鎖定您的資源以保護基礎結構
身為系統管理員,您可以鎖定 Azure 訂用帳戶、資源群組或資源,以防止意外刪除和修改使用者。 鎖定會覆寫使用者的任何權限。
您可以設定鎖定,以防止刪除或修改。 在入口網站中,這些鎖定稱為 Delete 和 唯讀。 在命令行中,這些鎖定稱為 CanNotDelete 和 ReadOnly。
- CanNotDelete 表示經過授權的使用者可以讀取和修改資源,但無法刪除資源。
- ReadOnly 表示經過授權的使用者可以讀取資源,但無法刪除或更新資源。 套用此鎖定類似於將所有授權的使用者限制為讀取者角色提供的許可權。
不同於角色型訪問控制 (RBAC),您可以使用管理鎖定,將限制套用至所有使用者和角色。 若要瞭解如何設定使用者和角色的許可權,請參閱 Azure RBAC。
鎖定繼承
當您在父範圍套用鎖定時,該範圍內的所有資源都會繼承相同的鎖定。 即使是您稍後新增的資源也會繼承相同的父系鎖定。 繼承中限制最嚴格的鎖定優先。
擴充功能資源 會繼承其所套用之資源的鎖定。 例如,Microsoft.Insights/diagnostic 設定 是延伸模組資源類型。 如果您將診斷設定套用至記憶體 Blob,並鎖定記憶體帳戶,則無法刪除診斷設定。 此繼承很合理,因為診斷設定的完整資源標識碼為:
/subscriptions/{sub-id}/resourceGroups/{rg-name}/providers/Microsoft.Storage/storageAccounts/{storage-name}/blobServices/default/providers/microsoft.insights/diagnosticSettings/{setting-name}"
這符合鎖定之資源的資源識別碼範圍:
/subscriptions/{sub-id}/resourceGroups/{rg-name}/providers/Microsoft.Storage/storageAccounts/{storage-name}
如果您有 資源的刪除 鎖定並嘗試刪除其資源群組,此功能會封鎖整個刪除作業。 即使資源群組或其他資源已解除鎖定,刪除也不會發生。 您永遠不會有部分刪除。
當您 取消 Azure 訂用帳戶時:
- 資源鎖定不會封鎖訂用帳戶取消。
- Azure 會停用資源,而不是立即刪除資源來保留資源。
- Azure 只會在等候期間之後永久刪除您的資源。
了解鎖定的範圍
注意
鎖定僅適用於控制平面 Azure 作業,不適用於數據平面作業。
Azure 控制平面作業會移至 https://management.azure.com。 Azure 資料平面作業會移至您的服務實例,例如 https://myaccount.blob.core.windows.net/。 請參閱 Azure 控制平面和數據平面。 若要探索使用控制平面 URL 的作業,請參閱 Azure REST API。
差別表示鎖定可保護資源免於變更,但不會限制資源執行其功能的方式。 例如,SQL 資料庫 邏輯伺服器上的 ReadOnly 鎖定可保護它免於刪除或修改。 它可讓您在伺服器資料庫中建立、更新或刪除資料。 數據平面作業允許數據交易。 這些要求不會移至 https://management.azure.com。
套用鎖定前的考慮
套用鎖定可能會導致非預期的結果。 某些作業似乎未修改資源,需要封鎖的動作。 鎖定可防止 POST 方法將數據傳送至 Azure Resource Manager (ARM) API。 封鎖作業的一些常見範例如下:
儲存體帳戶的唯讀鎖定可防止使用者列出帳戶密鑰。 POST 要求會處理 Azure 儲存體 清單金鑰作業,以保護帳戶密鑰的存取權。 帳戶金鑰可讓您完整存取記憶體帳戶中的數據。 設定記憶體帳戶的唯讀鎖定時,沒有帳戶密鑰的使用者需要使用 Microsoft Entra 認證來存取 Blob 或佇列數據。 只讀鎖定也會防止將範圍設定為記憶體帳戶或數據容器(Blob 容器或佇列)的 Azure RBAC 角色指派。
