TPM 金鑰證明
適用於:Windows Server 2022、Windows Server 2019、Windows Server 2016、Windows Server 2012 R2、Windows Server 2012
作者:Windows 群組資深支援呈核工程師 Justin Turner
注意
本內容由 Microsoft 客戶支援工程師編寫,適用對象為經驗豐富的系統管理員和系統架構師,如果 TechNet 提供的主題已無法滿足您,您要找的是 Windows Server 2012 R2 中功能和解決方案的更深入技術講解,則您是本文的適用對象。 不過,本文未經過相同的編輯階段,因此部分語句也許不如 TechNet 文章那樣洗鍊。
概觀
雖然自 Windows 8 以來已支援受 TPM 保護的金鑰,但 CA 沒有機制可以密碼編譯方式證明憑證要求者私密金鑰實際上受到信賴平台模組 (TPM) 的保護。 此更新可讓 CA 執行該證明,並在發行的憑證中反映該證明。
注意
本文假設讀者熟悉憑證範本概念 (如需參考,請參閱憑證範本)。 其中也假設讀者熟悉如何設定企業 CA 以根據憑證範本發行憑證 (如需參考,請參閱檢查清單:設定 CA 以發行和管理憑證)。
辭彙
| 詞彙 | 定義 |
|---|---|
| EK | 簽署金鑰。 這是 TPM 內所包含的非對稱金鑰 (在製造時間插入)。 EK 對於每個 TPM 都是唯一的,而且可以予以識別。 EK 無法變更或移除。 |
| EKpub | 表示 EK 的公開金鑰。 |
| EKPriv | 表示 EK 的私密金鑰。 |
| EKCert | EK 憑證。 EKPub 的 TPM 製造商發行憑證。 並非所有 TPM 都有 EKCert。 |
| TPM | 信賴平台模組。 TPM 是設計來提供硬體式的安全性相關功能。 TPM 晶片是一種安全的密碼編譯處理器,其設計目的是執行密碼編譯作業。 此晶片包含多個實體安全性機制,使得它具備防竄改功能,在 TPM 安全性功能的加持下,惡意程式碼軟體便無法進行竄改。 |
背景
從 Windows 8 開始,可以使用信賴平台模組 (TPM) 來保護憑證的私密金鑰。 Microsoft 平台密碼編譯提供者金鑰儲存提供者 (KSP) 會啟用此功能。 實作有兩個考量:
無法保證金鑰實際上受到 TPM 保護 (有人可以輕鬆地詐騙軟體 KSP 作為具有本機系統管理員認證的 TPM KSP)。
無法限制允許保護企業發行憑證的 TPM 清單 (如果 PKI 系統管理員想要控制可用於在環境中取得憑證的裝置類型)。
TPM 金鑰證明
TPM 金鑰證明是實體要求憑證以密碼編譯方式向 CA 證明憑證要求中的 RSA 金鑰受到 CA 所信任「某個」或「特定」TPM 所保護的能力。 本文稍後的部署概觀一節會進一步討論 TPM 信任模型。
為什麼 TPM 金鑰證明很重要?
具有 TPM 證明金鑰的使用者憑證可提供更高的安全性保證、由 TPM 提供金鑰的不可匯出性、不受 hammer 命令影響以及隔離所支援。
透過 TPM 金鑰證明,現在可以使用新的管理架構:系統管理員可以定義一組裝置,讓使用者可用來存取公司資源 (例如 VPN 或無線存取點),並具有無法用來存取其他裝置的強式保證。 這個新的存取控制架構屬於強式,因為其繫結至硬體繫結的使用者身分識別,而其比軟體型認證更強。
TPM 金鑰證明如何運作?
