Power BI 安全性
如需 Power BI 安全性的詳細資訊,請參閱 Power BI 安全性白皮書。
若要規劃 Power BI 安全性,請參閱 Power BI 實作規劃 安全性系列文章。 它會擴充Power BI安全性白皮書中的內容。 雖然 Power BI 安全性白皮書著重於驗證、數據落地和網路隔離等重要技術主題,但系列的主要目標是為您提供考慮和決策,以協助您規劃安全性和隱私權。
Power BI 服務 建置在 Microsoft 的雲端運算基礎結構和平臺 Azure 上。 Power BI 服務 的架構是以兩個叢集為基礎:
- Web 前端 (WFE) 叢集。 WFE 叢集會管理對 Power BI 服務 的初始連線和驗證。
- 後端叢集。 驗證之後,後端會處理所有後續的用戶互動。 Power BI 會使用 Microsoft Entra 識別符來儲存和管理使用者身分識別。 Microsoft Entra ID 也會分別使用 Azure BLOB 和 Azure SQL 資料庫 來管理數據記憶體和元數據。
Power BI 架構
WFE 叢集會使用 Microsoft Entra ID 來驗證用戶端,併為後續用戶端連線 Power BI 服務 提供令牌。 Power BI 會使用 Azure 流量管理員 (流量管理員) 將使用者流量導向至最近的數據中心。 流量管理員 使用嘗試連線、驗證及下載靜態內容和檔案之用戶端的 DNS 記錄來指示要求。 Power BI 會使用 Azure 內容傳遞網路 (CDN),根據地理地區設定,有效率地將必要的靜態內容和檔案散發給使用者。
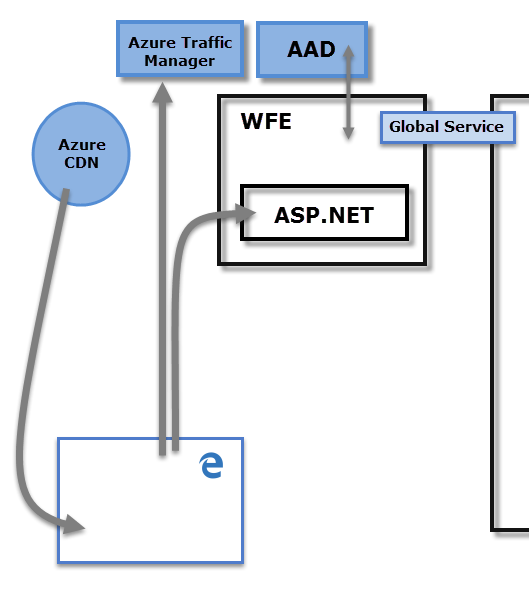
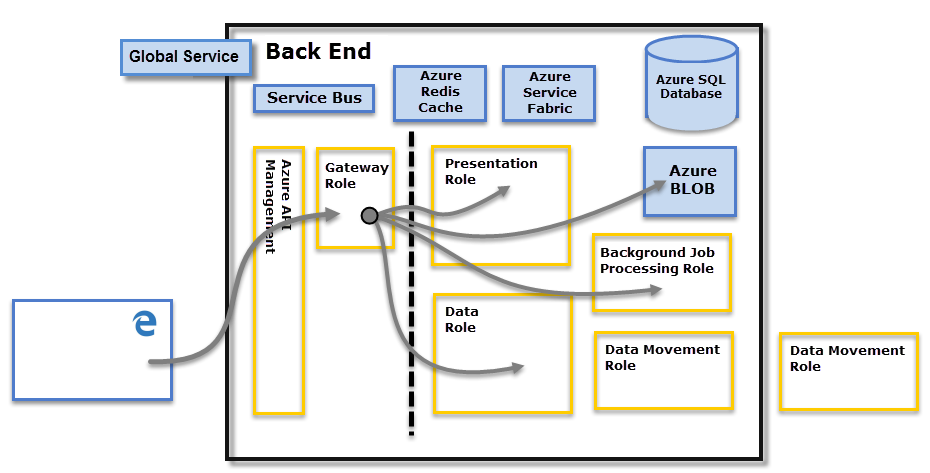
後端叢集會決定已驗證的用戶端如何與 Power BI 服務 互動。 後端叢集會管理視覺效果、用戶儀錶板、語意模型、報表、數據儲存區、數據連線、數據重新整理,以及與 Power BI 服務 互動的其他層面。 閘道角色可作為使用者要求與 Power BI 服務 之間的閘道。 使用者不會直接與閘道角色以外的任何角色互動。 Azure API 管理 最終會處理閘道角色。
重要
只有 Azure API 管理 和閘道角色可透過公用因特網存取。 它們提供驗證、授權、DDoS 保護、節流、負載平衡、路由和其他功能。
數據 儲存體 安全性
Power BI 使用兩個主要存放庫來儲存和管理數據:
- 從用戶上傳的數據通常會傳送至 Azure Blob 儲存體。
- 所有元數據,包括系統本身的專案都會儲存在 Azure SQL 資料庫 中。
後端叢集圖中顯示的虛線,釐清兩個元件之間的界限,這些元件可由點線左邊顯示的使用者存取。 只有系統可存取的角色會顯示在右側。 當已驗證的用戶連線到Power BI服務時,客戶端的連線和任何要求都會由 閘道角色 接受和管理,然後代表使用者與Power BI 服務的其餘部分互動。 例如,當用戶端嘗試檢視儀錶板時, 閘道角色 會接受該要求,然後個別傳送要求給 簡報角色 ,以擷取瀏覽器顯示儀錶板所需的數據。 最後,Azure API 管理 會處理連線和用戶端要求。
使用者驗證
Power BI 會使用 Microsoft Entra 識別符來驗證登入 Power BI 服務 的使用者。 每當用戶嘗試存取安全資源時,都需要登入認證。 使用者使用他們建立Power BI帳戶的電子郵件位址登入 Power BI 服務。 每當使用者嘗試連線到數據時,Power BI 會使用與有效使用者名稱相同的認證,並將它傳遞給資源。 然後有效的 使用者 名稱會對應至 用戶主體名稱 ,並解析為套用驗證的相關聯 Windows 網域帳戶。
例如 david@contoso.com,對於使用Power BI 登入工作電子郵件地址的組織而言, UPN 對應的有效使用者名稱 很簡單。 對於未使用工作電子郵件地址的組織,例如 david@contoso.onmicrosoft.com ,Microsoft Entra ID 與內部部署認證之間的對應需要 目錄同步 處理才能正常運作。
Power BI 的平台安全性也包含多租用戶環境安全性、網路安全性,以及新增其他 Microsoft Entra ID 型安全性措施的能力。
數據和服務安全性
如需詳細資訊,請參閱 在信任上執行的 Microsoft 信任中心、產品和服務。
如先前所述,內部部署AD伺服器會使用Power BI登入對應至UPN以取得認證。 不過,用戶必須瞭解其共享數據的敏感度。 在您安全地連線到數據源,然後與其他人共享報表、儀錶板或語意模型之後,收件者就會獲得報表的存取權。 收件者不需要登入數據源。
例外狀況是使用內部部署數據網關連線到 SQL Server Analysis Services。 儀錶板會在Power BI中快取,但存取基礎報表或語意模型會針對嘗試存取報表或語意模型的每個使用者起始驗證。 只有在使用者有足夠的認證存取數據時,才會授與存取權。 如需詳細資訊,請參閱 深入的內部部署數據閘道。
強制執行 TLS 版本使用方式
網路和IT系統管理員可以強制要求使用目前傳輸層安全性 (TLS) 在其網路上的任何安全通訊。 Windows 透過 Microsoft 通道提供者提供 TLS 版本的支援,如需詳細資訊,請參閱 TLS/SSL 中的通訊協定(安全通道 SSP)。
這項強制執行是透過系統管理方式設定登錄機碼來實作。 如需強制執行詳細數據,請參閱 管理 AD FS 的 SSL/TLS 通訊協定和加密套件。
Power BI Desktop 需要 TLS(傳輸層安全性)1.2 版(或更新版本)來保護您的端點。 使用 TLS 1.2 之前 TLS 版本的網頁瀏覽器和其他用戶端應用程式將無法連線。 如果需要較新版本的 TLS,Power BI Desktop 會遵守這些文章中所述的登錄機碼設定,而且只會建立符合根據這些登錄設定允許之 TLS 版本需求的連線。如果有的話。
如需設定這些登錄機碼的詳細資訊,請參閱 傳輸層安全性 (TLS) 登錄設定。
意見反應
即將登場:在 2024 年,我們將逐步淘汰 GitHub 問題作為內容的意見反應機制,並將它取代為新的意見反應系統。 如需詳細資訊,請參閱:https://aka.ms/ContentUserFeedback。
提交並檢視相關的意見反應