記憶體帳戶的唯讀鎖定可保護針對記憶體帳戶或數據容器 (Blob 容器或佇列) 設定範圍的 RBAC 指派。
記憶體帳戶的唯讀鎖定可防止建立 Blob 容器。
儲存體帳戶上的只讀鎖定或無法刪除鎖定,並不會防止其數據遭到刪除或修改。 它也不會保護 Blob、佇列、數據表或檔案中的數據。
儲存體 帳戶 API 會公開數據平面和控制平面作業。 如果要求使用 數據平面 作業,記憶體帳戶上的鎖定不會保護該記憶體帳戶內的 Blob、佇列、數據表或檔案數據。 不過,如果要求使用 控制平面 作業,鎖定會保護這些資源。
例如,如果要求使用 檔案共享 - 刪除,這是控制平面作業,則刪除會失敗。 如果要求使用 刪除共用,這是數據平面作業,則刪除會成功。 建議您使用控制平面作業。
網路安全組 (NSG) 的唯讀鎖定可防止建立對應的NSG流量記錄。 網路安全組 (NSG) 上的無法刪除鎖定不會防止建立或修改對應的 NSG 流量記錄。
App Service 資源的唯讀鎖定可防止 Visual Studio Server Explorer 顯示資源的檔案,因為該互動需要寫入存取權。
包含 App Service 方案的資源群組唯讀鎖定可防止您相應增加或相應放大方案。
包含虛擬機的資源群組只讀鎖定可防止所有用戶啟動或重新啟動虛擬機。 這些作業需要POST方法要求。
資源群組的只讀鎖定可防止您將現有的資源移入或移出資源群組。
包含自動化帳戶的資源群組只讀鎖定可防止所有 Runbook 啟動。 這些作業需要POST方法要求。
無法刪除資源或資源群組的鎖定可防止刪除 Azure RBAC 指派。
資源群組上的無法刪除鎖定可防止 Azure Resource Manager 自動刪除歷程記錄中的部署。 如果您在歷程記錄中達到 800 個部署,您的部署就會失敗。
Azure 備份 服務所建立之資源群組的無法刪除鎖定會導致備份失敗。 服務最多支援18個還原點。 鎖定時,備份服務無法清除還原點。 如需詳細資訊,請參閱 備份 Azure VM 的常見問題。
包含 Azure 機器學習 工作區的資源群組無法刪除鎖定,可防止自動調整 Azure 機器學習 計算叢集無法正常運作。 使用鎖定時,自動調整無法移除未使用的節點。 您的解決方案會耗用比工作負載所需的資源更多。
Log Analytics 工作區的只讀鎖定可防止啟用使用者和實體行為分析 (UEBA)。
訂用帳戶的只讀鎖定可防止 Azure Advisor 正常運作。 Advisor 無法儲存其查詢的結果。
應用程式閘道 的唯讀鎖定可防止您取得應用程式閘道的後端健康情況。 該 作業會使用POST方法,這是唯讀鎖定區塊。
Azure Kubernetes Service (AKS) 叢集上的只讀鎖定會限制如何透過入口網站存取叢集資源。 只讀鎖定可防止您在 Azure 入口網站 中使用 AKS 叢集的 Kubernetes 資源一節來選擇叢集資源。 這些作業需要POST方法要求進行驗證。
Site Recovery 所保護之虛擬機上的無法刪除鎖定,可防止當您移除保護或停用複寫時,無法正確移除與 Site Recovery 相關的特定資源連結。 如果您打算稍後再次保護 VM,您需要先移除鎖定,再停用保護。 如果您未移除鎖定,您必須遵循特定步驟來清除過時的連結,才能保護 VM。 如需詳細資訊,請參閱 針對 Azure VM 複寫進行疑難解答。
誰可以建立或刪除鎖定
若要建立或刪除管理鎖定,您必須存取 Microsoft.Authorization/* 或 Microsoft.Authorization/locks/* 動作。 指派給擁有者和使用者存取 管理員 istrator 角色的使用者具有必要的存取權。 某些特製化的內建角色也會授與此存取權。 您可以建立具有必要權限的自訂角色。
受控應用程式和鎖定
某些 Azure 服務,例如 Azure Databricks,會使用 受控應用程式 來實作服務。 在此情況下,服務會建立兩個資源群組。 其中一個是包含服務概觀的解除鎖定資源群組。 另一個是包含服務基礎結構的鎖定資源群組。
