控管探索到的應用程式
檢閱環境中探索到的應用程式清單之後,您可以透過下列方式核准安全應用程式(已獲批准)或禁止垃圾應用程式,以保護環境。
批准/不批准應用程式
您可以按下資料列結尾的三個點,將特定有風險的應用程式標示為未經批准。 然後選取 [未批准]。 不批准應用程式不會封鎖使用,而是讓您透過 Cloud Discovery 篩選更輕鬆地監視其使用情況。 然後,您可以通知使用者未經批准的應用程式,並建議替代的安全應用程式以供其使用,或使用 適用於雲端的 Defender Apps API 產生區塊腳本,以封鎖所有未經批准的應用程式。
使用內建串流封鎖應用程式
如果您的租使用者使用 適用於端點的 Microsoft Defender,一旦您將應用程式標示為未批准,它就會自動遭到封鎖。 此外,您可以將封鎖範圍限制為適用於端點的特定Defender裝置群組、監視應用程式,以及使用 警告和教育 功能。 如需詳細資訊,請參閱使用 適用於端點的 Microsoft Defender 控管探索到的應用程式。
否則,如果您的租使用者使用 Zscaler NSS、iboss、Corrata、Menlo 或 Open Systems,當應用程式未經批准時,您仍然可以享受無縫封鎖功能,但無法依裝置群組使用範圍,或 警告和教育 功能。 如需詳細資訊,請參閱 與 Zscaler 整合、 與 iboss 整合、 與 Corrata 整合、 與 Menlo 整合,以及 與 Open Systems 整合。
匯出區塊腳本來封鎖應用程式
適用於雲端的 Defender Apps 可讓您使用現有的內部部署安全性設備來封鎖對未經批准之應用程式的存取。 您可以產生專用的封鎖指令碼並將它匯入您的設備。 此解決方案不需要將組織所有的網路流量重新導向到 Proxy。
在 Cloud Discovery 儀表板中,將您要封鎖的應用程式標記為待批准。
在標題欄中,選取 [ 動作 ],然後選取 [ 產生區塊腳本...]。
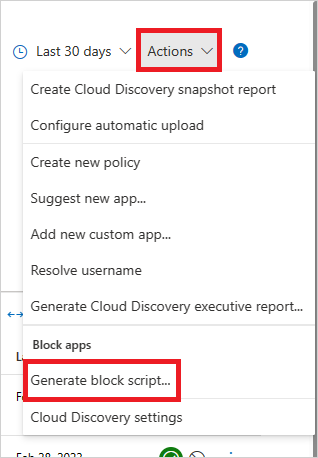
在 [Generate block script]\(產生封鎖指令碼) 中,選取所產生之封鎖指令碼的適用裝置。
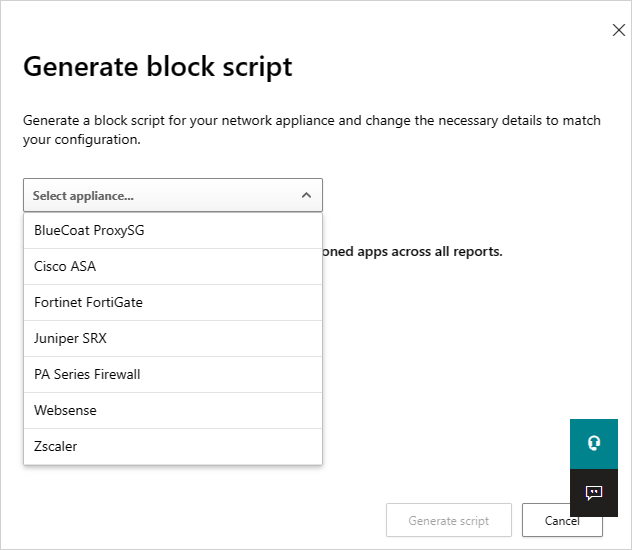
然後選取 [ 產生腳本 ] 按鈕,為所有未經批准的應用程式建立區塊腳本。 根據預設,檔案會以導出的日期和您選取的設備類型命名。 2017-02-19_CAS_Fortigate_block_script.txt是範例檔名。
將建立的檔案匯入您的設備。
封鎖不支持的數據流
如果您的租使用者未使用上述任何數據流,您仍然可以匯出所有未經批准應用程式的所有網域清單,並設定您的第三方非支持設備來封鎖這些網域。
在 [ 探索到的應用程式] 頁面中,篩選所有 未核准 的應用程式,然後使用匯出功能匯出所有網域。
不可封鎖的應用程式
若要防止使用者不小心封鎖業務關鍵服務並造成停機時間,無法透過UI或原則使用 適用於雲端的 Defender Apps封鎖下列服務:
- Microsoft Defender for Cloud Apps
- Microsoft Defender 資訊安全中心
- Microsoft 365 資訊安全中心
- 適用於身分識別的 Microsoft Defender
- Microsoft Purview
- Microsoft Entra 權限管理
- Microsoft 條件式存取應用程控
- Microsoft 安全分數
- Microsoft Purview 合規性入口網站
- Microsoft Intune
- Microsoft 支援服務
- Microsoft AD FS 說明
- Microsoft 支援服務
- Microsoft Online Services
治理衝突
如果手動治理動作與原則所設定的治理之間發生衝突,則套用的最後一個作業優先。
下一步
如果您遇到任何問題,我們會在這裡提供説明。 若要取得產品問題的協助或支援,請 開啟支援票證。
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應
