BitLocker 恢复概述
BitLocker 恢复是一个过程,如果驱动器未使用默认解锁机制解锁,则可以还原对受 BitLocker 保护的驱动器的访问。
本文介绍触发 BitLocker 恢复的方案、如何配置设备以保存恢复信息,以及还原对锁定驱动器的访问的选项。
BitLocker 恢复方案
以下列表提供了导致设备在启动 Windows 时进入 BitLocker 恢复模式的常见事件示例:
输入错误的 PIN 次数过多
如果使用基于 USB 的密钥而不是 TPM,则关闭对在预启动环境中从 BIOS 或 UEFI 固件读取 USB 设备的支持
将 CD 或 DVD 驱动器以 BIOS 启动顺序在硬盘驱动器之前 (与虚拟机)
停靠或取消停靠便携式计算机
对磁盘上的 NTFS 分区表的更改
对启动管理器的更改
关闭、禁用、停用或清除 TPM
TPM 自测试失败
使用新的 TPM 将主板升级到新的主板
升级关键的早期启动组件,例如 BIOS 或 UEFI 固件升级
从操作系统中隐藏 TPM
修改 TPM 验证配置文件使用的平台配置寄存器 (PCR)
将受 BitLocker 保护的驱动器移动到新计算机
在具有 TPM 1.2 的设备上,更改 BIOS 或固件启动设备顺序
超过允许的最大失败登录尝试次数
注意
若要利用此功能,必须配置策略设置交互式登录:计算机帐户锁定阈值位于计算机配置>Windows 设置安全设置>>本地策略>安全选项中。 或者,使用 Exchange ActiveSyncMaxFailedPasswordAttempts 策略设置或 DeviceLock 配置服务提供程序 (CSP) 。
作为 BitLocker 恢复过程的一部分,建议确定导致设备进入恢复模式的原因。 根本原因分析可能有助于防止将来再次出现问题。 例如,如果确定攻击者通过获取物理访问权限修改了设备,则可以实施新的安全策略来跟踪谁具有物理状态。
对于计划方案(例如已知的硬件或固件升级),可以通过暂时挂起 BitLocker 保护来避免启动恢复。 暂停 BitLocker 会使驱动器保持完全加密状态,管理员可以在完成计划的任务后快速恢复 BitLocker 保护。 使用 暂停 和 恢复 还会重新密封加密密钥,而无需输入恢复密钥。
注意
如果暂停,BitLocker 会在设备重新启动时自动恢复保护,除非使用 PowerShell 或 manage-bde.exe 命令行工具指定了重新启动计数。 有关暂停 BitLocker 的详细信息,请参阅 BitLocker 操作指南。
提示
恢复是在计划外或不需要的行为上下文中描述的。 但是,恢复也可以作为预期的生产方案进行,例如,为了管理访问控制。 将设备重新部署到组织中的其他部门或员工时,可以在将设备交付给新用户之前强制恢复 BitLocker。
Windows RE和 BitLocker 恢复
Windows 恢复环境 (Windows RE) 可用于恢复对受 BitLocker 保护的驱动器的访问。 如果设备在两次故障后无法启动, 则“启动修复” 会自动启动。
当启动修复因启动失败而自动启动时,它仅执行操作系统和驱动程序文件修复,前提是启动日志或任何可用的故障转储指向特定的损坏文件。 在支持 PCR[7] 的特定 TPM 度量的设备上,TPM 会验证Windows RE是否为受信任的操作环境,并在未修改Windows RE时解锁任何受 BitLocker 保护的驱动器。 如果已修改Windows RE环境(例如禁用 TPM),则驱动器将一直处于锁定状态,直到提供 BitLocker 恢复密钥。 如果启动修复无法自动运行,而是从修复磁盘手动启动Windows RE,则必须提供 BitLocker 恢复密钥才能解锁受 BitLocker 保护的驱动器。
在对 OS 驱动器保护程序使用 TPM + PIN 或密码的设备上启动“从Windows RE删除所有重置内容”时,Windows RE还会要求提供 BitLocker 恢复密钥。 如果在仅具有 TPM 保护的无键盘设备上启动 BitLocker 恢复,Windows RE(而不是启动管理器)会要求提供 BitLocker 恢复密钥。 输入密钥后,可以访问Windows RE故障排除工具或正常启动 Windows。
