輸出規則 Azure Load Balancer
輸出規則可讓您為公用標準負載平衡器明確地定義 SNAT (來源網路位址轉譯)。 此設定可讓您使用負載平衡器的公用 IP,以為您的後端執行個體提供輸出網際網路連線能力。
此設定可啟用:
- IP 偽裝
- 簡化您的允許清單。
- 減少部署的公用 IP 資源數目。
使用輸出規則時,您可以完整地以宣告方式控制輸出網際網路連線能力。 輸出規則可讓您調整此功能,以滿足您的特定需求。
只有當後端 VM 沒有執行個體層級公用 IP 位址 (ILPIP) 時,才會遵循輸出規則。
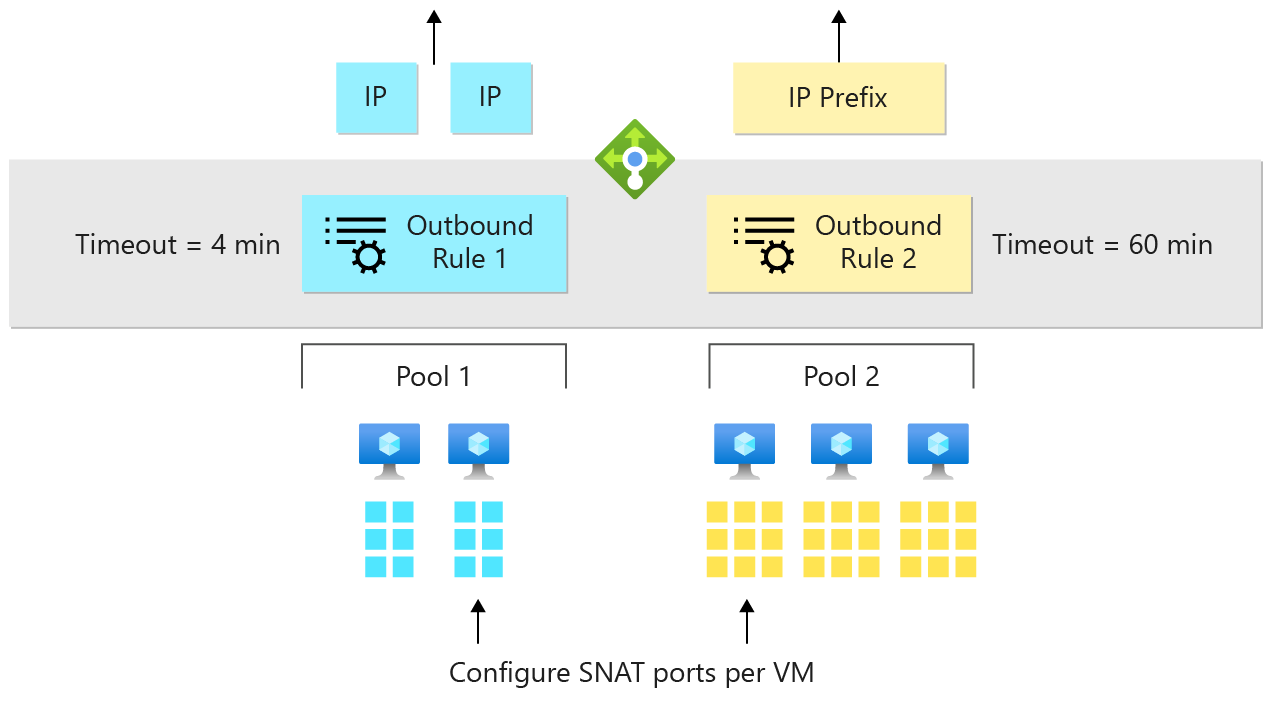
使用輸出規則,您可以明確地定義輸出 SNAT 行為。
輸出規則可讓您控制:
- 哪些虛擬機器會轉譯成哪些公用 IP 位址。
- 兩個規則是後端集區 1 使用藍色 IP 位址,後端集區 2 則是使用黃色 IP 首碼。
- 輸出 SNAT 連接埠的配置方式。
- 如果後端集區 2 是建立輸出連線的唯一集區,請將所有 SNAT 連接埠授與後端集區 2,而不授與後端集區 1 任何連接埠。
- 要提供其輸出轉譯的通訊協定。
- 如果後端集區 2 需要 UDP 連接埠以便進行輸出,而後端集區 1 需要 TCP,請將 TCP 連接埠提供給 1 和 UDP 連接埠提供給 2。
- 要用於輸出連線閒置逾時的持續時間 (4-120 分鐘)。
- 如果有長時間執行的連線具有 keepalive,請為長時間執行的連線保留閒置的連接埠達最多 120 分鐘。 假設已放棄過時的連線,並在 4 分鐘內針對新的連線釋放連接埠
- 是否要在閒置逾時時傳送 TCP重設。
- 當閒置連線逾時時,是否要將 TCP RST 傳送給用戶端和伺服器,讓他們知道已放棄該流量?
