建立更加安全的來賓共用環境
在本文中,我們會逐步解說在 Microsoft 365 中建立更安全來賓共用環境的各種選項。 下列是可讓您了解可用選項的一些範例。 您可以用不同的組合使用這些程序,以符合貴組織的安全性和合規性需求。
本文包括:
- 設定來賓的多重要素驗證。
- 為來賓設定使用規定。
- 設定每季來賓存取權檢閱,以定期驗證來賓是否繼續需要小組和網站的使用權限。
- 將來賓限制為僅限網頁存取未受管理的裝置。
- 設定工作階段逾時原則,以確保來賓每天進行驗證。
- 為高敏感性專案建立敏感性資訊類型。
- 自動將高敏感性標籤指派給包含敏感性資訊類型的文件。
- 自動從具有敏感度標籤的檔案移除來賓存取。
本文中討論的一些選項會要求來賓在Microsoft Entra識別碼中擁有帳戶。 若要確保當您與他們共用檔案和資料夾時,會將來賓包含在目錄中,請使用SharePoint 和 OneDrive 與 Microsoft Entra B2B 預覽版整合。
請注意,我們不會在本文中討論如何啟用來賓共用設定。 如需針對不同案例啟用來賓共用的詳細資訊,請參閱與組織外部人員共同作業。
設定來賓的多重要素驗證
多重要素驗證可大幅降低帳戶遭到入侵的機會。 由於來賓可能使用未遵守任何治理原則或最佳做法的個人電子郵件帳戶,因此要求來賓進行多重要素驗證特別重要。 若來賓的使用者名稱和密碼遭竊,要求第二個驗證要素能大幅降低未知人員存取網站和檔案的機會。
在此範例中,我們會使用Microsoft Entra識別碼中的條件式存取原則,為來賓設定多重要素驗證。
設定來賓的多重要素驗證
- 開啟Microsoft Entra系統管理中心。
- 展開 [保護],然後選取 [條件式存取]。
- 在 條件式存取上 |[概觀 ] 頁面,選取 [建立新原則]。
- 在 [名稱] 欄位中,輸入名稱。
- 選取 [ 使用者 ] 連結。
- 選擇 [選取使用者和群組],然後選取 [ 來賓或外部使用者] 核取方塊。
- 在下拉式清單中,選取 [B2B 共同作業來賓使用者 ] 和 [B2B 共同作業成員使用者]。
- 選取 [目標資源] 連結。
- 選取 [包含] 索引標籤上的 [所有雲端應用程式]。
- 選取 [授與 ] 連結。
- 在 [ 授與] 刀鋒視窗上,選取 [ 需要多重要素驗證] 複 選框,然後按一下 [ 選取]。
- 在 [ 啟用原則]底下,選取 [ 開啟],然後選取 [ 建立]。
現在,來賓必須先註冊多重要素驗證,才能存取共用內容、網站或小組。
其他相關資訊
為來賓設定使用規定
在某些情況下,來賓可能未與貴組織簽署保密協定或其他法律合約。 在來賓存取與他們共用的檔案之前,您可以要求來賓同意使用規定。 使用規定可在來賓首次嘗試存取共用檔案或網站時顯示。
若要建立使用規定,您必須先在 Word 或其他撰寫程式建立文件,然後將文件儲存為 .pdf 檔案。 此檔案接著可以上傳至Microsoft Entra識別碼。
建立Microsoft Entra使用規定
展開 [保護],然後選取 [條件式存取]。
選 取 [使用規定]。
選取 [新增字詞]。
