使用 AD FS 將 Microsoft Entra 多重因子驗證配置為驗證業者
本文中的資訊適用於 Windows 2016 和更新版本。
如果貴公司已和 Microsoft Entra ID 成立聯盟,即可使用 Microsoft Entra 多重因子驗證功能保障 Active Directory Federation Services (AD FS) 資源在內部部署和雲端的安。 Microsoft Entra 多重因子驗證功能讓您消除密碼,提供更安全的驗證方式。 憑藉 AD FS,您可以為主要驗證配置 Microsoft Entra 多重因子驗證,或將其當成額外驗證業者。
有別於 Windows Server 2012 R2 的 AD FS,AD FS 2016 Microsoft Entra 多重因子驗證轉換程式直接與 Microsoft Entra ID 整合,不需要內部部署 Azure 多重因子驗證伺服器。 Microsoft Entra 多重因子驗證轉換程式內建於 Windows Server 2016 中。 不需另外安裝。
藉由使用 AD FS 讓使用者註冊 Microsoft Entra ID 多重因子驗證
AD FS 不支援 Microsoft Entra 多重因子驗證資安核驗資訊的內聯 “校對” 註冊,例如電話號碼或行動裝置應用程式。 在不支援內聯校對情況下,使用者必須先造訪https://account.activedirectory.windowsazure.com/Proofup.aspx後才能使用 Microsoft Entra 多重因子驗證功能,驗證 AD FS 應用程式身份。 尚未在 Microsoft Entra ID 校對過的使用者嘗試在 AD FS 以 Microsoft Entra 多重因子驗證功能進行身份驗證時,他們會收到 AD FS 錯誤訊息。 身為 AD FS 系統管理員,您可以自訂此錯誤體驗,改為引導使用者前往證明頁面。 您可以使用 onload.js 自訂來建立此訊息,以偵測 AD FS 頁面中的錯誤訊息字串。 然後,您可以顯示新的訊息,引導使用者前往 https://aka.ms/mfasetup,讓他們重新嘗試驗證。 如需詳細資訊,請參閱自訂 AD FS 網頁,以引導使用者註冊 MFA 驗證方法。
注意
這個更新版之前,使用者必須使用 Microsoft Entra 多重因子驗證進行身份驗證,才能藉由造訪 https://account.activedirectory.windowsazure.com/Proofup.aspx進行註冊。 憑藉這次的更新版,尚未註冊 Microsoft Entra 多重因子驗證核驗資訊的 AD FS 使用者可以使用只有主要驗證功能的快速鍵 https://aka.ms/mfasetup,例如 Windows 整合身份驗證或 AD FS 網頁上的使用者名和密碼,存取 Azure 校對頁面。 如果使用者尚未配置核驗方法,Microsoft Entra ID 會執行內聯註冊。 使用者會看到以下訊息,"您的管理員已經要求您設定此帳戶進行其他資安核驗。" 然後使用者選取現在立即設定。造訪校對頁面時,已經配置至少一種核驗方法的使用者仍會接獲須提供多重因子驗證 (MFA) 的提示。
建議的部署拓撲
本節涵蓋把 Microsoft Entra 多重因子驗證當成 AD FS 和 Office 365 的 Microsoft Entra 多重因子驗證中,主要的驗證方法。
Microsoft Entra 多重因子驗證即為主要驗證
使用 Microsoft Entra 多重因子驗證當成 AD FS 主要驗證有幾個很好的理由:
- 它避免登入 Microsoft Entra ID、Office 365 和其他 AD FS 應用程式的密碼。
- 透過要求另一項要素來保護密碼型登入,例如密碼之前的驗證碼。
您可能也想要把 Microsoft Entra 多重因子驗證當作主要驗證方法和 Microsoft Entra 條件式存取方法使用,包括藉由提示其他因子的真實 MFA。 若要以內部部署方式使用 Microsoft Entra 多重因子驗證,您可以藉由把SupportsMfa設定為$true的方式配置 Microsoft Entra 網域設定。 在這個配置中,Microsoft Entra ID 會提示 AD FS 針對需要它的條件式存取方案執行額外驗證或 "真實 MFA"。
任何尚未註冊的 AD FS 使用者 (尚未設定 MFA 驗證資訊),都應該提示其設定驗證資訊。 若要提示未註冊的使用者,您可以使用自訂的 AD FS 錯誤頁面,將使用者導向 https://aka.ms/mfasetup 並設定驗證資訊。 設定之後,使用者可以重新嘗試其 AD FS 登入。
扮演主要驗證角色的 Microsoft Entra 多重因子驗證被視為單一因素。 初始配置后,使用者需要提供另一個因素來管理或更新 Microsoft Entra ID 的驗證資訊,或存取需要 MFA 的其他資源。