重要
當後端集區是以 IP 位址設定時,行為會如同預設啟用輸出的基本 Load Balancer。 若為有輸出需求的安全預設設定和應用程式,請以 NIC 設定後端集區。
輸出規則定義
如同所有負載平衡器規則,輸出規則會遵循與負載平衡和輸入 NAT 規則相同的熟悉語法:前端 + 參數 + 後端集區。
輸出規則會將「後端集區所識別的所有虛擬機器」的輸出 NAT 設定為轉譯成「前端」。
「參數」提供對輸出 NAT 演算法的精細控制。
使用多個 IP 位址擴增輸出 NAT
前端所提供的每個額外 IP 位址都會提供另外的 64,000 個暫時連接埠,以供負載平衡器當成 SNAT 連接埠使用。
使用多個 IP 位址來規劃大規模案例。 使用輸出規則來減輕 SNAT 耗盡的問題。
您還可以直接使用公用 IP 首碼搭配輸出規則。
公用 IP 首碼可增加部署的規模。 可以將首碼新增至源自 Azure 資源的流量的允許清單。 您可以在負載平衡器內設定前端 IP 設定,以參考公用 IP 位址首碼。
負載平衡器具有公用 IP 首碼的控制權。 輸出規則會自動使用公用 IP 首碼中包含的所有公用 IP 位址來進行輸出連線。
公用 IP 首碼內的每個 IP 位址都會為每個 IP 位址提供額外的 64,000 個暫時連接埠,以供負載平衡器當成 SNAT 連接埠使用。
輸出流量閒置逾時和 TCP 重設
輸出規則提供設定參數來控制輸出流程閒置逾時,並使其符合您應用程式的需求。 輸出閒置逾時預設為 4 分鐘。 如需詳細資訊,請參閱設定閒置逾時。
負載平衡器的預設行為,是在達到輸出閒置逾時的當時以無訊息方式捨棄流程。 enableTCPReset 參數會啟用可預測的應用程式行為和控制。 該參數會指定是否要在輸出閒置逾時的逾時時,傳送雙向 TCP 重設 (TCP RST)。
如需詳細資料 (包含區域可用性),請檢閱閒置逾時的 TCP 重設。
明確保護和控制輸出連線能力
負載平衡規則會提供輸出 NAT 的自動程式設計。 某些案例會透過負載平衡規則獲益或要求您停用輸出 NAT 的自動程式設計。 透過規則停用可讓您控制或精簡該行為。
您可以透過兩種方式來使用此參數:
防止輸出 SNAT 的輸入 IP 位址。 在負載平衡規則中停用輸出 SNAT。
調整同時用於輸入和輸出的 IP 位址的輸出 SNAT 參數。 必須停用自動輸出 NAT,以允許輸出規則取得控制。 若要將位址的 SNAT 連接埠配置變更為也用於輸入,
disableOutboundSnat參數必須設定為 true。
如果您嘗試重新定義用於輸入的 IP 位址,則設定輸出規則的作業將會失敗。 先停用負載平衡規則的輸出 NAT。
重要
如果您將此參數設定為 true,但沒有輸出規則來定義輸出連線能力,則您的虛擬機器將不會有輸出連線能力。 您 VM 或應用程式的某些作業可能取決於可用輸出連線。 請確定您了解情節的相依性,並考慮這項變更的影響。
有時,您會不想讓 VM 建立輸出流程。 要管理要接收輸出流量的是哪些目的地,或哪些目的地可以開始輸入流量,可能有一項要求。 使用網路安全性群組來管理 VM 可到達的目的地。 使用 NSG 來管理哪些公用目的地可開始輸入流量。
當您將 NSG 套用到經過負載平衡的虛擬機器時,請注意服務標記和預設安全性規則。
確保 VM 可以從 Azure Load Balancer 接收健全狀況探查要求。
