安裝和設定 Microsoft Rights Management 連接器
使用下列資訊可協助您安裝和設定 Microsoft Rights Management (RMS) 連接器。 這些程序涵蓋部署 Microsoft Rights Management 連接器的步驟 1 到 4。
在開始之前:
請確定您已檢閱並檢查 此部署的必要條件 。
請確定您知道 連接器的正確 Azure 主權雲端實例 ,才能完成設定和設定。
安裝 RMS 連接器
識別執行 RMS 連接器的電腦(至少兩部)。 這些計算機必須符合必要條件中列出的最低規格。
注意
安裝單一 RMS 連接器(由多部伺服器組成以取得高可用性),每個租使用者(Microsoft 365 租使用者或 Microsoft Entra 租使用者)。 不同於 Active Directory RMS,您不需要在每個樹系中安裝 RMS 連接器。
從 Microsoft 下載中心下載 RMS 連接器的來源檔案。
若要安裝 RMS 連接器,請下載 RMS 連線 orSetup.exe。
此外,如果您想要使用 RMS 連接器的伺服器組態工具,將內部部署伺服器上的登錄設定設定自動化,也請下載 Gen 連線 orConfig.ps1。
在您要安裝 RMS 連接器的電腦上,以系統管理員許可權執行 RMS 連線 orSetup.exe。
在 Microsoft Rights Management 連線 or 安裝程式的 [歡迎] 頁面上,選取 [在計算機上安裝 Microsoft Rights Management 連接器],然後按 [下一步]。
閱讀並接受最終使用者許可協定條款,然後按 [ 下一步]。
在 [ 驗證] 頁面中,選取符合您解決方案的雲端環境。 例如,針對 Azure 商業供應項目選取 [AzureCloud ]。 否則,請選取下列其中一個選項:
- AzureChinaCloud:由 21Vianet 運作的 Azure
- AzureUSGovernment:Azure Government (GCC High/DoD)
- AzureUSGovernment2:Azure Government 2
- AzureUSGovernment3:Azure Government 3
選取 [登入 ] 以登入您的帳戶。 請確定您輸入具有足夠許可權的帳戶認證來設定 RMS 連接器。
您可以使用具有下列其中一個權限的帳戶:
租使用者的全域管理員:帳戶是 Microsoft 365 租使用者或 Microsoft Entra 租使用者的全域管理員。
Azure Rights Management 全域管理員:已獲指派 Azure RMS 全域管理員角色的 Microsoft Entra 標識符中的帳戶。
Azure Rights Management 連接器系統管理員:Microsoft Entra 標識符中的帳戶,已獲授與安裝及管理貴組織的 RMS 連接器許可權。