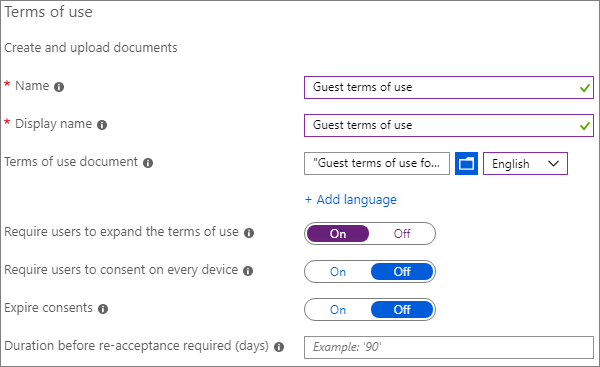
輸入 名稱。
在使用規定文件,瀏覽及選取您建立的 PDF 檔案。
選取使用規定文件的語言。
輸入顯示名稱。
將 [要求使用者展開使用規定] 設為 [開啟]。
在 [條件式存取] 底下的 [強制使用條件式存取原則範本] 清單中,選擇 [稍後建立條件式存取原則]。
選取 [建立]。
建立使用規定後,下一個步驟是建立條件式存取原則,以顯示來賓的使用規定。
若要建立條件式存取原則
- 在 [Microsoft Entra 系統管理中心] 的 [保護] 下,選取 [條件式存取]。
- 在 條件式存取上 |[概觀 ] 頁面,選取 [建立新原則]。
- 在 [名稱] 方塊中,輸入名稱。
- 選取 [ 使用者 ] 連結。
- 選 取 [選取使用者和群組],然後選取 [ 來賓或外部使用者] 核取方塊。
- 在下拉式清單中,選取 [B2B 共同作業來賓使用者 ] 和 [B2B 共同作業成員使用者]。
- 選取 [目標資源] 連結。
- 在 [ 包含] 索引標籤上, 選取 [選取應用程式],然後按一下 [ 選取 ] 連結。
- 在 [選取]刀鋒視窗上,選取 [Office 365],然後按一下 [選取]。
- 選取 [授與 ] 連結。
- 在 [ 授與] 刀鋒視窗上,選取您所建立使用規定核取方塊,然後按一下 [ 選取]。
- 在 [ 啟用原則]底下,選取 [ 開啟],然後選取 [ 建立]。
現在,來賓第一次嘗試存取貴組織中的內容或小組或網站時,必須接受使用規定。
其他相關資訊
Microsoft SharePoint eSignature 概觀
設定來賓存取權檢閱
使用Microsoft Entra識別碼的存取權檢閱,您可以自動定期檢閱使用者對各種小組和群組的存取權。 藉由特別要求來賓的存取權檢閱,您可以協助確保來賓不會將貴組織的敏感性資訊存取保留超過所需的時間。
設定來賓存取權檢閱
展開 [身分識別控管],然後選 取 [存取權檢閱]。
選 取 [新增存取權檢閱]。
選擇 Teams + 群組 選項。
選擇 來賓使用者的所有 Microsoft 365 群組 選項。 如果您想要排除任何群組,請按一下 [選取排除群組]。
選擇 [ 僅限來賓使用者 ] 選項,然後選取 [ 下一步:檢閱]。
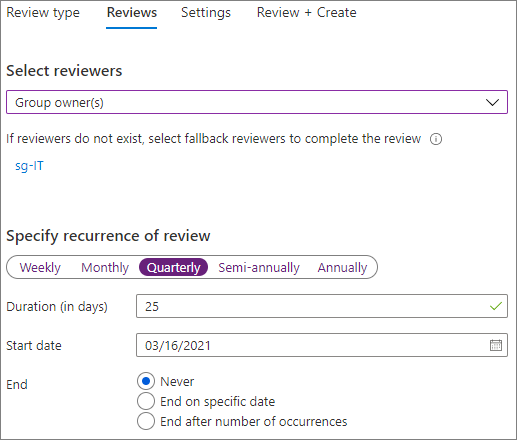
在 [選取檢閱者]下,選擇 [群組擁有者]。
按一下 [選取遞補檢閱者],選擇誰是遞補檢閱者,然後按一下 [選取]。
選擇 [ 持續時間] (天) ,以供檢閱開啟以供批註使用。
在 [指定檢閱週期]下,選擇 [季度]。
選取開始日期和期間。
針對 [結束],選擇 [ 永不],然後選取 [ 下一步:設定]。
在 [設定] 索引標籤上,檢閱符合您商務規則的設定。
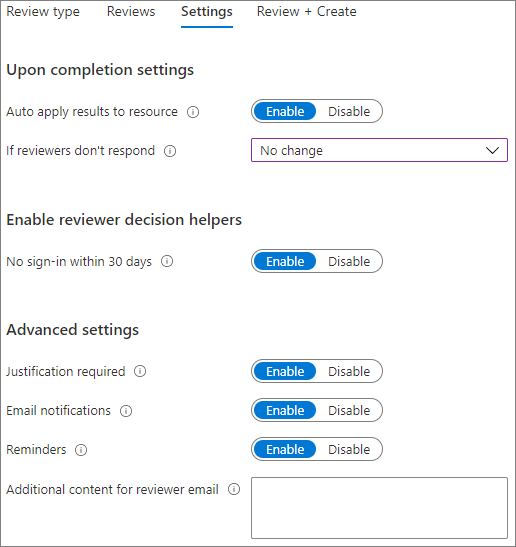
選 取 [下一步:檢閱 + 建立]。
輸入 [檢閱名稱] 並檢閱設定。
選取 [建立]。
其他相關資訊
在Microsoft Entra識別碼中建立群組和應用程式的存取權檢閱