一般而言,TPM 索引鍵證明是以下列要素為基礎:
每個 TPM 都會隨附唯一的非對稱金鑰,稱為簽署金鑰 (EK),由製造商燒錄。 我們將此金鑰的公用部分稱為 EKPub,並將相關聯的私密金鑰稱為 EKPriv。 某些 TPM 晶片也有由製造商針對 EKPub 發行的 EK 憑證。 我們將此憑證稱為 EKCert。
CA 會透過 EKPub 或 EKCert 在 TPM 中建立信任。
使用者需要向 CA 證明要求憑證的 RSA 金鑰會以密碼編譯方式與 EKPub 相關,且使用者擁有 EKpriv。
CA 會發行具有特殊發行原則 OID 的憑證,表示金鑰現在已證明受 TPM 保護。
部署概觀
在此部署中,假設已設定 Windows Server 2012 R2 企業 CA。 此外,用戶端 (Windows 8.1) 也會設定為使用憑證範本針對該企業 CA 進行註冊。
部署 TPM 金鑰證明有三個步驟:
規劃 TPM 信任模型:第一個步驟是決定要使用的 TPM 信任模型。 有 3 種支援的方法來執行這項操作:
以使用者認證為基礎的信任:企業 CA 會將使用者提供的 EKPub 信任為憑證要求的一部分,而且不會執行使用者網域認證以外的驗證。
以 EKCert 為基礎的信任:企業 CA 會根據可接受的 EK 憑證鏈結清單,驗證憑證要求期間所提供的 EKCert 鏈結。 可接受的鏈結是根據每個製造商所定義,並透過發行 CA 上的兩個自訂憑證存放區來表示 (一個存放區用於中繼,另一個用於根 CA 憑證)。 此信任模式表示來自指定製造商的所有 TPM 都會受到信任。 請注意,在此模式中,環境中使用的 TPM 必須包含 EKCerts。
以 EKPub 為基礎的信任:企業 CA 會驗證在憑證要求期間所提供的 EKPub 是否出現在受系統管理員管理的允許 EKPubs 清單中。 此清單會以檔案目錄表示,其中此目錄中每個檔案的名稱是允許的 EKPub 的 SHA-2 雜湊。 此選項提供最高保證層級,但需要更多系統管理工作,因為每個裝置都會個別進行識別。 在此信任模型中,只有已將其 TPM 的 EKPub 新增至允許的 EKPub 清單的裝置,才允許註冊 TPM 證明的憑證。
根據所使用的方法,CA 會將不同的發行原則 OID 套用至發行的憑證。 如需發行原則 OID 的詳細資料,請參閱本文中設定憑證範本一節中的發行原則 OID 資料表。
請注意,您可以選擇 TPM 信任模型的組合。 在此情況下,CA 會接受任何證明方法,而發行原則 OID 會反映所有成功的證明方法。
設定憑證範本:本文的部署詳細資料一節將說明設定憑證範本。 本文未涵蓋如何將此憑證範本指派給企業 CA,或如何將註冊存取權指定給一組使用者。 如需詳細資訊,請參閱檢查清單:將 CA 設定為發行和管理憑證。
設定 TPM 信任模型的 CA
以使用者認證為基礎的信任:不需要特定設定。
以 EKCert 為基礎的信任:系統管理員必須從 TPM 製造商取得 EKCert 鏈結憑證,並將其匯入至系統管理員在執行 TPM 金鑰證明的 CA 上所建立兩個新的憑證存放區。 如需詳細資訊,請參閱本文中的 CA 組態一節。
以 EKPub 為基礎的信任:系統管理員必須取得每個需要 TPM 證明憑證的裝置 EKPub,並將其新增至允許的 EKPubs 清單。 如需詳細資訊,請參閱本文中的 CA 組態一節。
注意
- 此功能需要 Windows 8.1/Windows Server 2012 R2。
- 不支援協力廠商智慧卡 KSP 的 TPM 金鑰證明。 必須使用 Microsoft 平台密碼編譯提供者 KSP。
- TPM 金鑰證明僅適用於 RSA 金鑰。