注意
使用 AD FS 2019 時,您必須修改 Active Directory 宣告提供者信任的錨點宣告類型,並將其從 windowsaccountname 修改為使用者主體名稱 (UPN)。 執行下列 PowerShell Cmdlet。 這不會影響 AD FS 伺服器陣列的內部運作。 在進行這項變更之後,可能會重新提示一些使用者進行憑證。 再次登入之後,終端使用者將看不到任何差異。
Set-AdfsClaimsProviderTrust -AnchorClaimType "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn" -TargetName "Active Directory"
Microsoft Entra 多重因子驗證可當成 Office 365 的額外驗證工具
適用 AD FS 的 Microsoft Entra 多重因子驗證轉換程式讓您的使用者在 AD FS 執行 MFA。 若要保障您的 Microsoft Entra 資源安全,您應詃要求透過條件式存取政策執行 MFA。 您也必須將網域設定 SupportsMfa 設定為 $true,並在使用者成功執行雙步驟驗證時發出 multipleauthn 宣告 。
如前所述,任何尚未註冊的 AD FS 使用者 (尚未設定 MFA 驗證資訊),都應該提示其設定驗證資訊。 若要提示未註冊的使用者,您可以使用自訂的 AD FS 錯誤頁面,將使用者導向 https://aka.ms/mfasetup 並設定驗證資訊。 設定之後,使用者可以重新嘗試其 AD FS 登入。
必要條件
當您將 Microsoft Entra 多重因子驗證用於 AD FS 驗證時,以下是必要的先決條件:
- 含有 Microsoft Entra ID 的 Azure 訂閱。
- Microsoft Entra 多重因子驗證。
注意
Microsoft Entra ID 和 Microsoft Entra 多重因子驗證含在 Microsoft Entra ID P1 或 P2 和 Enterprise Mobility Suite (EMS) 裡。 如果您已安裝其中一個應用程式,就不需要個別訂閱帳戶。
- Windows Server 2016 AD FS 內部部署環境。
- 伺服器必須能透過 443 連接埠與下列 URL 通訊。
https://adnotifications.windowsazure.comhttps://login.microsoftonline.com
- 伺服器必須能透過 443 連接埠與下列 URL 通訊。
- 您的內部部署環境必須與 Microsoft Entra ID 建立聯盟。
- 適用 Windows PowerShell 的 Microsoft Azure Active Directory 模組。
- 在您的 Microsoft Entra ID 執行個體上的全域管理員權限,可借助 Azure AD PowerShell 配置。
- 企業管理員憑證用來配置 Microsoft Entra 多重因子驗證專用 AD FS 農場。
注意
自 2024 年 3 月 30 日起,Azure AD 和 MSOnline PowerShell 模組已被淘汰。 若要深入了解,請閱讀淘汰更新。 在此日期之後,對這些模組的支援僅限於對 Microsoft Graph PowerShell SDK 的移轉協助和安全性修正。 淘汰的模組將繼續運作至 2025 年 3 月 30 日。
我們建議移轉至 Microsoft Graph PowerShell 以與 Microsoft Entra ID (以前稱為 Azure AD) 互動。 如需了解常見的移轉問題,請參閱移轉常見問題。 注意:MSOnline 1.0.x 版可能會在 2024 年 6 月 30 日之後發生中斷。
設定 AD FS 伺服器
若要完成 AD FS 的 Microsoft Entra 多重因子驗證的配置,您需要借助這裡描述的步驟配置每個 AD FS 伺服器。
注意
請確定對伺服器陣列中的所有 AD FS 伺服器執行這些步驟。 如果您的伺服器陣列中有多個 AD FS 伺服器,您可以使用 Azure AD PowerShell 從遠端執行必要的設定。
步驟 1:在每個 AD FS 伺服器上為 Microsoft Entra 多重因子驗證產生證書
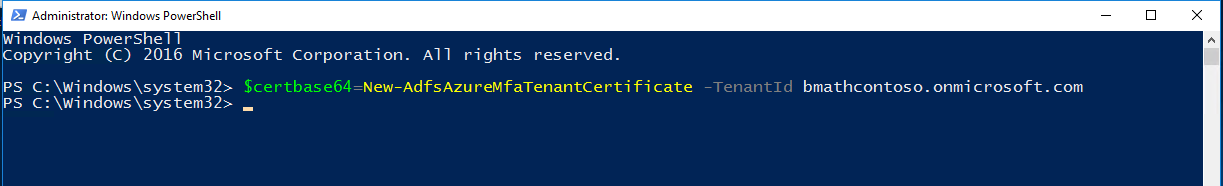
您需要做的第一件事是使用 New-AdfsAzureMfaTenantCertificate PowerShell 指令產生 Microsoft Entra 多重因子驗證使用的證書。 產生憑證之後,請在本機電腦憑證存放區中找出憑證。 證書已標註包含 Microsoft Entra 目錄適用的 TenantID 主旨名稱。

