 配置一文。
有关 EKU) (扩展密钥用法的详细信息,请参阅 https://datatracker.ietf.org/doc/html/rfc5280#section-4.2.1.12。
有关将 EKU 添加到证书的信息,请参阅 https://technet.microsoft.com/library/cc731792.aspx。
以下列表介绍了用于 EAP 的证书的先决条件:
证书必须至少具有以下 EKU 属性之一:
- 客户端身份验证:如 RFC 5280 所定义,此属性是定义完善的 OID,值为 1.3.6.1.5.5.7.3.2。
- 任何目的:此属性是 EKU 定义的属性,由 Microsoft 发布。 它是定义完善的 OID,值为 1.3.6.1.4.1.311.10.12.1。 包含此 OID 意味着证书可用于任何目的。 此 EKU 与“所有用途 EKU”的优点是,仍可将其他非关键或自定义 EKU 添加到证书中,以便进行有效筛选。
- 所有目的:如 RFC 5280 所定义,如果 CA 包含 EKU 以满足某些应用程序需求,但不想限制密钥的使用,则 CA 可以添加 EKU 值 0。 具有此类 EKU 的证书可用于所有目的。
客户端上的用户或计算机证书必须链接到受信任的根 CA。
用户或计算机证书不会使 CryptoAPI 证书存储区执行的任何检查失败,并且证书通过了远程访问策略中的要求。
用户或计算机证书不会使 Internet 身份验证服务 (IAS) /Radius Server 中指定的任何证书对象标识符检查失败。
证书中的 SubjectAltName) 扩展 (使用者可选名称包含用户 UPN () 的用户主体名称。
以下 XML 示例介绍了 EAP TLS XML 的属性,包括证书筛选。
注意
对于 PEAP 或 TTLS 配置文件,EAP TLS XML 嵌入到某些 PEAP 特定的或特定于 TTLS 的元素中。
<EapHostConfig xmlns="http://www.microsoft.com/provisioning/EapHostConfig">
<EapMethod>
<Type xmlns="http://www.microsoft.com/provisioning/EapCommon">13</Type>
<!--The above property defines the Method type for EAP, 13 means EAP TLS -->
<VendorId xmlns="http://www.microsoft.com/provisioning/EapCommon">0</VendorId>
<VendorType xmlns="http://www.microsoft.com/provisioning/EapCommon">0</VendorType>
<AuthorId xmlns="http://www.microsoft.com/provisioning/EapCommon">0</AuthorId>
<!--The 3 properties above define the method publishers, this is seen primarily in 3rd party Vendor methods.-->
<!-- For Microsoft EAP TLS the value of the above fields will always be 0 -->
</EapMethod>
<!-- Now that the EAP Method is Defined we will go into the Configuration -->
<Config xmlns="http://www.microsoft.com/provisioning/EapHostConfig">
<Eap xmlns="http://www.microsoft.com/provisioning/BaseEapConnectionPropertiesV1">
<Type>13</Type>
<EapType xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV1">
<CredentialsSource>
<!-- Credential Source can be either CertificateStore or SmartCard -->
<CertificateStore>
<SimpleCertSelection>true</SimpleCertSelection>
<!--SimpleCertSelection automatically selects a cert if there are mutiple identical (Same UPN, Issuer, etc.) certs.-->
<!--It uses a combination of rules to select the right cert-->
</CertificateStore>
</CredentialsSource>
<ServerValidation>
<!-- ServerValidation fields allow for checks on whether the server being connected to and the server cert being used are trusted -->
<DisableUserPromptForServerValidation>false</DisableUserPromptForServerValidation>
<ServerNames/>
</ServerValidation>
<DifferentUsername>false</DifferentUsername>
<PerformServerValidation xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV2">false</PerformServerValidation>
<AcceptServerName xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV2">false</AcceptServerName>
<TLSExtensions xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV2">
<!-- For filtering the relevant information is below -->
<FilteringInfo xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV3">
<CAHashList Enabled="true">
<!-- The above implies that you want to filter by Issuer Hash -->