- 獨立 CA 不支援 TPM 金鑰證明。
- TPM 金鑰證明不支援非持續性憑證處理。
部署詳細資料
設定憑證範本
若要設定 TPM 金鑰證明的憑證範本,請執行下列設定步驟:
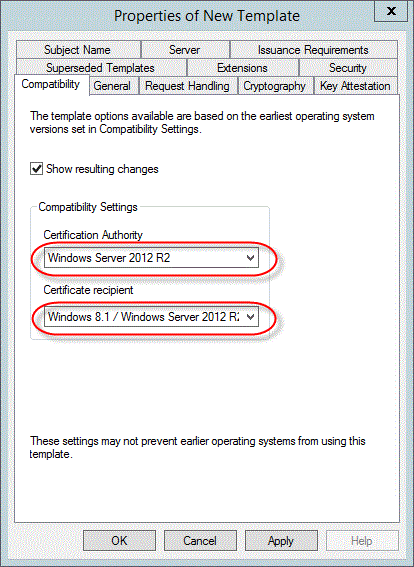
[相容性] 索引標籤
在 [相容性設定] 區段中:
確定已針對 [憑證授權單位] 選取 [Windows Server 2012 R2]。
確定已針對 [憑證接收者] 選取 [Windows 8.1/Windows Server 2012 R2]。
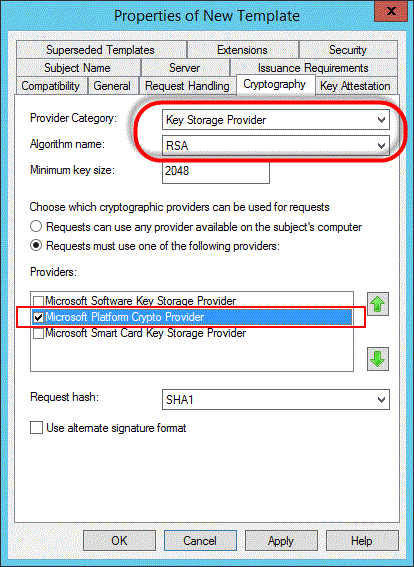
[密碼編譯] 索引標籤
確定已針對 [提供者類別] 選取 [金鑰儲存提供者],並針對 [演算法名稱] 選取 [RSA]。 確定 [要求必須使用下列其中一個提供者],並在 [提供者] 底下選取 [Microsoft 平台密碼編譯提供者] 選項。
[金鑰證明] 索引標籤
這是 Windows Server 2012 R2 的新索引標籤:
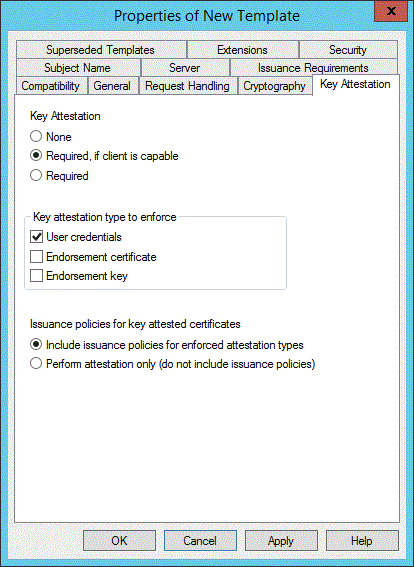
從三個可能的選項中選擇證明模式。
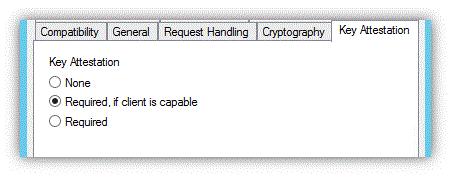
無:表示不得使用金鑰證明
支援用戶端時必要:允許不支援 TPM 金鑰證明裝置上的使用者繼續註冊該憑證。 可以執行證明的使用者將會使用特殊發行原則 OID 來區分。 某些裝置可能無法執行證明,因為舊的 TPM 不支援金鑰證明,或裝置完全沒有 TPM。
必要:用戶端必須執行 TPM 金鑰證明,否則憑證要求將會失敗。
然後選擇 TPM 信任模型。 這也有三個選項:
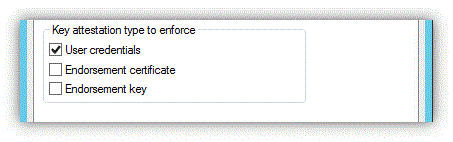
使用者認證:藉由指定其網域認證,允許驗證使用者確認有效的 TPM。
簽署憑證:裝置的 EKCert 必須透過系統管理員管理的 TPM 中繼 CA 憑證向系統管理員管理的根 CA 憑證進行驗證。 如果您選擇此選項,您必須在發行 CA 上設定 EKCA 和 EKRoot 憑證存放區,如本文的 CA 組態一節中所述。
簽署金鑰:裝置的 EKPub 必須出現在 PKI 系統管理員管理的清單中。 此選項提供最高保證層級,但需要更多系統管理工作。 如果您選擇此選項,則必須在發行 CA 上設定 EKPub 清單,如本文的 CA 組態一節中所述。
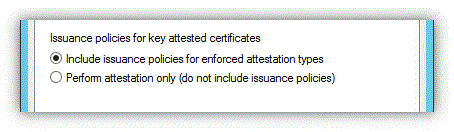
最後,決定要在發行憑證中顯示的發行原則。 根據預設,每個強制類型都有相關聯的物件識別碼 (OID),如果憑證通過該強制類型,則會插入憑證,如下表所述。 請注意,您可以選擇強制方法的組合。 在此情況下,CA 會接受任何證明方法,而發行原則 OID 會反映所有成功的證明方法。
發行原則 OID
OID 金鑰證明類型 描述 保證層級 1.3.6.1.4.1.311.21.30 EK 「EK 已驗證」:適用於系統管理員管理的 EK 清單 高 1.3.6.1.4.1.311.21.31 簽署憑證 「EK 憑證已驗證」:驗證 EK 憑證鏈結時 中 1.3.6.1.4.1.311.21.32 使用者認證 「使用時受信任的 EK」:適用於使用者證明的 EK 低 如果已選取 [包含發行原則] (預設選項),則會將 OID 插入已發行的憑證中。
提示
憑證中有 OID 的其中一個可能用途是限制特定裝置的 VPN 或無線網路存取。 例如,如果憑證中有 OID 1.3.6.1.4.1.311.21.30,您的存取原則可能會允許連線 (或存取不同的 VLAN)。 這可讓您限制對 TPM EK 存在於 EKPUB 清單中的裝置存取。