如果您嘗試刪除基礎結構資源群組,您會收到錯誤,指出資源群組已鎖定。 如果您嘗試刪除基礎結構資源群組的鎖定,您會收到錯誤,指出因為系統應用程式擁有鎖定而無法刪除鎖定。
請改為刪除服務,這也會刪除基礎結構資源群組。
針對受控應用程式,選擇您部署的服務。
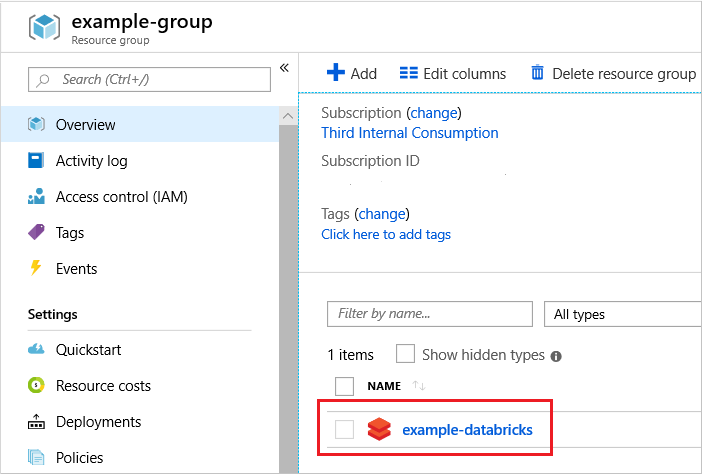
請注意,服務包含受控資源群組的連結。 該資源群組會保存基礎結構並已鎖定。 您只能間接刪除它。
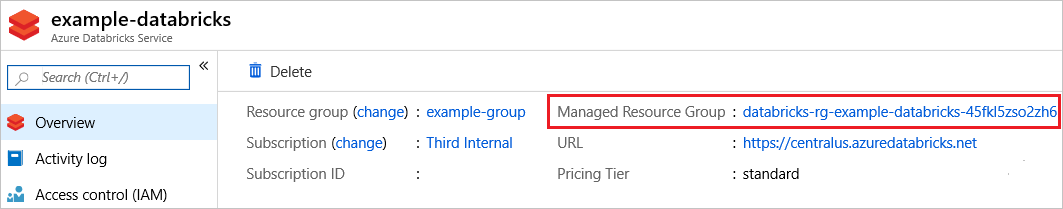
若要刪除服務的所有專案,包括鎖定的基礎結構資源群組,請選擇 服務的 [刪除 ]。

設定鎖定
入口網站
在左側導覽面板中,訂用帳戶鎖定功能的名稱是 [資源鎖定],而資源群組鎖定功能的名稱是 [鎖定]。
在您要鎖定之資源、資源群組或訂用帳戶的 [設定] 刀鋒視窗中,選取 [鎖定]。
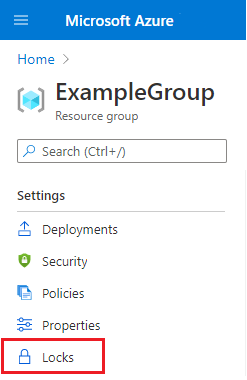
若要新增鎖定,選取 [新增]。 如果您想要在父層級建立鎖定,請選取父代。 目前選取的資源會繼承父系的鎖定。 例如,您可以鎖定資源群組,將鎖定套用至其所有資源。
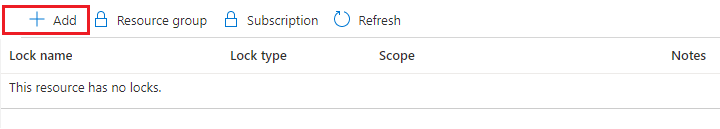
提供鎖定名稱和鎖定層級。 您可以視需要新增描述鎖定的附註。
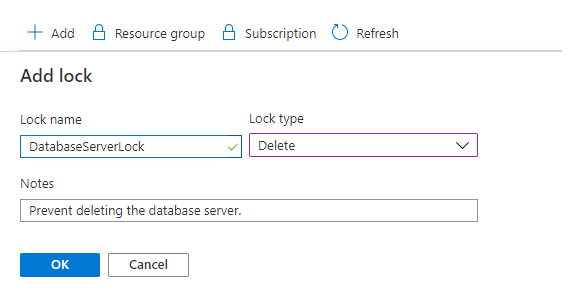
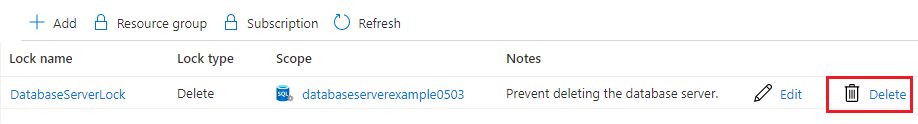
若要刪除鎖定,請選取 [刪除] 按鈕。
範本
使用ARM範本或 Bicep 檔案部署鎖定時,最好瞭解部署範圍和鎖定範圍如何一起運作。 若要在部署範圍套用鎖定,例如鎖定資源群組或訂用帳戶,請將 scope 屬性保持未設定。 鎖定資源時,在部署範圍內設定鎖定的範圍屬性。
下列範本會將鎖定套用至資源群組。 請注意,鎖定資源上沒有範圍屬性,因為鎖定範圍符合部署範圍。 在資源群組層級部署此範本。
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
},
"resources": [
{
"type": "Microsoft.Authorization/locks",
"apiVersion": "2016-09-01",
"name": "rgLock",
"properties": {
"level": "CanNotDelete",
"notes": "Resource group should not be deleted."
}
}
]
}
若要建立資源群組並加以鎖定,請在訂用帳戶層級部署下列範本。
{
"$schema": "https://schema.management.azure.com/schemas/2018-05-01/subscriptionDeploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"rgName": {
"type": "string"
},
"rgLocation": {
"type": "string"
}
},
"variables": {},
"resources": [
{
"type": "Microsoft.Resources/resourceGroups",
"apiVersion": "2021-04-01",
"name": "[parameters('rgName')]",
"location": "[parameters('rgLocation')]",
"properties": {}
},
{
"type": "Microsoft.Resources/deployments",
"apiVersion": "2021-04-01",
"name": "lockDeployment",