Windows RE显示的 BitLocker 恢复屏幕具有讲述人和屏幕键盘等辅助工具,可帮助你输入 BitLocker 恢复密钥:
- 若要在 Windows RE 中恢复 BitLocker 期间激活讲述人,请按 WIN + Ctrl + Enter
- 若要激活屏幕键盘,请点击文本输入控件
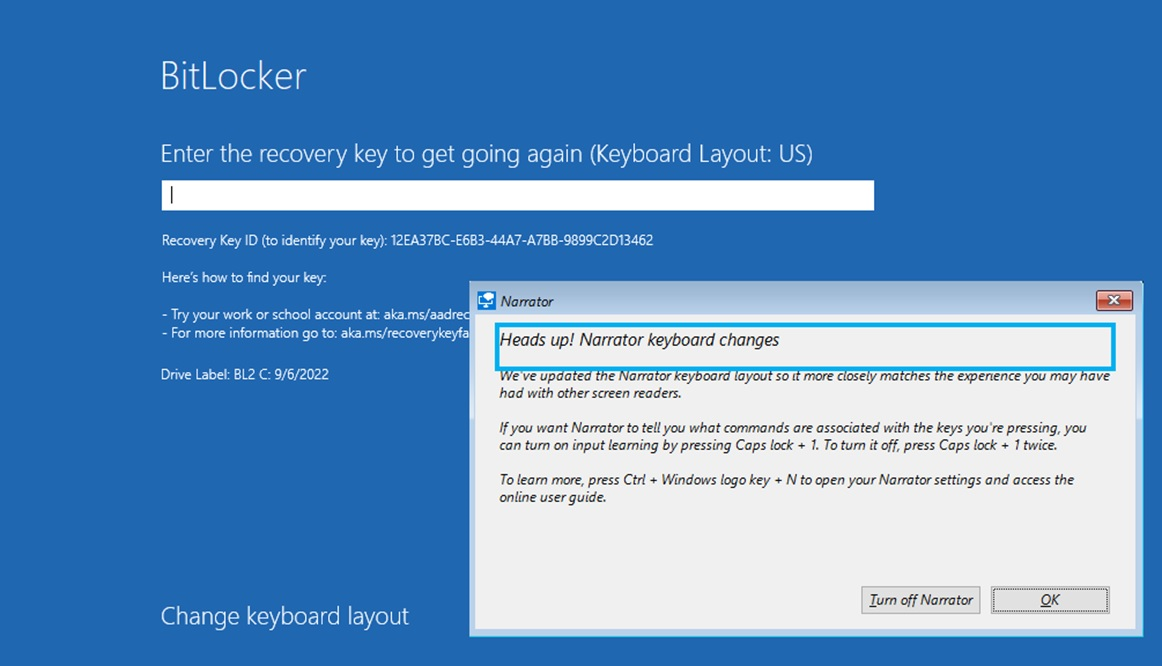
如果 Windows 启动管理器请求 BitLocker 恢复密钥,则这些工具可能不可用。
BitLocker 恢复选项
在恢复方案中,以下用于还原驱动器访问权限的选项可能可用,具体取决于应用于设备的策略设置:
- 恢复密码:在卷处于恢复模式时用于解锁卷的 48 位数字。 恢复密码可能保存为文本文件、打印或存储在 Microsoft Entra ID 或 Active Directory 中。 用户可以提供恢复密码(如果可用)
- 恢复密钥:存储在可移动媒体上的加密密钥,可用于恢复 BitLocker 卷上加密的数据。 文件名的格式为
<protector_id>.bek。 对于 OS 驱动器,如果 BitLocker 检测到在设备启动时阻止其解锁驱动器的条件,则恢复密钥可用于获取对设备的访问权限。 如果出于某种原因忘记了密码或设备无法访问驱动器,则恢复密钥还可用于访问使用 BitLocker 加密的固定数据驱动器和可移动驱动器
- 密钥包:可与 BitLocker 修复工具一起使用的解密密钥,以重建驱动器的关键部分并打捞可恢复的数据。 使用密钥包以及 恢复密码 或 恢复密钥,可以解密受 BitLocker 保护的驱动器损坏的部分内容。 每个密钥包仅适用于具有相应驱动器标识符的驱动器。 密钥包不会自动生成,可以保存在文件或Active Directory 域服务中。 密钥包不能存储在 Microsoft Entra ID
- 数据恢复代理证书:数据恢复代理 (DRA) 是一种与 Active Directory 安全主体关联的证书,可用于访问配置了匹配公钥的任何 BitLocker 加密驱动器。 DRA 可以使用其凭据解锁驱动器。 如果驱动器是 OS 驱动器,则必须将驱动器作为数据驱动器装载到另一台设备上,才能解锁 DRA
提示
用户可在数据和可移动驱动器) 控制面板小程序 (或预启动恢复屏幕中提供恢复密码和恢复密钥。 建议配置策略设置以自定义预启动恢复屏幕,例如添加自定义消息、URL 和技术支持联系人信息。 有关详细信息,请查看 BitLocker 预启动恢复屏幕一文。
规划 BitLocker 恢复过程时,请先参阅组织当前恢复敏感信息的最佳做法。 例如:
| ☑️ | 问题 |
|---|---|
| 🔲 | 组织如何处理丢失或忘记的密码? |
| 🔲 | 组织如何执行智能卡 PIN 重置? |
| 🔲 | 是否允许用户保存或检索其拥有的设备的恢复信息? |
| 🔲 | 你希望用户在 BitLocker 配置过程中参与多少? 你希望用户与进程交互、保持静默还是同时保持两者? |
| 🔲 | 要将 BitLocker 恢复密钥存储在何处? |
| 🔲 | 是否启用恢复密码轮换? |
回答这些问题有助于确定组织的最佳 BitLocker 恢复过程,并相应地配置 BitLocker 策略设置。 例如,如果组织有重置密码的过程,则可以将类似的过程用于 BitLocker 恢复。 如果不允许用户保存或检索恢复信息,组织可以使用数据恢复代理 (DRA) ,或自动备份恢复信息。
以下策略设置定义可用于还原对受 BitLocker 保护的驱动器的访问的恢复方法:
提示
在每个策略中,选择“将 BitLocker 恢复信息保存到Active Directory 域服务然后选择要在 AD DS 中存储的 BitLocker 恢复信息。 使用选项在恢复信息存储在 AD DS 中之前不要启用 BitLocker,以防止用户启用 BitLocker,除非驱动器的 BitLocker 恢复信息备份成功以Microsoft Entra ID或 AD DS。
BitLocker 恢复密码