CA 組態
在發行 CA 上設定 EKCA 和 EKROOT 憑證存放區
如果您選擇範本設定的簽署憑證,請執行下列設定步驟:
使用 Windows PowerShell 在將執行 TPM 金鑰證明的憑證授權單位 (CA) 伺服器上建立兩個新的憑證存放區。
從您想要在企業環境中允許的製造商取得中繼和根 CA 憑證。 這些憑證必須視需要匯入先前建立的憑證存放區 (EKCA 和 EKROOT)。
下列 Windows PowerShell 指令碼會執行這兩個步驟。 在下列範例中,TPM 製造商 Fabrikam 已提供根憑證 FabrikamRoot.cer 和發行 CA 憑證 Fabrikamca.cer。
PS C:>\cd cert: PS Cert:\>cd .\\LocalMachine PS Cert:\LocalMachine> new-item EKROOT PS Cert:\ LocalMachine> new-item EKCA PS Cert:\EKCA\copy FabrikamCa.cer .\EKCA PS Cert:\EKROOT\copy FabrikamRoot.cer .\EKROOT如果使用 EK 證明類型,請設定 EKPUB 清單
如果您選擇範本設定中的簽署金鑰,接下來的設定步驟是在發行 CA 上建立和設定資料夾,其中包含 0 位元組檔案,每個檔案都針對允許 EK 的 SHA-2 雜湊命名。 此資料夾可作為允許取得 TPM 金鑰證明憑證之裝置的「允許清單」。 因為您必須針對每個需要證明憑證的裝置手動新增 EKPUB,所以其會為企業提供獲授權取得 TPM 金鑰證明憑證的裝置保證。 設定此模式的 CA 需要兩個步驟:
建立 EndorsementKeyListDirectories 登錄項目:使用 Certutil 命令列工具來設定定義受信任 EKpubs 的資料夾位置,如下表所述。
作業 命令語法 新增資料夾位置 certutil.exe -setreg CA\EndorsementKeyListDirectories +"<folder>" 移除資料夾位置 certutil.exe -setreg CA\EndorsementKeyListDirectories -"<folder>" certutil 命令中的 EndorsementKeyListDirectories 是登錄設定,如下表所述。
值名稱 類型 資料 EndorsementKeyListDirectories REG_MULTI_SZ <EKPUB 允許清單的 LOCAL 或 UNC 路徑> 範例:
\\blueCA.contoso.com\ekpub
\\bluecluster1.contoso.com\ekpub
D:\ekpub
HKLM\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration\<CA Sanitized Name>
EndorsementKeyListDirectories 將包含 UNC 或本機檔案系統路徑的清單,每個路徑都指向 CA 具有讀取權限的資料夾。 每個資料夾可能包含零或多個允許清單項目,其中每個項目都是名稱為受信任 EKpub 之 SHA-2 雜湊的檔案,且沒有副檔名。 建立或編輯此登錄機碼組態需要重新啟動 CA,就像現有的 CA 登錄組態設定一樣。 不過,對組態設定的編輯將會立即生效,且不需要重新啟動 CA。
重要
藉由設定權限來保護清單中的資料夾以避免竄改和未經授權的存取,讓只有授權的系統管理員具有讀取和寫入權限。 CA 的電腦帳戶僅需要讀取存取權。