Azure Rights Management 全域管理員角色和 Azure Rights Management 連接器系統管理員角色會使用 Add-AipServiceRoleBased 管理員 istrator Cmdlet 指派給帳戶。
注意
如果您已實 作上線控件,請確定您指定的帳戶能夠保護內容。
例如,如果您將保護內容的能力限制為「IT 部門」群組,您在此處指定的帳戶必須是該群組的成員。 如果沒有,您會看到錯誤訊息: 嘗試探索管理服務和組織的位置失敗。請確定您的組織已啟用 Microsoft Rights Management 服務。
提示
若要以最低許可權執行 RMS 連接器,請為此建立專用帳戶,然後指派 Azure RMS 連接器系統管理員角色。 如需詳細資訊,請參閱 建立 RMS 連接器的專用帳戶。
在精靈的最後一個頁面上,執行下列動作,然後按兩下 [ 完成]:
如果這是您安裝的第一個連接器,請勿選取 [ 啟動連接器系統管理員主控台] 來授權伺服器 。 安裝第二個(或最終)RMS 連接器之後,您將選取此選項。 相反地,請在至少一部其他計算機上再次執行精靈。 您必須至少安裝兩個連接器。
如果您已安裝第二個(或最終)連接器,請選取 [啟動連接器系統管理員控制台] 以授權伺服器。
在 RMS 連接器安裝程式期間,所有必要條件軟體都會經過驗證並安裝,如果尚未安裝,則會安裝 網際網路資訊服務 (IIS),並安裝並設定連接器軟體。 Azure RMS 也會藉由建立下列專案來準備進行設定:
授權使用連接器與 Azure RMS 通訊的伺服器 空白資料表。 稍後將伺服器 新增至此數據表。
連接器的一組安全性令牌 ,可授權 Azure RMS 的作業。 這些令牌會從 Azure RMS 下載,並安裝在登錄中的本機電腦上。 它們會使用資料保護應用程式開發介面 (DPAPI) 和本機系統帳戶認證來保護它們。
建立 RMS 連接器的專用帳戶
此程序說明如何建立專用帳戶,以盡可能具備最低許可權來執行 Azure RMS 連接器,以在 RMS 連接器安裝期間登入時使用。
如果您尚未這麼做,請下載並安裝 AIPService PowerShell 模組。 如需詳細資訊,請參閱 安裝 AIPService PowerShell 模組。
使用 [以系統管理員身分執行] 命令啟動 Windows PowerShell,並使用 連線-AipService 命令連線到保護服務:
Connect-AipService //provide Microsoft 365 tenant administratoror Azure RMS global administrator credentials使用下列其中一個參數,執行 Add-AipServiceRoleBased 管理員 istrator 命令:
Add-AipServiceRoleBasedAdministrator -EmailAddress <email address> -Role"ConnectorAdministrator"Add-AipServiceRoleBasedAdministrator -ObjectId <object id> -Role"ConnectorAdministrator"Add-AipServiceRoleBasedAdministrator -SecurityGroupDisplayName <group Name> -Role"ConnectorAdministrator"例如,執行:
Add-AipServiceRoleBasedAdministrator -EmailAddressmelisa@contoso.com -Role "ConnectorAdministrator"
雖然這些命令會指派連接器系統管理員角色,但您也可以改用 Global 管理員 istrator 角色。
確認安裝
若要確認 RMS 連接器的 Web 服務是否正常運作:
從網頁瀏覽器連線到 http:// connectoraddress>/_wmcs/certification/servercertification.asmx,將 <connectoraddress> 取代為已安裝 RMS 連接器的伺服器位址或<名稱。
成功的聯機會顯示 ServerCertificationWebService 頁面。
若要確認使用者讀取或修改 RMS 或 AIP 保護的檔案的能力:
在 RMS 連接器電腦上,開啟 事件檢視器 並移至應用程式 Windows 記錄檔。 使用 [資訊層級] 從 Microsoft RMS 連線 or 來源尋找專案。
項目應該會有類似下列的訊息:
The list of authorized accounts has been updated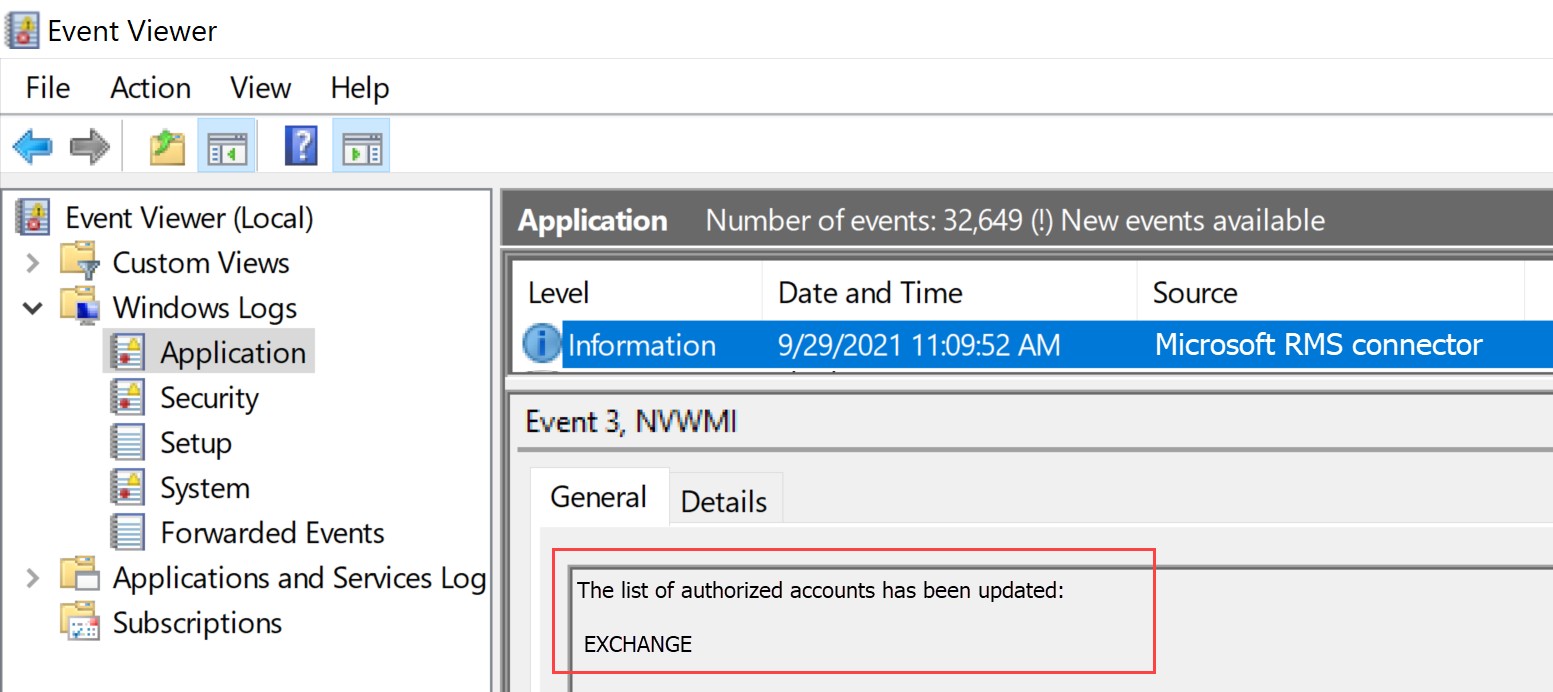
如果您需要卸載 RMS 連接器,請透過系統設定頁面卸載,或再次執行精靈並選取卸載選項。
如果您在安裝期間遇到任何問題,請檢查安裝記錄檔: %LocalAppData%\Temp\Microsoft Rights Management connector_<date 和 time.log>
例如,您的安裝記錄檔看起來可能類似 C:\Users\管理員 istrator\AppData\Local\Temp\Microsoft Rights Management connector_20170803110352.log
授權伺服器使用 RMS 連接器
當您在至少兩部電腦上安裝 RMS 連接器時,即可授權您想要使用 RMS 連接器的伺服器和服務。 例如,執行 Exchange Server 2013 或 SharePoint Server 2013 的伺服器。
若要定義這些伺服器,請執行 RMS 連接器管理工具,並將專案新增至允許的伺服器清單。 當您選取 [ 啟動連接器管理控制台] 來授權 Microsoft Rights Management 連接器安裝精靈結尾的伺服器時,您可以執行此工具,也可以與精靈分開執行。
當您授權這些伺服器時,請注意下列考慮:
您新增的伺服器會被授與特殊許可權。 您在連接器組態中為 Exchange Server 角色指定的所有帳戶都會獲得 Azure RMS 中的進階使用者角色 ,這可讓他們存取此 RMS 租使用者的所有內容。 如有必要,此時會自動啟用進階使用者功能。 若要避免提高許可權的安全性風險,請小心只指定貴組織的 Exchange 伺服器所使用的帳戶。 所有設定為 SharePoint 伺服器或使用 FCI 的檔案伺服器都會獲得一般用戶許可權。
您可以藉由指定 Active Directory 安全性或通訊群組,或多個伺服器所使用的服務帳戶,將多部伺服器新增為單一專案 。 當您使用此組態時,伺服器群組會共用相同的 RMS 憑證,而且全都被視為其中任何一個受保護內容的擁有者。 若要將系統管理額外負荷降到最低,建議您使用此單一群組的組態,而不是個別伺服器來授權組織的 Exchange 伺服器或 SharePoint 伺服器數位。
在 [允許使用連接器 的伺服器] 頁面上,選取 [ 新增]。
注意
授權伺服器相當於 Azure RMS 中的對等設定,相當於將 NTFS 許可權手動套用至 服務或伺服器電腦帳戶的 ServerCertification.asmx 的 AD RMS 設定,並手動將使用者進階許可權授與 Exchange 帳戶。 連接器上不需要將NTFS許可權套用至 ServerCertification.asmx 。
將伺服器新增至允許的伺服器清單
在 [ 允許伺服器利用連接器 ] 頁面上,輸入對象的名稱,或瀏覽以識別要授權的物件。
請務必授權正確的物件。 若要讓伺服器使用連接器,必須選取執行內部部署服務(例如 Exchange 或 SharePoint)的帳戶進行授權。 例如,如果服務是以已設定的服務帳戶執行,請將該服務帳戶的名稱新增至清單。 如果服務以本機系統的形式執行,請新增計算機對象的名稱(例如 SERVERNAME$)。 最佳做法是建立包含這些帳戶的群組,並指定群組而非個別伺服器名稱。
不同伺服器角色的詳細資訊:
對於執行 Exchange 的伺服器:您必須指定安全組,而且您可以使用 Exchange 自動建立和維護樹系中所有 Exchange 伺服器的預設群組(Exchange Server)。
針對執行 SharePoint 的伺服器:
如果 SharePoint 2010 伺服器設定為以本機系統執行(它不使用服務帳戶),請在 Active Directory 網域服務 中手動建立安全組,並將此組態中伺服器的計算機名稱物件新增至此群組。
如果 SharePoint 伺服器設定為使用服務帳戶(SharePoint 2010 的建議做法,以及 SharePoint 2016 和 SharePoint 2013 的唯一選項),請執行下列動作:
新增執行 SharePoint Central 管理員 istration 服務的服務帳戶,以從其系統管理員控制台設定 SharePoint。
新增針對 SharePoint 應用程式集區設定的帳戶。
提示
如果這兩個帳戶不同,請考慮建立包含這兩個帳戶的單一群組,以將系統管理額外負荷降到最低。