若要恢复 BitLocker,用户可以使用恢复密码(如果可用)。 BitLocker 恢复密码对于创建它的设备是唯一的,可以采用不同的方式保存。 根据配置的策略设置,恢复密码可以是:
- 保存在 Microsoft Entra ID 中,用于加入Microsoft Entra
- 已加入 Active Directory 的设备保存在 AD DS 中
- 保存在文本文件上
- 已打印
拥有恢复密码的访问权限允许持有者解锁受 BitLocker 保护的卷并访问其所有数据。 因此,组织必须建立控制对恢复密码的访问的过程,并确保这些密码与它们保护的设备分开进行安全存储。
注意
可以选择将 BitLocker 恢复密钥存储在用户的 Microsoft 帐户中。 选项适用于不是域成员且用户使用 Microsoft 帐户的设备。 将恢复密码存储在 Microsoft 帐户中是默认建议的恢复密钥存储方法,适用于未Microsoft Entra加入或已加入 Active Directory 的设备。
恢复密码的备份应在启用 BitLocker 之前进行配置,但也可以在加密后完成,如 BitLocker 操作指南中所述。
组织中的首选备份方法是将 BitLocker 恢复信息自动存储在中心位置。 根据组织的要求,恢复信息可以存储在Microsoft Entra ID、AD DS 或文件共享中。
建议使用以下 BitLocker 备份方法:
- 对于已加入Microsoft Entra的设备,请将恢复密钥存储在 Microsoft Entra ID
- 对于已加入 Active Directory 的设备,请将恢复密钥存储在 AD DS 中
注意
没有自动方法可将可移动存储设备的恢复密钥存储在 Microsoft Entra ID 或 AD DS 中。 但是,可以使用 PowerShell 或 manage.bde.exe 命令执行此操作。 有关详细信息和示例,请查看 BitLocker 操作指南。
数据恢复代理
DRA 可用于恢复 OS 驱动器、固定数据驱动器和可移动数据驱动器。 但是,当用于恢复 OS 驱动器时,操作系统驱动器必须作为 数据驱动器 装载在另一台设备上,才能使 DRA 能够解锁驱动器。 数据恢复代理在加密后会添加到驱动器中,并在加密发生后进行更新。
对密码或密钥恢复使用 DRA 的好处是,DRA 充当 BitLocker 的主密钥 。 使用 DRA,可以恢复受策略保护的任何卷,而无需为每个单独的卷查找特定的密码或密钥。
若要为已加入 Active Directory 域的设备配置 DRA,需要执行以下步骤:
- 获取 DRA 证书。 在使用证书之前,BitLocker 会检查以下密钥用法和增强的密钥用法属性。
- 如果存在密钥用法属性,则它必须是:
CERT_DATA_ENCIPHERMENT_KEY_USAGECERT_KEY_AGREEMENT_KEY_USAGECERT_KEY_ENCIPHERMENT_KEY_USAGE
- 如果存在 EKU) 属性 (增强的密钥用法,则它必须是:
- 如策略设置中指定的,或默认值
1.3.6.1.4.1.311.67.1.1 - 证书颁发机构支持的任何 EKU 对象标识符 (CA)
- 如策略设置中指定的,或默认值
- 如果存在密钥用法属性,则它必须是:
- 使用路径通过组策略添加 DRA: 计算机配置>策略>Windows 设置>安全设置>公钥策略>BitLocker 驱动器加密
- 配置 “为组织提供唯一标识符 ”策略设置,以将唯一标识符关联到使用 BitLocker 启用的新驱动器。 标识字段是用于唯一标识业务部门或组织的字符串。 标识字段是管理受 BitLocker 保护的驱动器上的数据恢复代理所必需的。 BitLocker 仅在驱动器上存在标识字段且与设备上配置的值相同时管理和更新 DRA
- 配置以下策略设置,以允许对每种驱动器类型使用 DRA 进行恢复:
存储在 Microsoft Entra ID 中的 BitLocker 恢复信息
已加入Microsoft Entra设备的 BitLocker 恢复信息可以存储在 Microsoft Entra ID 中。 在 Microsoft Entra ID 中存储 BitLocker 恢复密码的优点是,用户可以轻松地从 Web 检索分配给他们的设备的密码,而无需涉及支持人员。