TenantID 是 Microsoft Entra ID 裡,您的目錄名稱。 使用下列 PowerShell cmdlet 產生新憑證:
$certbase64 = New-AdfsAzureMfaTenantCertificate -TenantID <tenantID>
步驟 2:將新憑證加至 Azure 多重因子驗證 Client Service Principal
若要促使 AD FS 伺服器與 Azure 多重因子驗證客戶端通訊,您需要將憑證加至 Azure 多重因子驗證客戶端的 Service Principal。 使用 New-AdfsAzureMFaTenantCertificate cmdlet 所產生的憑證會作為這些憑證。 打開 PowerShell 並執行以下步驟,將新憑證加至 Azure 多重因子驗證 Client Service Principal。
步驟 3:針對 Azure 多重因子驗證客戶端將證書設定為新憑證
注意
若要完成這道步驟,您需要使用 Connect-MgGraph將您的 Microsoft Entra ID 執行個體與 Microsoft Graph PowerShell 連接。 這些步驟假設您已透過 PowerShell 連線。
Connect-MgGraph -Scopes 'Application.ReadWrite.All'
$servicePrincipalId = (Get-MgServicePrincipal -Filter "appid eq '981f26a1-7f43-403b-a875-f8b09b8cd720'").Id
$keyCredentials = (Get-MgServicePrincipal -Filter "appid eq '981f26a1-7f43-403b-a875-f8b09b8cd720'").KeyCredentials
$certX509 = [System.Security.Cryptography.X509Certificates.X509Certificate2]([System.Convert]::FromBase64String($certBase64))
$newKey = @(@{
CustomKeyIdentifier = $null
DisplayName = $certX509.Subject
EndDateTime = $null
Key = $certX509.GetRawCertData()
KeyId = [guid]::NewGuid()
StartDateTime = $null
Type = "AsymmetricX509Cert"
Usage = "Verify"
AdditionalProperties = $null
})
$keyCredentials += $newKey
Update-MgServicePrincipal -ServicePrincipalId $servicePrincipalId -KeyCredentials $keyCredentials
重要
此命令必須在伺服器陣列中的所有 AD FS 伺服器上執行。 證書一直未設定為 Azure 多重因子驗證用戶端專用的新憑證伺服器上,Microsoft Entra 多重因子驗證將會失敗。
注意
981f26a1-7f43-403b-a875-f8b09b8cd720 是 Azure 多重因子驗證客戶端的 GUID。
設定 AD FS 伺服器陣列
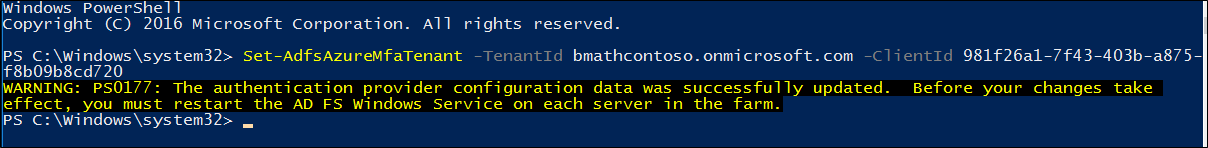
針對每個 AD FS 伺服器完成上一節中的步驟之後,請使用 Set-AdfsAzureMfaTenant Cmdlet 設定 Azure 租用戶資訊。 只需要針對 AD FS 伺服器陣列執行一次此 Cmdlet。
開啟 PowerShell,並使用 Set-AdfsAzureMfaTenant Cmdlet 輸入您自己的 tenantId。 針對使用 Microsoft Azure Government 雲端的客戶,新增 -Environment USGov 參數:
注意
您必須在伺服器陣列中的每個伺服器上重新啟動 AD FS 服務,這些變更才會生效。 為了將影響降到最低,請一次讓一個 AD FS 伺服器退出 NLB 輪替,等待直到所有連線清空。
Set-AdfsAzureMfaTenant -TenantId <tenant ID> -ClientId 981f26a1-7f43-403b-a875-f8b09b8cd720
非最新 Service Pack 的 Windows Server 不支援 Set-AdfsAzureMfaTenant Cmdlet 的 -Environment 參數。 如果您使用 Azure Government 雲端,且先前的步驟因缺少 -Environment 參數而無法設定 Azure 租用戶,請完成下列步驟手動建立登錄專案。 如果先前的 Cmdlet 已正確登錄您的租用戶資訊,或您不在 Azure Government 雲端中,請略過這些步驟:
在 AD FS 伺服器上開啟登錄編輯程式 。
瀏覽至 HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ADFS。 建立下列的登錄機碼值:
登錄機碼 值 SasUrl https://adnotifications.windowsazure.us/StrongAuthenticationService.svc/ConnectorStsUrl https://login.microsoftonline.usResourceUri https://adnotifications.windowsazure.us/StrongAuthenticationService.svc/Connector在伺服器陣列中的每個伺服器上重新啟動 AD FS 服務,這些變更才會生效。 為了降低對系統的影響,請一次讓一個 AD FS 伺服器退出 NLB 輪替,等待直到所有連線清空。
這道步驟完成後,您會看見 Microsoft Entra 多重因子驗證可當作企業內部網路和外部網路使用的主要驗證方法。
![[編輯驗證方法] 對話方塊的螢幕擷取畫面,其中顯示 [外部網络] 和 [內部網络] 區段中醒目提示的 Microsoft Entra 多重要素驗證選項。](media/configure-ad-fs-2016-and-azure-mfa/adfs_azuremfa6.png)
如果您要把 Microsoft Entra 多重因子驗證當作輔助驗證方法使用,請在編輯驗證方法方塊上選取多重因子索引標籤 (AD FS 2019 的附加索引標籤) 並確保它已經啟用。 否則,您可能會收到錯誤訊息,例如「找不到有效的增強式驗證方法。 請連絡您的系統管理員,以設定並啟用適當的增強式驗證提供者。」
續約和管理 AD FS Microsoft Entra 多重因子驗證證書
以下指南著眼於幫助您管理 AD FS 伺服器上的 Microsoft Entra 多重因子驗證證書。
當您使用 Microsoft Entra 多重因子驗證配置 AD FS 時,預設透過 New-AdfsAzureMfaTenantCertificatePowerShell cmdlet 產生的證書有效期兩年。 若要判斷憑證到期時間有多接近,以及更新並安裝新的憑證,請使用下列程序。
評估 AD FS Microsoft Entra 多重因子驗證證書到期日。
在每台 AD FS 伺服器上,本機電腦我的商店中,核發者和主旨區有一份自行簽署證書,其中含有 "Microsoft AD FS Microsoft Entra 多重因子驗證"。 這份證書是 Microsoft Entra 多重因子驗證證書。 檢查每個 AD FS 伺服器上此憑證的有效期間,以判斷到期日。
在每台 AD FS 伺服器上創造新 AD FS Microsoft Entra 多重因子驗證證書。
如果您的證書效期即將結束,請藉由在每台 AD FS 伺服器上產生新 Microsoft Entra 多重因子驗證證書來啟動續約流程。 在 PowerShell 中,使用下列 Cmdlet 在每個 AD FS 伺服器上產生新的憑證:
警告
如果您的憑證已經過期,請勿將
-Renew $true參數新增至下列命令。 在此案例中,現有的過期憑證會換成新的憑證,而不是繼續保留,並建立其他憑證。$newcert = New-AdfsAzureMfaTenantCertificate -TenantId <tenant id such as contoso.onmicrosoft.com> -Renew $true如果憑證尚未過期,命令會產生新的憑證,該憑證的有效期間為從當天過兩天到兩年後再加兩天。 執行 cmdlet 或續約證書時,AD FS 和 Microsoft Entra 多重因子驗證操作不受影響。 兩天的延遲是有意的,它在 AD FS 開始使用新證書進行 Microsoft Entra 多重因子驗證前,提供時間按照後續步驟在租用戶中配置新證書。
在 Microsoft Entra 租用戶中配置每個新 AD FS Microsoft Entra 多重因子驗證證書。
注意
若要完成這道步驟,您需要使用