填入 EKPUB 清單:使用下列 Windows PowerShell Cmdlet,在每個裝置上使用 Windows PowerShell 取得 TPM EK 的公開金鑰雜湊,然後將此公開金鑰雜湊傳送至 CA,並將其儲存在 EKPubList 資料夾中。
PS C:>\$a=Get-TpmEndorsementKeyInfo -hashalgorithm sha256 PS C:>$b=new-item $a.PublicKeyHash -ItemType file
疑難排解
憑證範本上無法使用金鑰證明欄位
如果範本設定不符合證明的需求,則無法使用 [金鑰證明] 欄位。 兩個常見原因:
相容性設定未正確設定。 請確定其已設定如下:
憑證授權單位:Windows Server 2012 R2
憑證接收者:Windows 8.1/Windows Server 2012 R2
密碼編譯設定未正確設定。 請確定其已設定如下:
提供者類別目錄:金鑰儲存提供者
演算法名稱:RSA
提供者:Microsoft 平台密碼編譯提供者
要求處理設定未正確設定。 請確定其已設定如下:
不得選取 [允許匯出私密金鑰] 選項。
不得選取 [封存主體的加密金鑰] 選項。
驗證 TPM 裝置以進行證明
使用 Windows PowerShell Cmdlet Confirm-CAEndorsementKeyInfo 來驗證特定 TPM 裝置是否受到 CA 可用於證明的信任。 有兩個選項:一個用於驗證 EKCert,另一個選項用於驗證 EKPub。 Cmdlet 是在本機 CA 上執行,或使用 Windows PowerShell 遠端處理在遠端 CA 上執行。
若要驗證 EKPub 上的信任,請執行下列兩個步驟:
從用戶端電腦擷取 EKPub:EKPub 可透過 Get-TpmEndorsementKeyInfo 從用戶端電腦擷取。 在提升權限的命令提示字元中,執行下列動作:
PS C:>\$a=Get-TpmEndorsementKeyInfo -hashalgorithm sha256確認 CA 電腦上的 EKCert 信任:將擷取的字串 (EKPub 的 SHA-2 雜湊) 複製到伺服器 (例如透過電子郵件),並將其傳遞至 Confirm-CAEndorsementKeyInfo Cmdlet。 請注意,此參數必須是 64 個字元。
Confirm-CAEndorsementKeyInfo [-PublicKeyHash] <string>
若要驗證 EKCert 上的信任,請執行下列兩個步驟:
從用戶端電腦擷取 EKCert:EKCert 可透過 Get-TpmEndorsementKeyInfo 從用戶端電腦擷取。 在提升權限的命令提示字元中,執行下列動作:
PS C:>\$a=Get-TpmEndorsementKeyInfo PS C:>\$a.manufacturerCertificates|Export-Certificate -filepath c:\myEkcert.cer確認 CA 電腦上的 EKCert 信任:將擷取的 EKCert (EkCert.cer) 複製到 CA (例如,透過電子郵件或 xcopy)。 例如,如果您複製 CA 伺服器上「c:\diagnose」資料夾的憑證檔案,請執行下列命令以完成驗證:
PS C:>new-object System.Security.Cryptography.X509Certificates.X509Certificate2 "c:\diagnose\myEKcert.cer" | Confirm-CAEndorsementKeyInfo