如果 NSG 封鎖來自 AZURE_LOADBALANCER 預設標籤的健全狀況探查要求,您的 VM 健全狀況探查會失敗,且會將 VM 標示為無法使用。 負載平衡器會停止將新的流量傳送到該 VM。
輸出規則案例
- 設定對一組特定公用 IP 或首碼的輸出連線。
- 修改 SNAT 連接埠配置。
- 僅啟用輸出。
- 僅 VM 的輸出 NAT (無輸入)。
- 用於內部標準負載平衡器的輸出 NAT。
- 使用公用標準負載平衡器啟用輸出 NAT 的 TCP 和 UDP 通訊協定。
案例 1:設定對一組特定公用 IP 或首碼的輸出連線
詳細資料
使用此案例來為輸出連線量身打造為源自一組公用 IP 位址。 根據來源將公用 IP 或首碼新增至允許或封鎖清單。
此公用 IP 或首碼可以與負載平衡規則所使用的相同。
若要使用與負載平衡規則所使用的不同公用 IP 或首碼:
- 建立公用 IP 首碼或公用 IP 位址。
- 建立公用標準負載平衡器
- 建立參考您要使用的公用 IP 首碼 (或公用 IP 位址) 的前端。
- 重複使用後端集區,或建立後端集區,並將 VM 放入公用負載平衡器的後端集區
- 在公用負載平衡器上設定輸出規則,以使用前端啟用 VM 的輸出 NAT。 不建議針對輸出使用負載平衡規則,在負載平衡規則上停用輸出 SNAT。
案例 2:修改 SNAT 連接埠配置
詳細資料
您可以使用輸出規則來調整根據後端集區大小的自動 SNAT 連接埠配置。
如果您遇到 SNAT 耗盡的情況,請增加提供預設值 1024 的 SNAT 連接埠數目。
每個公用 IP 位址都可提供最多 64,000 個暫時連接埠。 後端集區中的 VM 數目會決定分散至每部 VM 的連接埠數目。 後端集區中的一部 VM 可以存取最多 64,000 個連接埠。 針對兩部 VM,最多可以使用一個輸出規則來配置 32,000 個 SNAT 連接埠 (2x 32,000 = 64,000)。
您可以使用輸出規則來調整預設提供的 SNAT 連接埠。 您可以提供較預設 SNAT 連接埠配置所提供更多或更少的數量。 來自輸出規則的前端的每個公用 IP 位址都會提供最多 64,000 個暫時連接埠,以當成 SNAT 連接埠使用。
負載平衡器會以 8 的倍數提供 SNAT 連接埠。 如果您提供的值無法與 8 整除,則會拒絕設定作業。 每個負載平衡規則和輸入 NAT 規則都會耗用八個連接埠的範圍。 如果負載平衡或輸入 NAT 規則與另一個規則共用 8 的相同範圍,將不會耗用額外的連接埠。
如果您嘗試提供比可用 SNAT 連接埠更多的 SNAT 連接埠 (根據公用 IP 位址數目),則該設定作業會遭到拒絕。 例如,如果您為每部 VM 提供 10,000 個連接埠,且後端集區中有七部 VM 共用單一公用 IP,則會拒絕該設定。 七乘以 10,000 即超過 64,000 個連接埠的限制。 將更多公用 IP 位址新增至輸出規則的前端,可啟用該案例。
指定 0 作為連接埠數目,以還原為預設連接埠配置。 如需預設 SNAT 連接埠配置的詳細資訊,請參閱 SNAT 連接埠配置表。
案例 3:僅啟用輸出
詳細資料
使用公用 Standard Load Balancer 來提供一組 VM 的輸出 NAT。 在此案例中,請使用輸出規則本身,而不要設定額外的規則。
注意
Azure NAT 閘道 可以提供虛擬機的輸出連線,而不需要負載平衡器。 如需詳細資訊,請參閱什麼是 Azure NAT 閘道?