為具有非受控裝置的來賓設定僅限 Web 存取
如果您的來賓使用的裝置不是由您的組織或其他與您有信任關係的組織所管理,則您只能使用網頁瀏覽器要求他們存取您的小組、網站和檔案。 這可減少他們下載敏感性檔案並將它們保留在非受控裝置上的機會。 當與使用共用裝置的環境共用時,這也很有用。
針對Microsoft 365 群組和 Teams,這會使用Microsoft Entra條件式存取原則來完成。 若為 SharePoint,這會在 SharePoint 系統管理中心設定。 (您也可以使用敏感度標籤將來賓限制在僅限 Web 存取。)
為群組和小組將來賓限制在僅限 Web 存取:
展開 [保護],然後選取 [條件式存取]。
在 條件式存取上 |[概觀 ] 頁面,選取 [建立新原則]。
在 [名稱] 方塊中,輸入名稱。
選取 [ 使用者 ] 連結。
選 取 [選取使用者和群組],然後選取 [ 來賓或外部使用者] 核取方塊。
在下拉式清單中,選取 [B2B 共同作業來賓使用者 ] 和 [B2B 共同作業成員使用者]。
選取 [目標資源] 連結。
在 [ 包含] 索引標籤上, 選取 [選取應用程式],然後按一下 [ 選取 ] 連結。
在 [選取]刀鋒視窗上,選取 [Office 365],然後按一下 [選取]。
選取 [條件] 連結。
在 [ 條件] 刀鋒 視窗上,選取 [用戶端應用程式] 連結。
在 [用戶端應用程式]刀鋒視窗上,針對 [設定] 選取 [是],然後選取 [行動應用程式和桌面客戶端]、[Exchange ActiveSync客戶端]和 [其他客戶端] 設定。 清除 [瀏覽] 核取方塊。
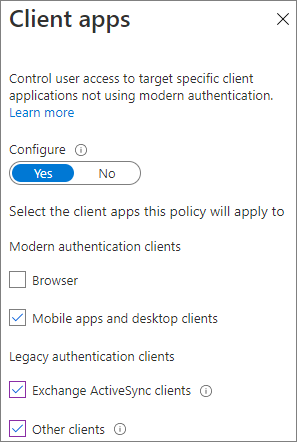
選取 [完成]。
選取 [授與 ] 連結。
在 [授與]刀鋒視窗上,選取 [需要將裝置標示為符合規範] 和 [需要Microsoft Entra混合式聯結裝置]。
在 [針對多個控制項] 底下,選取 [需要其中一個選取的控制項],然後按一下 [選取]。
在 [ 啟用原則]底下,選取 [ 開啟],然後選取 [ 建立]。
其他相關資訊
SharePoint 和 OneDrive 非受控裝置存取控制
為來賓設定工作階段逾時。
若來賓的裝置不安全,要求來賓定期驗證可降低未知的使用者存取貴組織內容的可能性。 您可以在Microsoft Entra識別碼中設定來賓的會話逾時條件式存取原則。
若要設定來賓工作階段逾時原則
- 開啟Microsoft Entra系統管理中心。
- 展開 [保護],然後選取 [條件式存取]。
- 在 條件式存取上 |[概觀 ] 頁面,選取 [建立新原則]。
- 在 [名稱] 欄位中,輸入名稱。
- 選取 [ 使用者 ] 連結。
- 選 取 [選取使用者和群組],然後選取 [ 來賓或外部使用者] 核取方塊。
- 在下拉式清單中,選取 [B2B 共同作業來賓使用者 ] 和 [B2B 共同作業成員使用者]。
- 選取 [目標資源] 連結。
- 在 [ 包含] 索引標籤上, 選取 [選取應用程式],然後按一下 [ 選取 ] 連結。