<IssuerHash>ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff
<!-- Issuing certs thumbprint goes here-->
</IssuerHash>
<!-- You can add multiple entries and it will find the list of certs that have at least one of these certs in its chain-->
</CAHashList>
<EKUMapping>
<!-- This section defines Custom EKUs that you may be adding-->
<!-- You do not need this section if you do not have custom EKUs -->
<!-- You can have multiple EKUs defined here and then referenced below as shown -->
<EKUMap>
<EKUName>
<!--Add a friendly Name for an EKU here for example -->ContostoITEKU</EKUName>
<EKUOID>
<!--Add the OID Value your CA adds to the certificate here, for example -->1.3.6.1.4.1.311.42.1.15</EKUOID>
</EKUMap>
<!-- All the EKU Names referenced in the example below must first be defined here
<EKUMap>
<EKUName>Example1</EKUName>
<EKUOID>2.23.133.8.3</EKUOID>
</EKUMap>
<EKUMap>
<EKUName>Example2</EKUName>
<EKUOID>1.3.6.1.4.1.311.20.2.1</EKUOID>
</EKUMap>
-->
</EKUMapping>
<ClientAuthEKUList Enabled="true">
<!-- The above implies that you want certs with Client Authentication EKU to be used for authentication -->
<EKUMapInList>
<!-- This section implies that the certificate should have the following custom EKUs in addition to the Client Authentication EKU -->
<EKUName>
<!--Use the name from the EKUMap Field above-->ContostoITEKU</EKUName>
</EKUMapInList>
<!-- You can have multiple Custom EKUs mapped here, Each additional EKU will be processed with an AND operand -->
<!-- For example, Client Auth EKU AND ContosoITEKU AND Example1 etc. -->
<EKUMapInList>
<EKUName>Example1</EKUName>
</EKUMapInList>
</ClientAuthEKUList>
<AllPurposeEnabled>true</AllPurposeEnabled>
<!-- Implies that a certificate with the EKU field = 0 will be selected -->
<AnyPurposeEKUList Enabled="true"/>
<!-- Implies that a certificate with the EKU oid Value of 1.3.6.1.4.1.311.10.12.1 will be selected -->
<!-- Like for Client Auth you can also add Custom EKU properties with AnyPurposeEKUList (but not with AllPurposeEnabled) -->
<!-- So here is what the above policy implies.
The certificate selected will have
Issuer Thumbprint = ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff ff
AND
((Client Authentication EKU AND ContosoITEKU) OR (AnyPurposeEKU) OR AllPurpose Certificate)
Any certificate(s) that match these criteria will be utilised for authentication
-->
</FilteringInfo>
</TLSExtensions>
</EapType>
</Eap>
</Config>
</EapHostConfig>
注意
EAP TLS XSD 位于 %systemdrive%\Windows\schemas\EAPMethods\eaptlsconnectionpropertiesv3.xsd。
或者,可以使用以下过程创建 EAP 配置 XML:
按照 EAP 配置一文中的步骤 1 到 7 进行操作。
在 “Microsoft VPN SelfHost 属性 ”对话框中,从下拉菜单中选择“ Microsoft:智能卡或其他证书 ”, (此值选择 EAP TLS) 。
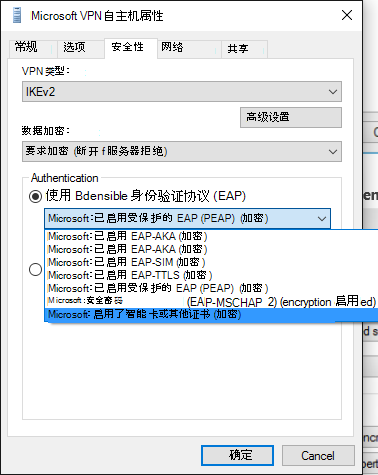
注意
对于 PEAP 或 TTLS,请选择适当的方法并继续执行此过程。
选择下拉菜单下的 “属性” 按钮。
在 “智能卡”或其他“证书属性” 菜单上,选择“ 高级 ”按钮。
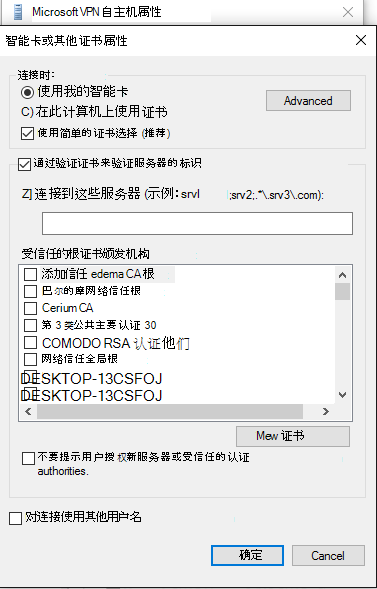
在 “配置证书选择 ”菜单上,根据需要调整筛选器。

选择“确定”关闭窗口并返回到“main rasphone.exe”对话框。
关闭 rasphone 对话框。
继续按照步骤 9 中的 EAP 配置一文中的过程获取具有适当筛选的 EAP TLS 配置文件。
注意
还可以通过此 UI 设置所有其他适用的 EAP 属性。 有关这些属性含义的指南,请参阅 用于网络访问的可扩展身份验证协议 (EAP) 一文。
相关主题
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