Microsoft Defender 应用程序防护概述
注意
- Microsoft Defender 应用程序防护(包括 Windows 独立应用启动器 API)将弃用Microsoft Edge 商业版,并且将不再更新。 请下载 Microsoft Edge For Business Security 白皮书 ,了解有关 Edge for Business 安全功能的详细信息。
- 由于已弃用应用程序防护,因此不会迁移到 Edge 清单 V3。 相应的扩展和关联的 Windows 应用商店应用 在 2024 年 5 月之后将不可用。 这会影响以下浏览器:应用程序防护 扩展 - Chrome 和 应用程序防护 扩展 - Firefox。 如果要阻止未受保护的浏览器,直到准备好在企业中停用 MDAG 使用,我们建议使用 AppLocker 策略或 Microsoft Edge 管理服务。 有关详细信息,请参阅 Microsoft Edge 和 Microsoft Defender 应用程序防护。
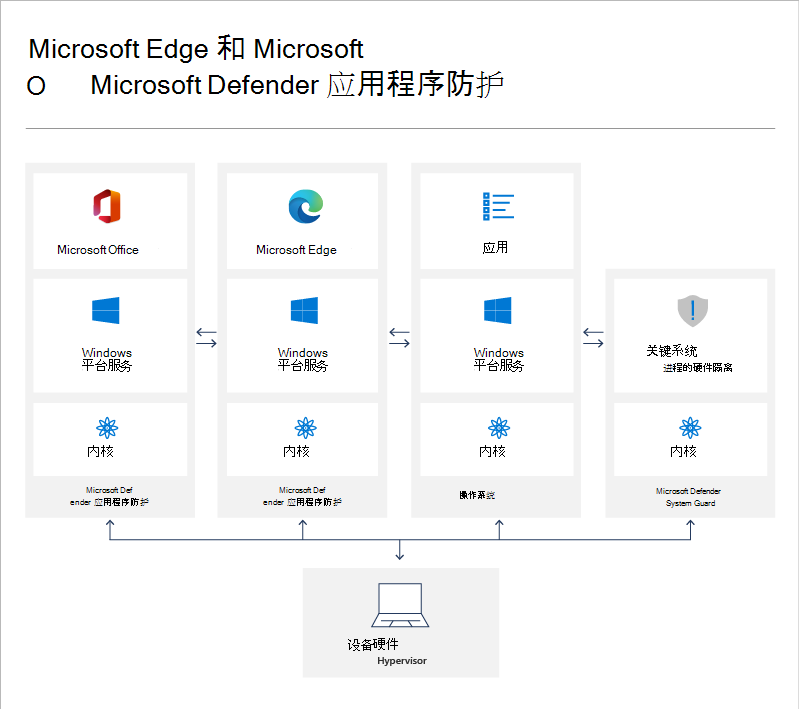
Microsoft Defender 应用程序防护 (MDAG) 旨在帮助防止新旧攻击,以帮助保持员工的工作效率。 使用我们独特的硬件隔离方法,我们的目标是通过使当前攻击方法过时来破坏攻击者使用的 playbook。
什么是应用程序防护,以及它是如何工作的?
对于 Microsoft Edge,应用程序防护有助于隔离企业定义的不受信任的站点,从而在员工浏览 Internet 时保护公司。 作为企业管理员,你需要定义哪些是受信任的网站、云资源和内部网络。 你列表上的所有内容均被视为不受信任。 如果员工通过 Microsoft Edge 或 Internet Explorer 访问不受信任的站点,Microsoft Edge 会在已启用 Hyper-V 的独立容器中打开站点。
对于 Microsoft Office,应用程序防护有助于防止不受信任的Word、PowerPoint 和 Excel 文件访问受信任的资源。 应用程序防护在已启用 Hyper-V 的独立容器中打开不受信任的文件。 隔离的 Hyper-V 容器独立于主机操作系统。 此容器隔离意味着,如果不受信任的站点或文件被证明是恶意的,则主机设备会受到保护,并且攻击者无法访问你的企业数据。 例如,此方法可让隔离容器成为匿名容器,因此,攻击者无法获得你员工的企业凭据。
哪些类型的设备应使用应用程序防护?