對於使用檔案分類基礎結構的檔伺服器,相關聯的服務會以本機系統帳戶的形式執行,因此您必須授權檔伺服器的計算機帳戶(例如 SERVERNAME$)或包含這些計算機帳戶的群組。
當您完成將伺服器新增至清單時,請按兩下 [ 關閉]。
如果您尚未這麼做,您現在必須針對已安裝 RMS 連接器的伺服器設定負載平衡,並考慮是否要針對這些伺服器與剛剛授權的伺服器之間的連線使用 HTTPS。
設定負載平衡和高可用性
安裝 RMS 連接器的第二個或最後一個實例之後,請定義連接器 URL 伺服器名稱並設定負載平衡系統。
連接器 URL 伺服器名稱可以是您控制之命名空間下的任何名稱。 例如,您可以在 DNS 系統中為 rmsconnector.contoso.com 建立專案,並將這個項目設定為在負載平衡系統中使用 IP 位址。 此名稱沒有特殊需求,而且不需要在連接器伺服器上自行設定。 除非您的 Exchange 和 SharePoint 伺服器要透過因特網與連接器通訊,否則此名稱不需要在因特網上解析。
重要
建議您在將 Exchange 或 SharePoint 伺服器設定為使用連接器之後,不要變更此名稱,因為您必須清除所有 IRM 組態的這些伺服器,然後重新設定它們。
在 DNS 中建立名稱並設定為 IP 位址之後,請設定該位址的負載平衡,以將流量導向連接器伺服器。 您可以針對此目的使用任何IP型負載平衡器,其中包括Windows Server中的網路負載平衡 (NLB) 功能。 如需詳細資訊,請參閱 負載平衡部署指南。
使用下列設定來設定 NLB 叢集:
埠:80(適用於 HTTP)或 443(適用於 HTTPS)
如需是否要使用 HTTP 或 HTTPS 的詳細資訊,請參閱下一節。
親和性:無
散發方法:等於
您為負載平衡系統定義的這個名稱(針對執行 RMS 連接器服務的伺服器)是組織稍後使用的 RMS 連接器名稱,當您設定內部部署伺服器以使用 Azure RMS 時。
設定 RMS 連接器以使用 HTTPS
注意
此設定步驟是選擇性的,但建議用於其他安全性。
雖然 RMS 連接器使用 TLS 或 SSL 是選擇性的,但建議針對任何 HTTP 型安全性敏感性服務使用 TLS 或 SSL。 此組態會向使用連接器的 Exchange 和 SharePoint 伺服器驗證執行連接器的伺服器。 此外,從這些伺服器傳送到連接器的所有數據都會加密。
若要讓 RMS 連接器能夠使用 TLS,請在執行 RMS 連接器的每個伺服器上,安裝包含您用於連接器之名稱的伺服器驗證憑證。 例如,如果您在 DNS 中定義的 RMS 連接器名稱是 rmsconnector.contoso.com,請將包含 憑證主體中 rmsconnector.contoso.com 的伺服器驗證憑證部署為一般名稱。 或者,將憑證別名中的 rmsconnector.contoso.com 指定為 DNS 值。 憑證不需要包含伺服器的名稱。 然後在 IIS 中,將此憑證系結至默認網站。
如果您使用 HTTPS 選項,請確定執行連接器的所有伺服器都有有效的伺服器驗證憑證,其鏈結至 Exchange 和 SharePoint 伺服器信任的根 CA。 此外,如果發行連接器伺服器的憑證的證書頒發機構單位 (CA) 發佈證書吊銷清單 (CRL),Exchange 和 SharePoint 伺服器必須能夠下載此 CRL。
提示
您可以使用下列資訊和資源來協助您要求及安裝伺服器驗證憑證,並將此憑證系結至 IIS 中的預設網站:
如果您使用 Active Directory 憑證服務 (AD CS) 和企業證書頒發機構單位 (CA) 來部署這些伺服器驗證憑證,則可以複製並使用網頁伺服器證書範本。 此證書範本會使用 憑證主體名稱要求中提供的 ,這表示當您要求 憑證的憑證主體名稱或主體別名時,您可以提供 RMS 連接器名稱的 FQDN。
如果您使用獨立 CA 或從另一家公司購買此憑證,請參閱 TechNet 上的網頁伺服器文檔庫中的設定因特網伺服器憑證 (IIS 7)。
若要將 IIS 設定為使用憑證,請參閱 TechNet 上的網頁伺服器 (IIS)文檔庫中的將系結新增至網站 (IIS 7)。
設定 Web Proxy 伺服器的 RMS 連接器
如果您的連接器伺服器安裝在沒有直接因特網連線的網路中,而且需要手動設定 Web Proxy 伺服器以進行輸出因特網存取,您必須在這些伺服器上設定 RMS 連接器的登錄。
若要將 RMS 連接器設定為使用 Web Proxy 伺服器
在執行 RMS 連接器的每部伺服器上,開啟登錄編輯器,例如 Regedit。
流覽至 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\AADRM\連線 or
新增 ProxyAddress 的字串值,然後將此值的數據設定為 http://< MyProxyDomainOrIPaddress>:<MyProxyPort>
關閉登錄編輯器,然後重新啟動伺服器,或執行 IISReset 命令以重新啟動 IIS。
在系統管理電腦上安裝 RMS 連接器管理工具
如果該電腦符合下列需求,您可以從未安裝 RMS 連接器的電腦執行 RMS 連接器管理工具:
執行 Windows Server 2019、2016、2012 或 Windows Server 2012 R2(所有版本)、Windows 11、Windows 10、Windows 8.1、Windows 8 的實體或虛擬計算機。
至少 1 GB 的 RAM。
至少 64 GB 的磁碟空間。
至少一個網路介面。
透過防火牆存取因特網(或 Web Proxy)。
.NET 4.7.2
若要安裝 RMS 連接器管理工具,請針對 64 位電腦執行下列檔案:RMS 連線 orSetup.exe
如果您尚未下載這些檔案,您可以從 Microsoft 下載中心執行此動作。
如需詳細資訊,請參閱 RMS 連接器的必要條件。
更新 RMS 連接器安裝
安裝新版本的 RMS 連接器會自動 卸載任何舊版,並安裝所需的 .NET 4.7.2。 如果您遇到任何問題,請使用下列指示手動卸載舊版並安裝 .NET 4.7.2。
在您的 RMS 連接器電腦上,使用 [應用程式與功能] 設定頁面來卸載 Microsoft Rights Management 連線 or。
在舊版系統上,您可能會在 [控制台 > 程式和功能] 頁面中找到未安裝的選項。
流覽精靈以卸載 Microsoft Rights Management 連接器,然後選取結尾的 [ 完成 ]。
確認您的電腦已安裝 .NET 4.7.2。 如需詳細資訊,請參閱 如何:判斷已安裝哪些 .NET Framework 版本。
如果您需要,請下載並安裝 .NET 4.7.2 版。
出現提示時重新啟動計算機,然後繼續 安裝新的 RMS 連接器版本。
為 Azure RMS 連線 or 強制執行 TLS 1.2
Microsoft 會在 2022 年 3 月 1 日預設停用舊版不安全的 TLS 通訊協定,包括 RMS 服務上的 TLS 1.0 和 TLS 1.1。 若要準備這項變更,您可能想要關閉 RMS 連線 or 伺服器上這些舊通訊協定的支援,並確保系統會如預期般運作。
本節說明在 RMS 連線 or 伺服器上停用傳輸層安全性 (TLS) 1.0 和 1.1 的步驟,並強制使用 TLS 1.2。
關閉 TLS 1.0 和 1.1,並強制使用 TLS 1.2
請確定 RMS 連線 or 電腦上的 .NET Framework 為 4.7.2 版。 如需詳細資訊,請參閱 .NET Framework 4.7.2 版。
下載並安裝最新可用的 RMS 連線 or 版本。 如需詳細資訊,請參閱 安裝 RMS 連接器。
重新啟動 RMS 連線 or 伺服器,並測試 RMS 連線 or 功能。 例如,請確定內部部署 RMS 用戶能夠讀取其加密的檔。
如需詳細資訊,請參閱
確認 TLS 1.2 使用方式 (進階)
此程式提供如何驗證 TLS 1.2 正在使用的範例,而且需要事先瞭解 Fiddler。
在您的 RMS 連線 or 電腦上下載並安裝 Fiddler。
開啟 Fiddler,然後開啟 Microsoft RMS 連線 or 管理工具。
選取 [登入],雖然您不需要實際登入即可完成驗證。
在左側的 Fiddler 視窗中,尋找 msconnectoradmin 程式。 此程式應該嘗試建立與 discover.aadrm.com 的安全連線。
例如:
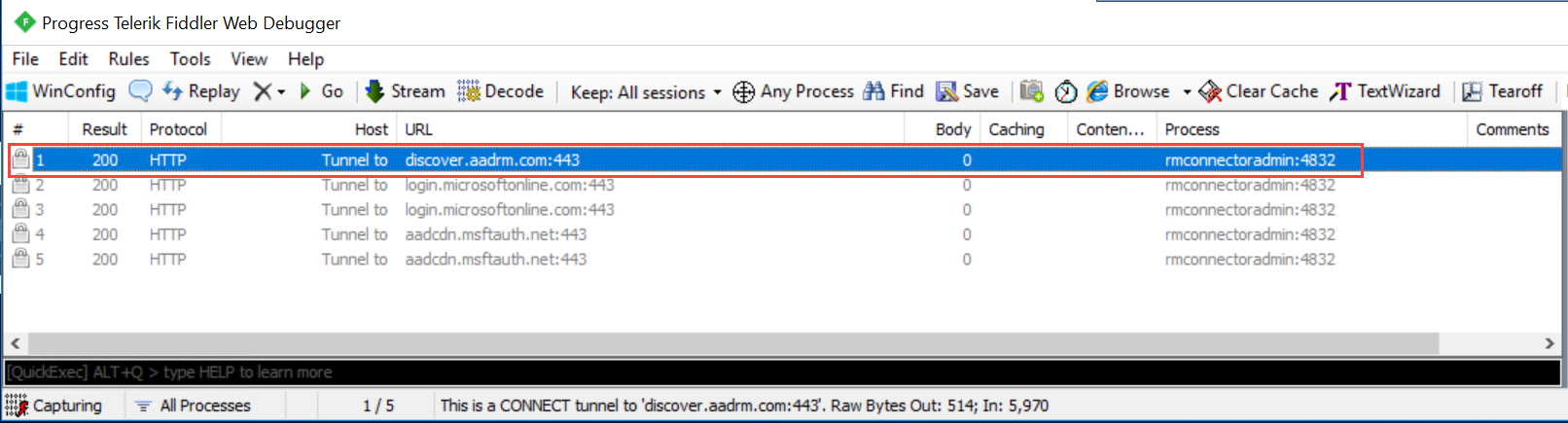
在右側的 Fiddler 視窗中,選取 [偵測器 ] 索引標籤,並檢視 要求和回應的 [文字檢視 ] 索引卷標。
在這些索引標籤中,請注意會使用 TLS 1.2 執行通訊。 例如:
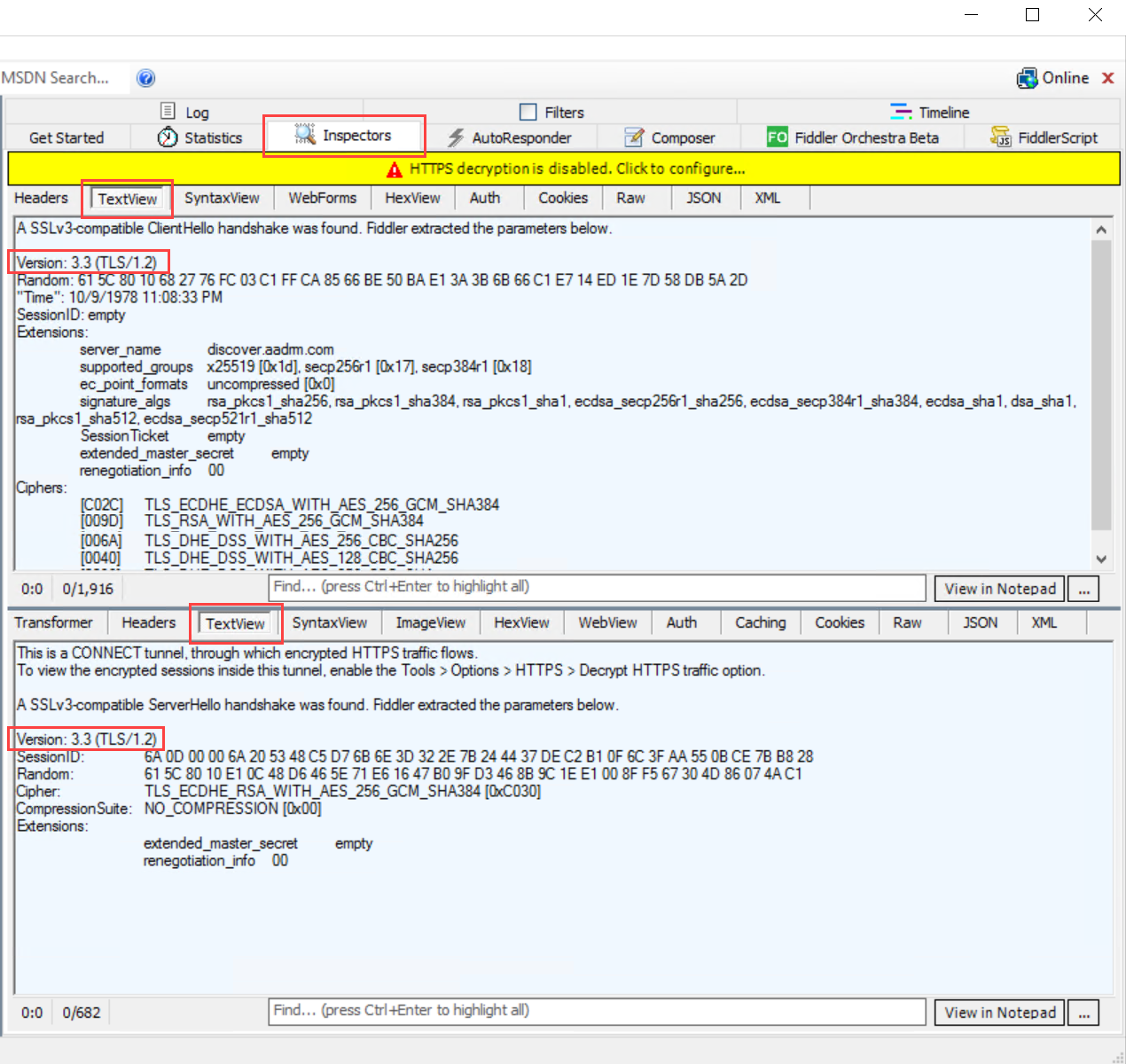
手動強制使用 TLS 1.2
如果您需要手動強制使用 TLS 1.2,請關閉任何舊版的使用量,請在 RMS 連接器電腦上執行下列 PowerShell 腳本。
警告
使用本節中的腳本會關閉每部機器上的 TLS 1.2 前通訊。 如果電腦上的其他服務需要 TLS 1.0 或 1.2,此腳本可能會中斷這些服務的功能。
$ProtocolList = @("SSL 2.0", "SSL 3.0", "TLS 1.0", "TLS 1.1", "TLS 1.2")
$ProtocolSubKeyList = @("Client", "Server")
$DisabledByDefault = "DisabledByDefault"
$Enabled = "Enabled"
$registryPath = "HKLM:\\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\"
foreach ($Protocol in $ProtocolList) {
foreach ($key in $ProtocolSubKeyList) {
$currentRegPath = $registryPath + $Protocol + "\" + $key
Write-Host " Current Registry Path $currentRegPath"
if (!(Test-Path $currentRegPath)) {
Write-Host "creating the registry"
New-Item -Path $currentRegPath -Force | out-Null
}
if ($Protocol -eq "TLS 1.2") {
Write-Host "Working for TLS 1.2"
New-ItemProperty -Path $currentRegPath -Name $DisabledByDefault -Value "0" -PropertyType DWORD -Force | Out-Null
New-ItemProperty -Path $currentRegPath -Name $Enabled -Value "1" -PropertyType DWORD -Force | Out-Null
}
else {
Write-Host "Working for other protocol"
New-ItemProperty -Path $currentRegPath -Name $DisabledByDefault -Value "1" -PropertyType DWORD -Force | Out-Null
New-ItemProperty -Path $currentRegPath -Name $Enabled -Value "0" -PropertyType DWORD -Force | Out-Null
}
}
}
下一步
既然已安裝並設定 RMS 連接器,您就可以設定內部部署伺服器來使用它。 移至設定 Microsoft Rights Management 連接器的伺服器。
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應