"resourceGroup": "[parameters('rgName')]",
"dependsOn": [
"[resourceId('Microsoft.Resources/resourceGroups/', parameters('rgName'))]"
],
"properties": {
"mode": "Incremental",
"template": {
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {},
"variables": {},
"resources": [
{
"type": "Microsoft.Authorization/locks",
"apiVersion": "2016-09-01",
"name": "rgLock",
"properties": {
"level": "CanNotDelete",
"notes": "Resource group and its resources should not be deleted."
}
}
],
"outputs": {}
}
}
}
],
"outputs": {}
}
將鎖定套用至 資源群組內的資源 時,請新增 scope 屬性。 將範圍設定為要鎖定的資源名稱。
下列範例示範建立App Service方案、網站和網站鎖定的範本。 鎖定的範圍會設定為網站。
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"hostingPlanName": {
"type": "string"
},
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]"
}
},
"variables": {
"siteName": "[concat('ExampleSite', uniqueString(resourceGroup().id))]"
},
"resources": [
{
"type": "Microsoft.Web/serverfarms",
"apiVersion": "2020-12-01",
"name": "[parameters('hostingPlanName')]",
"location": "[parameters('location')]",
"sku": {
"tier": "Free",
"name": "f1",
"capacity": 0
},
"properties": {
"targetWorkerCount": 1
}
},
{
"type": "Microsoft.Web/sites",
"apiVersion": "2020-12-01",
"name": "[variables('siteName')]",
"location": "[parameters('location')]",
"dependsOn": [
"[resourceId('Microsoft.Web/serverfarms', parameters('hostingPlanName'))]"
],
"properties": {
"serverFarmId": "[parameters('hostingPlanName')]"
}
},
{
"type": "Microsoft.Authorization/locks",
"apiVersion": "2016-09-01",
"name": "siteLock",
"scope": "[concat('Microsoft.Web/sites/', variables('siteName'))]",
"dependsOn": [
"[resourceId('Microsoft.Web/sites', variables('siteName'))]"
],
"properties": {
"level": "CanNotDelete",
"notes": "Site should not be deleted."
}
}
]
}
Azure PowerShell
您可以使用 New-AzResourceLock 命令,使用 Azure PowerShell 鎖定已部署的資源。
若要鎖定資源,請提供資源的名稱、其資源類型和資源組名。
New-AzResourceLock -LockLevel CanNotDelete -LockName LockSite -ResourceName examplesite -ResourceType Microsoft.Web/sites -ResourceGroupName exampleresourcegroup
若要鎖定資源群組,請提供資源群組的名稱。
New-AzResourceLock -LockName LockGroup -LockLevel CanNotDelete -ResourceGroupName exampleresourcegroup
若要取得鎖定的相關信息,請使用 Get-AzResourceLock。 若要取得訂用帳戶中的所有鎖定,請使用:
Get-AzResourceLock
若要取得資源的所有鎖定,請使用:
Get-AzResourceLock -ResourceName examplesite -ResourceType Microsoft.Web/sites -ResourceGroupName exampleresourcegroup
若要取得資源群組的所有鎖定,請使用:
Get-AzResourceLock -ResourceGroupName exampleresourcegroup
若要刪除資源的鎖定,請使用:
$lockId = (Get-AzResourceLock -ResourceGroupName exampleresourcegroup -ResourceName examplesite -ResourceType Microsoft.Web/sites).LockId
Remove-AzResourceLock -LockId $lockId
若要刪除資源群組的鎖定,請使用:
$lockId = (Get-AzResourceLock -ResourceGroupName exampleresourcegroup).LockId
Remove-AzResourceLock -LockId $lockId
Azure CLI
您可以使用 az lock create 命令,使用 Azure CLI 鎖定已部署的資源。
若要鎖定資源,請提供資源的名稱、其資源類型和資源組名。
az lock create --name LockSite --lock-type CanNotDelete --resource-group exampleresourcegroup --resource-name examplesite --resource-type Microsoft.Web/sites
若要鎖定資源群組,請提供資源群組的名稱。
az lock create --name LockGroup --lock-type CanNotDelete --resource-group exampleresourcegroup
若要取得鎖定的相關信息,請使用 az lock list。 若要取得訂用帳戶中的所有鎖定,請使用:
az lock list
若要取得資源的所有鎖定,請使用:
az lock list --resource-group exampleresourcegroup --resource-name examplesite --namespace Microsoft.Web --resource-type sites --parent ""
若要取得資源群組的所有鎖定,請使用:
az lock list --resource-group exampleresourcegroup
若要刪除資源的鎖定,請使用:
lockid=$(az lock show --name LockSite --resource-group exampleresourcegroup --resource-type Microsoft.Web/sites --resource-name examplesite --output tsv --query id)
az lock delete --ids $lockid
若要刪除資源群組的鎖定,請使用:
lockid=$(az lock show --name LockSite --resource-group exampleresourcegroup --output tsv --query id)
az lock delete --ids $lockid
Python
您可以使用 ManagementLockClient.management_locks.create_or_update_at_resource_group_level 命令鎖定已部署的資源。
若要鎖定資源,請提供資源的名稱、其資源類型和資源組名。
import os
from azure.identity import AzureCliCredential
from azure.mgmt.resource import ManagementLockClient
credential = AzureCliCredential()
subscription_id = os.environ["AZURE_SUBSCRIPTION_ID"]
lock_client = ManagementLockClient(credential, subscription_id)
lock_result = lock_client.management_locks.create_or_update_at_resource_level(
"exampleGroup",
"Microsoft.Web",
"",
"sites",
"examplesite",
"lockSite",
{
"level": "CanNotDelete"
}
)
若要鎖定資源群組,請提供資源群組的名稱。
import os
from azure.identity import AzureCliCredential
from azure.mgmt.resource import ManagementLockClient
credential = AzureCliCredential()
subscription_id = os.environ["AZURE_SUBSCRIPTION_ID"]
lock_client = ManagementLockClient(credential, subscription_id)
lock_result = lock_client.management_locks.create_or_update_at_resource_group_level(
"exampleGroup",
"lockGroup",
{
"level": "CanNotDelete"
}
)
若要取得訂用帳戶中所有鎖定的相關信息,請使用 ManagementLockClient.management_locks.get。 若要取得訂用帳戶中的所有鎖定,請使用:
import os
from azure.identity import AzureCliCredential
from azure.mgmt.resource import ManagementLockClient
credential = AzureCliCredential()
subscription_id = os.environ["AZURE_SUBSCRIPTION_ID"]
lock_client = ManagementLockClient(credential, subscription_id)
lock_result = lock_client.management_locks.list_at_subscription_level()
for lock in lock_result:
print(f"Lock name: {lock.name}")
print(f"Lock level: {lock.level}")
print(f"Lock notes: {lock.notes}")
若要取得資源的鎖定,請使用:
import os
from azure.identity import AzureCliCredential
from azure.mgmt.resource import ManagementLockClient
credential = AzureCliCredential()
subscription_id = os.environ["AZURE_SUBSCRIPTION_ID"]
lock_client = ManagementLockClient(credential, subscription_id)
lock_result = lock_client.management_locks.get_at_resource_level(
"exampleGroup",
"Microsoft.Web",
"",
"sites",
"examplesite",
"lockSite"
)
print(f"Lock ID: {lock_result.id}")
print(f"Lock Name: {lock_result.name}")
print(f"Lock Level: {lock_result.level}")
若要取得資源群組的鎖定,請使用:
import os
from azure.identity import AzureCliCredential
from azure.mgmt.resource import ManagementLockClient
credential = AzureCliCredential()
subscription_id = os.environ["AZURE_SUBSCRIPTION_ID"]
lock_client = ManagementLockClient(credential, subscription_id)
lock_result = lock_client.management_locks.get_at_resource_group_level(
"exampleGroup",
"lockGroup"
)
print(f"Lock ID: {lock_result.id}")
print(f"Lock Level: {lock_result.level}")
若要刪除資源的鎖定,請使用:
import os
from azure.identity import AzureCliCredential
from azure.mgmt.resource import ManagementLockClient
credential = AzureCliCredential()
subscription_id = os.environ["AZURE_SUBSCRIPTION_ID"]
lock_client = ManagementLockClient(credential, subscription_id)
lock_client.management_locks.delete_at_resource_level(
"exampleGroup",
"Microsoft.Web",
"",
"sites",
"examplesite",
"lockSite"
)
若要刪除資源群組的鎖定,請使用:
import os
from azure.identity import AzureCliCredential
from azure.mgmt.resource import ManagementLockClient
credential = AzureCliCredential()
subscription_id = os.environ["AZURE_SUBSCRIPTION_ID"]
lock_client = ManagementLockClient(credential, subscription_id)
lock_client.management_locks.delete_at_resource_group_level("exampleGroup", "lockGroup")
REST API
您可以使用 REST API 來鎖定已部署的資源 ,以進行管理鎖定。 REST API 可讓您建立和刪除鎖定,並擷取現有鎖定的相關信息。
若要建立鎖定,請執行:
PUT https://management.azure.com/{scope}/providers/Microsoft.Authorization/locks/{lock-name}?api-version={api-version}
範圍可以是訂用帳戶、資源群組或資源。 鎖定名稱可以是您想要呼叫的任何名稱。 針對 API 版本,請使用 2016-09-01。
在要求中,包含指定鎖定屬性的 JSON 物件。
{
"properties": {
"level": "CanNotDelete",
"notes": "Optional text notes."
}
}
下一步
- 若要瞭解以邏輯方式組織您的資源,請參閱 使用標籤來組織您的資源。
- 您可以使用自定義原則,在訂用帳戶中套用限制和慣例。 如需詳細資訊,請參閱什麼是 Azure 原則?。
- 如需關於企業如何使用 Resource Manager 有效地管理訂用帳戶的指引,請參閱 Azure 企業 Scaffold - 規定的訂用帳戶治理。