已创建应用程序防护,以面向多种类型的设备:
企业桌面。 这些台式机已加入域并由组织管理。 配置管理主要通过Microsoft Configuration Manager或Microsoft Intune完成。 员工通常具有标准用户权限并且使用高度带宽的有线企业网络。
企业移动笔记本电脑。 这些笔记本电脑已加入域并由组织管理。 配置管理主要通过Microsoft Configuration Manager或Microsoft Intune完成。 员工通常具有标准用户权限并且使用高度带宽的无线企业网络。
将自己的设备 (BYOD) 移动笔记本电脑。 这些个人拥有的笔记本电脑未加入域,但由组织通过Microsoft Intune等工具进行管理。 员工通常为设备上的管理员,工作时使用高速带宽的无线企业网络,在家时使用与之相当的个人网络。
个人设备。 这些个人拥有的台式机或移动笔记本电脑不是由组织加入或管理的。 用户是设备上的管理员,在家时使用高带宽无线个人网络,或在外面使用类似的公用网络。
Windows 版本和许可要求
下表列出了支持 Edge 独立模式Microsoft Defender 应用程序防护 (MDAG) 的 Windows 版本:
| Windows 专业版 | Windows 企业版 | Windows 专业教育版/SE | Windows 教育版 |
|---|---|---|---|
| 是 | 是 | 是 | 是 |
以下许可证授予 Edge 独立模式许可证权利Microsoft Defender 应用程序防护 (MDAG) :
| Windows 专业版/专业教育版/SE | Windows 企业版 E3 | Windows 企业版 E5 | Windows 教育版 A3 | Windows 教育版 A5 |
|---|---|---|---|---|
| 是 | 是 | 是 | 是 | 是 |
有关 Windows 许可的详细信息,请参阅 Windows 许可概述。
有关适用于 Edge 企业模式Microsoft Defender 应用程序防护 (MDAG) 的详细信息,请配置Microsoft Defender 应用程序防护策略设置。
相关文章
| 文章 | 描述 |
|---|---|
| Microsoft Defender 应用程序防护的系统要求 | 指定安装和使用应用程序防护所需的先决条件。 |
| 准备并安装Microsoft Defender 应用程序防护 | 提供有关确定要使用的模式(独立还是企业管理)以及如何在贵组织中安装应用程序防护的说明。 |
| 配置Microsoft Defender 应用程序防护的组策略设置 | 提供与可用组策略和 MDM 设置相关的信息。 |
| 在企业或组织中使用Microsoft Defender 应用程序防护测试方案 | 提供可用于测试组织中应用程序防护的建议测试方案的列表。 |
| 适用于 Web 浏览器的 Microsoft Defender 应用程序防护 扩展 | 介绍 Chrome 和 Firefox 的应用程序防护扩展,包括已知问题和故障排除指南 |
| Microsoft Office Microsoft Defender 应用程序防护 | 介绍 Microsoft Office 的应用程序防护,包括最低硬件要求、配置和故障排除指南 |
| 常见问题 - Microsoft Defender 应用程序防护 | 提供有关应用程序防护功能、与 Windows 操作系统集成和常规配置的常见问题解答。 |
| 在 Microsoft Intune 中使用网络边界在 Windows 设备上添加受信任的站点 | 网络边界是一项功能,可帮助你保护环境免受组织不信任的站点的防护。 |
反馈
即将发布:在整个 2024 年,我们将逐步淘汰作为内容反馈机制的“GitHub 问题”,并将其取代为新的反馈系统。 有关详细信息,请参阅:https://aka.ms/ContentUserFeedback。
提交和查看相关反馈