- 在 [選取]刀鋒視窗上,選取 [Office 365],然後按一下 [選取]。
- 選取 [會話 ] 連結。
- 在 [工作階段] 刀鋒視窗中,選取 [登入頻率]。
- 選擇 [1 ] 和 [ 天 ] 作為時段,然後按一下 [ 選取]。
- 在 [ 啟用原則]底下,選取 [ 開啟],然後選取 [ 建立]。
建立高敏感度專案的敏感性資訊類型
敏感性資訊類型是預先定義的字串,可用於原則工作流程中,以強制執行法規遵循需求。 Microsoft Purview 合規性入口網站隨附超過 100 種敏感性資訊類型,包括駕照編號、信用卡號、銀行帳號等。
您可以建立自訂敏感性資訊類型以協助管理貴組織的特定內容。 在此範例中,我們會為高敏感性專案建立自訂敏感性資訊類型。 然後,我們可以使用此敏感性資訊類型自動套用敏感性標籤。
若要建立敏感性資訊類型
- 在Microsoft Purview 合規性入口網站的左側導覽中,展開 [資料分類],然後選取 [分類器]。
- 選取 [ 敏感性資訊類型] 索引卷 標。
- 選 取 [建立敏感性資訊類型]。
- 針對 [名稱 ] 和 [描述],輸入 專案 Saturn,然後選取 [ 下一步]。
- 選 取 [建立模式]。
- 在 [ 新增模式] 面板上,選取 [ 新增主要元素],然後選取 [關鍵字清單]。
- 輸入 標識 符,例如 專案 Saturn。
- 在 [ 不區分大小寫 ] 方塊中,輸入 專案 Saturn、Saturn,然後選取 [ 完成]。
- 選 取 [建立],然後選取 [ 下一步]。
- 選擇信賴等級,然後選取 [ 下一步]。
- 選取 [建立]。
- 選取 [完成]。
如需詳細資訊,請 參閱瞭解敏感性資訊類型。
建立自動標籤原則,以根據敏感性資訊類型指派敏感度標籤
如果您在組織中使用敏感度標籤,您可以自動將標籤套用至包含已定義敏感性資訊類型的檔案。
建立自動套用標籤原則
- 開啟 Microsoft Purview 系統管理中心。
- 在左側導覽中,展開 [資訊保護],然後選取 [自動套用標籤]。
- 選 取 [建立自動套用標籤原則]。
- 在 [ 選擇要套用此標籤的資訊] 頁面上,選擇 [ 自訂 ],然後選取 [ 自訂原則]。
- 選取 [下一步]。
- 輸入原則的名稱和描述,然後選取 [ 下一步]。
- 在 [ 指派系統管理單位] 頁面上,選取 [ 下一步]。
- 在 [ 選擇要套用標籤的位置 ] 頁面上,選取 [SharePoint 網站 ],然後選擇性地選取 [ 編輯 ] 以選擇網站。
- 選取 [下一步]。
- 在 [ 設定通用或進階規則] 頁面上,選擇 [ 一般規則] ,然後選取 [ 下一步]。
- 在 [ 定義所有位置內容的規則 ] 頁面上,選取 [ 新增規則]。
- 在 [ 新增規則] 頁面上,為規則命名,選取 [ 新增條件],然後選取 [ 內容包含]。
- 選取 [新增],選取 [敏感性資訊類型],選擇您要使用的敏感性資訊類型,選取 [ 新增],然後選取 [ 儲存]。
- 選取 [下一步]。
- 選 取 [選擇標籤],選取您要使用的標籤,然後選取 [ 新增]。
- 選取 [下一步]。
- 讓原則保持模擬模式,並選擇是否要自動開啟。
- 選取 [下一步]。
- 選 取 [建立原則],然後選取 [ 完成]。
建立原則後,當使用者在文件中輸入「Saturn 專案」時,自動標籤原則將在掃描檔案時自動套用指定的標籤。
如需自動套用標籤的詳細資訊,請參閱 自動將敏感度標籤套用至內容。
其他相關資訊
建立 DLP 原則以移除高敏感性檔案的來賓存取
您可以使用 Microsoft Purview 資料外洩防護 (DLP) 以防止不必要的來賓共用敏感性內容。 資料外洩防護可以根據檔案的敏感度標籤採取動作,並移除來賓存取。
建立 DLP 規則
在左側導覽中,展開 [資料外泄防護],然後選取 [ 原則]。
選取 [建立原則]。
依 序選擇 [自訂 ] 和 [ 自訂原則]。
選取 [下一步]。
輸入原則的名稱,然後選取 [ 下一步]。
在 [ 指派系統管理單位] 頁面上,選取 [ 下一步]。
在 [要套用原則的位置 ] 頁面上,關閉 SharePoint 網站 和 OneDrive 帳戶以外的所有設定,然後選取 [ 下一步]。
在 [ 定義原則設定] 頁面上,選取 [ 下一步]。
在 [ 自訂進階 DLP 規則 ] 頁面上,選取 [ 建立規則 ] 並輸入規則的名稱。
在 [ 條件]下,選取 [新增條件],然後選擇 [內容從 Microsoft 365 共用]。
在下拉式清單中,選擇 與組織外部的人員搭配使用。
在 [ 條件] 底下,選取 [新增條件],然後選擇 [ 內容包含]。
選取 [新增],選擇 [ 敏感度標籤],選擇您要使用的標籤,然後選取 [ 新增]。
在 [ 動作 ] 底下,選 取 [新增動作] ,然後選擇 [ 限制存取或加密 Microsoft 365 位置中的內容]。
選擇 [ 僅封鎖組織外部的人員] 選項。

開啟使用者通知,然後選取 [在Office 365服務中使用原則提示通知使用者] 核取方塊。
選取 [儲存 ],然後選取 [ 下一步]。
選擇您的測試選項,然後選取 [ 下一步]。
選取 [提交],然後選取 [ 完成]。
請注意,如果來賓是網站或小組整體的成員,則此原則不會移除存取。 如果您規劃讓具有來賓成員的網站或小組擁有高敏感度文件,請考慮這些選項:
其他選項
Microsoft 365 和 Microsoft Entra 識別碼中有一些額外的選項可協助保護您的來賓共用環境。
- 您可以建立允許或拒絕共用網域的清單,以限制要共用的使用者。 如需詳細資訊,請參閱依網域限制 SharePoint 和 OneDrive 內容的共用和允許或封鎖對特定組織的 B2B 使用者的邀請。
- 您可以限制使用者可以連線的其他Microsoft Entra租使用者。 如需詳細資訊,請參閱 限制對租使用者的存取 。
- 您可以建立受管理環境,讓合作夥伴能夠協助管理來賓帳戶。 如需詳細資訊,請參閱建立 B2B 外部網路。
相關文章
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應