案例 4:僅 VM 的輸出 NAT (無輸入)
注意
Azure NAT 閘道 可以提供虛擬機的輸出連線,而不需要負載平衡器。 如需詳細資訊,請參閱什麼是 Azure NAT 閘道?
詳細資料
針對此案例:Azure Load Balancer 輸出規則和虛擬網路 NAT 是可從虛擬網路輸出的選項。
- 建立公用 IP 或首碼。
- 建立公用標準負載平衡器。
- 建立與公用 IP 或用於輸出的首碼相關聯的前端。
- 建立 VM 的後端集區。
- 將 VM 放入後端集區。
- 設定輸出規則以啟用輸出 NAT。
使用首碼或公用 IP 來調整 SNAT 連接埠。 將輸出連線的來源新增至允許或封鎖清單。
案例 5:用於內部負載平衡器的輸出 NAT
注意
Azure NAT 閘道 可為使用內部標準負載平衡器的虛擬機提供輸出連線能力。 如需詳細資訊,請參閱什麼是 Azure NAT 閘道?
詳細資料
輸出連線能力無法供內部標準負載平衡器使用,除非透過執行個體層級的公用 IP 或虛擬網路 NAT 明確宣告它,或是將後端集區成員與僅限輸出的負載平衡器設定產生關聯。
如需詳細資訊,請參閱僅限輸出的負載平衡器設定。
案例 6:使用公用標準負載平衡器啟用輸出 NAT 的 TCP 和 UDP 通訊協定
詳細資料
使用公用標準負載平衡器時,所提供的自動輸出 NAT 會符合負載平衡規則的傳輸通訊協定。
- 在負載平衡規則上停用輸出 SNAT。
- 在相同的負載平衡器上設定輸出規則。
- 重複使用 VM 已使用的後端集區。
- 指定 "protocol": "All" 作為輸出規則的一部分。
僅使用輸出 NAT 規則時,不會提供輸出 NAT。
- 將 VM 放入後端集區中。
- 使用公用 IP 位址或公用 IP 首碼,定義一或多個前端 IP 設定
- 在相同的負載平衡器上設定輸出規則。
- 指定 "protocol": "All" 作為輸出規則的一部分
限制
- 每個前端 IP 位址的可用暫時連接埠數目上限為 64,000。
- 可設定輸出閒置逾時的範圍為 4 到 120 分鐘 (240 到 7200 秒)。
- 負載平衡器不支持輸出 NAT 的 ICMP,唯一支援的通訊協定是 TCP 和 UDP。
- 輸出規則只能套用至 NIC 的主要 IPv4 組態。 您無法為 VM 或 NVA 的次要 IPv4 組態建立輸出規則。 支援多個 NIC。
- 只有 IPv6 支援次要 IP 組態的輸出規則。
- 可用性設定組內的所有虛擬機器都必須新增至後端集區,才能獲得輸出連線能力。
- 虛擬機器擴展集內的所有虛擬機器都必須新增至後端集區,才能獲得輸出連線能力。