还可以将恢复密码的访问权限委托给支持人员,以简化支持方案。
存储在 Microsoft Entra ID 中的 BitLocker 恢复密码信息是一种bitlockerRecoveryKey资源类型。 可以从 Microsoft Entra 管理中心、Microsoft Intune管理中心 (检索资源,这些设备在 Microsoft Intune) 中注册、使用 PowerShell 或 Microsoft Graph。 有关详细信息,请参阅 bitlockerRecoveryKey 资源类型。
存储在 AD DS 中的 BitLocker 恢复信息
已加入 Active Directory 域的设备的 BitLocker 恢复信息可以存储在 AD DS 中。 信息存储在计算机对象本身的子对象中。 每个 BitLocker 恢复对象都包含恢复密码和其他恢复信息。 每个计算机对象下可以存在多个 BitLocker 恢复对象,因为可以有多个恢复密码与启用了 BitLocker 的卷相关联。
BitLocker 恢复对象的名称包含全局唯一标识符 (GUID) 和日期和时间信息,长度固定为 63 个字符。 语法为 <Object Creation Date and Time><Recovery GUID>。
注意
Active Directory 维护计算机对象的所有恢复密码的历史记录。 除非删除了计算机对象,否则不会自动从 AD DS 中删除旧的恢复密钥。
BitLocker 恢复对象的 (cn) 的公用名是 ms-FVE-RecoveryInformation。 每个 ms-FVE-RecoveryInformation 对象具有以下属性:
| 属性名称 | 描述 |
|---|---|
ms-FVE-RecoveryPassword |
用于恢复 BitLocker 加密磁盘卷的 48 位恢复密码。 |
ms-FVE-RecoveryGuid |
与 BitLocker 恢复密码关联的 GUID。 在 BitLocker 的恢复模式下,GUID 会显示给用户,以便找到正确的恢复密码来解锁卷。 GUID 也包含在恢复对象的名称中。 |
ms-FVE-VolumeGuid |
与 BitLocker 支持的磁盘卷关联的 GUID。 虽然存储在) 中的 ms-FVE-RecoveryGuid 密码 (对于每个恢复密码都是唯一的,但每个 BitLocker 加密卷的卷标识符是唯一的。 |
ms-FVE-KeyPackage |
卷的 BitLocker 加密密钥由相应的恢复密码保护。 使用此密钥包和恢复密码 (存储在) 中 ms-FVE-RecoveryPassword ,如果磁盘损坏,则可以解密受 BitLocker 保护的卷的某些部分。 每个密钥包仅适用于具有存储在) 中的 ms-FVE-VolumeGuid 相应卷标识符 (卷。 BitLocker 修复工具可用于使用密钥包。 |
若要详细了解存储在 AD DS 中的 BitLocker 属性,请查看以下文章:
默认情况下不保存 BitLocker 密钥包。 若要在 AD DS 中保存包以及恢复密码,必须在控制恢复方法的策略中选择 “备份恢复密码和密钥包 策略”设置。 密钥包也可以从工作卷导出。
如果恢复信息未备份到 AD DS,或者想要将密钥包保存在备用位置,请使用以下命令为卷生成密钥包:
manage-bde.exe -KeyPackage C: -id <id> -path <path>
在指定路径中创建文件名格式 BitLocker Key Package {<id>}.KPG 为 的文件。
注意
若要从受 BitLocker 保护的未锁定卷导出新的密钥包,需要本地管理员访问工作卷,然后才能对该卷造成任何损坏。
后续步骤
了解如何获取已加入Microsoft Entra、Microsoft Entra混合联接和已加入 Active Directory 的设备的 BitLocker 恢复信息,以及如何还原对锁定驱动器的访问权限:
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈

