將您的應用程式連線到 Azure SQL 受控執行個體
適用於:Azure SQL 受控執行個體
本文描述如何在許多不同的應用程式案例中,在 Azure 虛擬網路內部或之間將應用程式連線至 Azure SQL 受控執行個體。
您在決定如何及何處裝載應用程式時,目前有多個選擇。 您可以選擇使用 Azure App Service 或 Azure 的一些虛擬網路整合式選項 (例如 Azure App Service 環境、Azure 虛擬機器及虛擬機器擴展集),在雲端裝載應用程式。 您也可以採用混合式 (「混合」) 雲端方法,將您的應用程式留在內部部署環境。 無論您的選擇是什麼,在許多不同的應用程式案例中,您的應用程式都可以在 Azure 虛擬網路內部或之間連線至 Azure SQL 受控執行個體。
您也可以從虛擬網路外部啟用對受控執行個體的資料存取,例如,從 Power BI 和 Azure App Service 等多租用戶 Azure 服務,或從未透過 VPN 連線到虛擬網路的內部部署網路存取。 若要完成這些和類似的案例,請參閱在 Azure SQL 受控執行個體中設定公用端點。
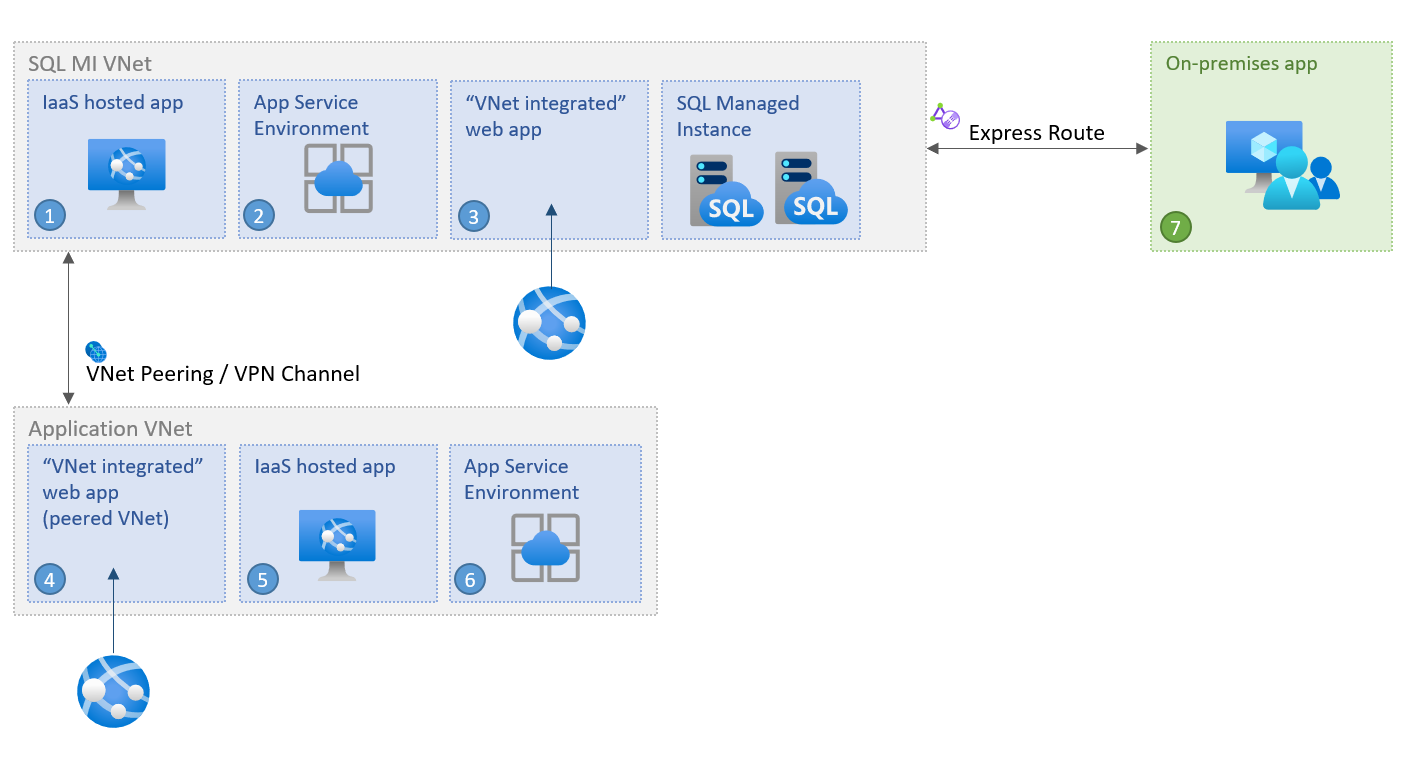
從相同的 VNet 內連線
將同一個虛擬網路內的應用程式當作 SQL 受控執行個體來連線是最簡單的案例。 虛擬網路內的虛擬機器即使位於不同的子網路,彼此也可以直接連線。 這表示若要在 App Service 環境或與 SQL 受控執行個體部署在相同虛擬網路中的虛擬機器內部連線應用程式,則需要設定連接字串,以其 VNet 本機端點為目標。
從不同的 VNet 內連線
當應用程式位於與 SQL 受控執行個體不同的虛擬網路時,連線應用程式必須先存取部署 SQL 受控執行個體的虛擬網路,或 SQL 受控執行個體本身。 兩個虛擬網路不一定要在相同的訂用帳戶中。
有三個選項可連線到不同虛擬網路中的 SQL 受控執行個體:
- 私人端點
- Azure 對等互連
- VNet 對 VNet VPN 閘道 (Azure 入口網站、PowerShell、Azure CLI)
在這三個選項中,私人端點是最安全且最具資源經濟效益的選項,因為它們:
- 僅會從其虛擬網路公開 SQL 受控執行個體。
- 僅允許單向連線。
- 僅需要應用程式虛擬網路中的一個 IP 位址。
如果私人端點無法完全符合您案例的需求,請考慮改用虛擬網路對等互連。 對等互連會使用骨幹 Azure 網路,因此跨虛擬網路界限的通訊不會有明顯的延遲懲罰。 在所有區域的網路之間支援虛擬網路對等互連 (全域虛擬網路對等互連),而在 2020 年 9 月 22 日前建立的子網路中託管的執行個體僅支援其區域內的對等互連。
從內部部署連線
您可以將內部部署應用程式連線至 SQL 受控執行個體的 VNet 本機端點。 若要從內部部署環境加以存取,您需要進行應用程式與 SQL 受控執行個體虛擬網路之間的站對站連線。 如果僅存取受控執行個體的資料已足夠,則您可以透過公用端點從虛擬網路外部進行連線;若要深入了解,請檢閱在 Azure SQL 受控執行個體中設定公用端點中設定公用端點。
您可以透過兩個選項連線內部部署與 Azure 虛擬網路:
- 站對站 VPN 連線 (Azure 入口網站、PowerShell、Azure CLI)
- Azure ExpressRoute 連線
如果您已建立內部部署與 Azure 的連線,但是無法建立與 SQL 受控執行個體的連線,請檢查開啟 SQL 連接埠 1433 和範圍 11000-11999 連接埠的輸出連線,以便重新導向。
連線開發人員方塊
您也可以將開發人員方塊連線至 SQL 受控執行個體。 若要透過虛擬網路從開發人員方塊進行存取,您必須先建立開發人員方塊與 SQL 受控執行個體虛擬網路之間的連線。 若要這麼做,請使用原生 Azure 憑證驗證設定虛擬網路的點對站連線。 如需詳細資訊,請參閱設定點對站連線以從內部部署電腦連線到 Azure SQL 受控執行個體。
若要從虛擬網路外部存取受控執行個體的資料,請參閱在 Azure SQL 受控執行個體中設定公用端點。
連線至輪輻網路
另一個常見案例是:VPN 閘道安裝在與託管 SQL 受控執行個體的虛擬網路 (中樞網路) 不同的虛擬網路 (也可能是訂用帳戶) - 輪幅網路中。 從輪輻網路 SQL 受控執行個體連線,是透過從不同的 VNet 內連線中列出的其中一個選項來設定:私人端點、VNet 對等互連或 VNet 對 VNet 閘道。
下列範例結構圖顯示 VNet 對等互連:
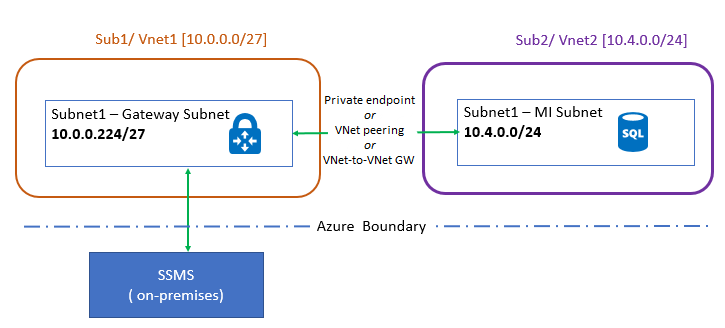
如果是對等互連中樞和輪輻網路,請確定 VPN 閘道會看到來自中樞網路的 IP 位址。 若要這麼做,請在 [對等互連設定] 下方進行下列變更:
- 在託管 VPN 閘道的虛擬網路 (輪輻網路) 中,前往 [對等互連]、移至 SQL 受控執行個體的對等互連虛擬網路連線,然後選取 [允許閘道傳輸]。
- 在託管 SQL 受控執行個體的虛擬網路 (中樞網路) 中,前往 [對等互連]、移至 VPN 閘道的對等互連虛擬網路連線,並選取 [使用遠端閘道]。
連線 Azure App Service
您也可以在與虛擬網路整合時,連接由 Azure App Service 託管的應用程式。 為此,請選取在從不同的 VNet 內連線中列出的其中一個機制。 若要從虛擬網路外部存取受控執行個體的資料,請參閱在 Azure SQL 受控執行個體中設定公用端點。
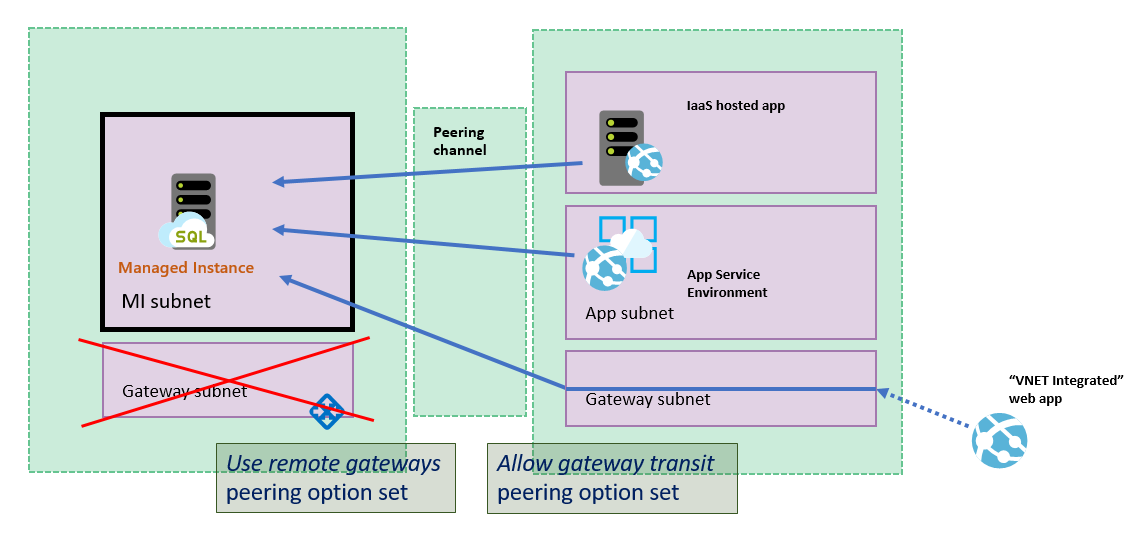
將 Azure App Service 連線至 SQL 受控執行個體的特殊案例是:將 Azure App Service 與對等互連至 SQL 受控執行個體虛擬網路的網路整合後。 這種情況下需要設定下列組態:
- SQL 受控執行個體虛擬網路不得有閘道
- SQL 受控執行個體虛擬網路必須設定
Use remote gateways選項 - 對等互連虛擬網路必須設定
Allow gateway transit選項
下圖說明此案例:
注意
虛擬網路整合功能不會整合應用程式與具有 ExpressRoute 閘道的虛擬網路。 即使是在共存模式中設定 ExpressRoute 閘道,虛擬網路整合仍無法運作。 如果需要透過 ExpressRoute 連線存取資源,您可以使用在虛擬網路中執行的 App Service 環境。
若要針對透過虛擬網路的 Azure App Service 存取進行疑難排解,請參閱針對虛擬網路和應用程式進行疑難排解。
針對連線能力問題進行疑難排解
若要對連線問題進行疑難排解,請檢閱以下幾點:
如果您無法從相同虛擬網路但不同子網路中的 Azure 虛擬機器連線至 SQL 受控執行個體,請檢查您在 VM 子網路上設定的網路安全性群組是否可能封鎖存取。 此外,請開啟 SQL 連接埠 1433 和範圍 11000-11999 連接埠的輸出連線,因為在 Azure 界限內透過重新導向連線時需要這些連接埠。
針對與虛擬網路建立關聯的路由表,確定已停用閘道路由的傳播。
如果使用點對站 VPN,請檢查 Azure 入口網站中的組態,以確認您是否看到輸入/輸出數值。 非零的數值表示 Azure 會將流量路由至內部部署,或從中輸出流量。
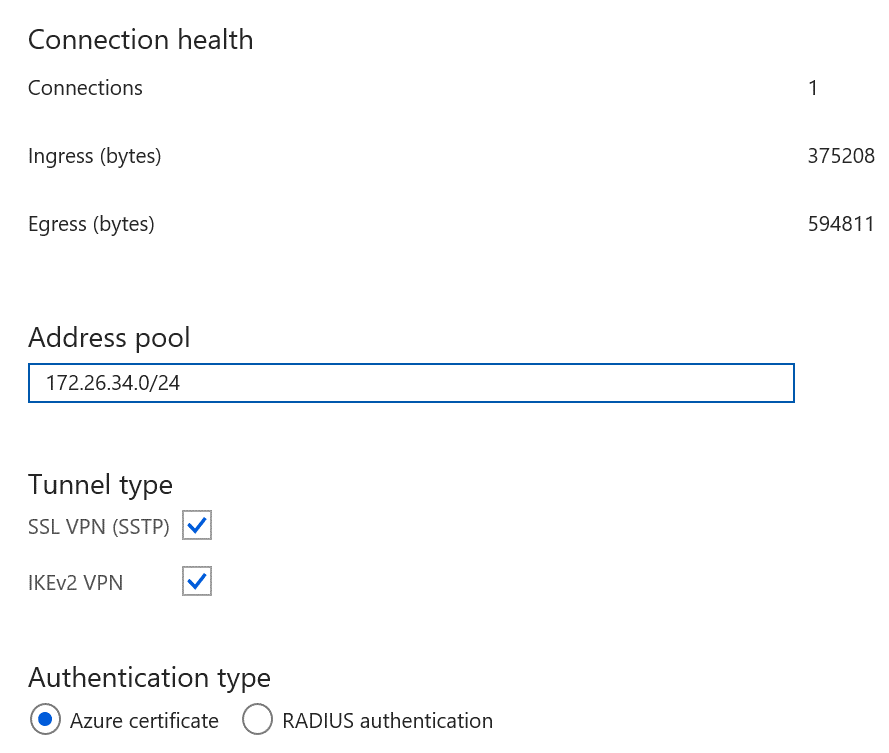
確認用戶端電腦 (執行 VPN 用戶端的電腦) 具有您需要存取之所有虛擬網路的路由入口。 路由會儲存在
%AppData%\Roaming\Microsoft\Network\Connections\Cm\<GUID>\routes.txt.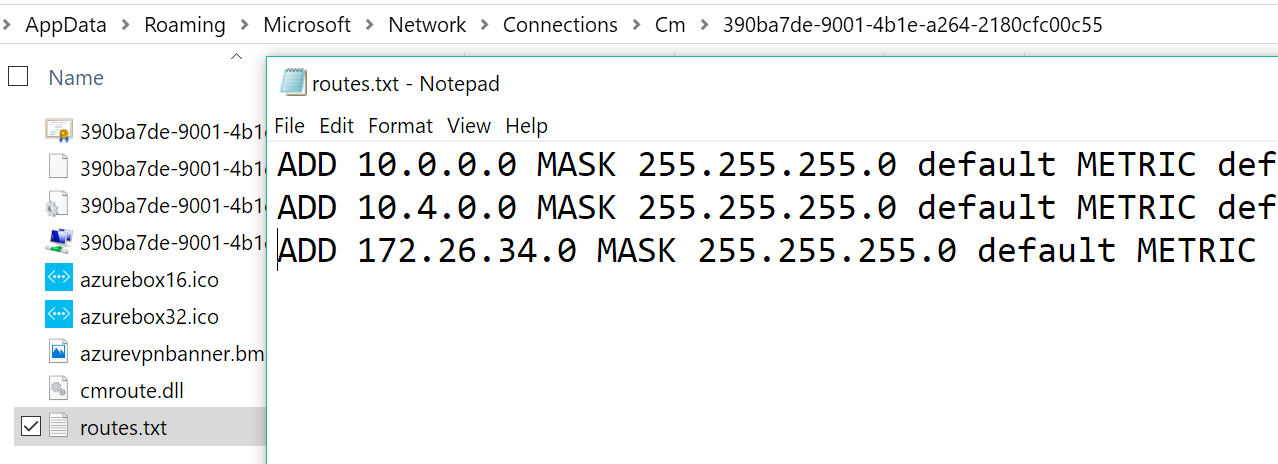
如圖所示,每個相關的虛擬網路都有兩個入口,而在入口網站中設定的 VPN 端點會有第三個入口。
除此之外,也可以透過下列命令來檢查路由。 下列輸出顯示各種子網路的路由:
C:\ >route print -4 =========================================================================== Interface List 14...54 ee 75 67 6b 39 ......Intel(R) Ethernet Connection (3) I218-LM 57...........................rndatavnet 18...94 65 9c 7d e5 ce ......Intel(R) Dual Band Wireless-AC 7265 1...........................Software Loopback Interface 1 Adapter=========================================================================== IPv4 Route Table =========================================================================== Active Routes: Network Destination Netmask Gateway Interface Metric 0.0.0.0 0.0.0.0 10.83.72.1 10.83.74.112 35 10.0.0.0 255.255.255.0 On-link 172.26.34.2 43 10.4.0.0 255.255.255.0 On-link 172.26.34.2 43 =========================================================================== Persistent Routes: None如果使用虛擬網路對等互連,請確認已依照允許閘道傳輸和使用遠端閘道的設定指示操作。
如果您正在使用虛擬網路對等互連來連線 Azure App Service 裝載的應用程式,且 SQL 受控執行個體虛擬網路具有公用 IP 位址範圍,請確認裝載的應用程式設定允許將輸出流量路由傳送至公用 IP 網路。 請遵循區域虛擬網路整合中的指示。
建議的驅動程式和工具版本
雖然較舊版本可能會運作,但下表列出了建議的工具和驅動程式最低版本,以連線到 SQL 受控執行個體:
| 驅動程式/工具 | 版本 |
|---|---|
| .NET Framework | 4.6.1 (或 .NET Core) |
| ODBC 驅動程式 | v17 |
| PHP 驅動程式 | 5.2.0 |
| JDBC 驅動程式 | 6.4.0 |
| Node.js 驅動程式 | 2.1.1 |
| OLEDB 驅動程式 | 18.0.2.0 |
| SSMS | 18.0 或 更高版本 |
| SMO | 150 或更高版本 |
後續步驟
- 如需 SQL 受控執行個體的資訊,請參閱什麼是 SQL 受控執行個體?。
- 如需示範如何新建受控執行個體的教學課程,請參閱建立受控執行個體。
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應