Connect-MgGraph將您的 Microsoft Entra ID 執行個體與 Microsoft Graph PowerShell 連接。 這些步驟假設您已透過 PowerShell 連線。Connect-MgGraph -Scopes 'Application.ReadWrite.All' $servicePrincipalId = (Get-MgServicePrincipal -Filter "appid eq '981f26a1-7f43-403b-a875-f8b09b8cd720'").Id $keyCredentials = (Get-MgServicePrincipal -Filter "appid eq '981f26a1-7f43-403b-a875-f8b09b8cd720'").KeyCredentials $certX509 = [System.Security.Cryptography.X509Certificates.X509Certificate2]([System.Convert]::FromBase64String($newcert)) $newKey = @(@{ CustomKeyIdentifier = $null DisplayName = $certX509.Subject EndDateTime = $null Key = $certX509.GetRawCertData() KeyId = [guid]::NewGuid() StartDateTime = $null Type = "AsymmetricX509Cert" Usage = "Verify" AdditionalProperties = $null }) $keyCredentials += $newKey Update-MgServicePrincipal -ServicePrincipalId $servicePrincipalId -KeyCredentials $keyCredentials如果先前的憑證已過期,請重新啟動 AD FS 服務,以挑選新的憑證。 如果您在憑證到期前更新憑證,就不需要重新啟動 AD FS 服務。
核驗新證書是否用於 Microsoft Entra 多重因子驗證。
新證書生效後,AD FS 將在幾小時到一天內領取它們並使用個別證書進行 Microsoft Entra 多重因子驗證。 AD FS 使用新憑證之後,您會在每個伺服器上的 AD FS Admin 事件記錄檔中看到事件記錄,其中包含下列資訊:
Log Name: AD FS/Admin
Source: AD FS
Date: 2/27/2018 7:33:31 PM
Event ID: 547
Task Category: None
Level: Information
Keywords: AD FS
User: DOMAIN\adfssvc
Computer: ADFS.domain.contoso.com
Description:
The tenant certificate for Azure MFA has been renewed.
TenantId: contoso.onmicrosoft.com.
Old thumbprint: 7CC103D60967318A11D8C51C289EF85214D9FC63.
Old expiration date: 9/15/2019 9:43:17 PM.
New thumbprint: 8110D7415744C9D4D5A4A6309499F7B48B5F3CCF.
New expiration date: 2/27/2020 2:16:07 AM.
自訂 AD FS 網頁,以引導使用者註冊 MFA 驗證方法
使用下列範例,為尚未證明 (設定 MFA 驗證資訊) 的使用者自訂 AD FS 網頁。
尋找錯誤
首先,當使用者缺少驗證資訊時,AD FS 會傳回幾個不同的錯誤訊息。 如果您將 Microsoft Entra 多重因子驗證當作主要驗證方法使用,未經校對的使用者會看見包含以下訊息的 AD FS 錯誤頁面:
<div id="errorArea">
<div id="openingMessage" class="groupMargin bigText">
An error occurred
</div>
<div id="errorMessage" class="groupMargin">
Authentication attempt failed. Select a different sign in option or close the web browser and sign in again. Contact your administrator for more information.
</div>
當企圖將 Microsoft Entra ID 當作額外驗證方法時,未經校對的使用者會看見包含以下訊息的 AD FS 錯誤頁面:
<div id='mfaGreetingDescription' class='groupMargin'>For security reasons, we require additional information to verify your account (mahesh@jenfield.net)</div>
<div id="errorArea">
<div id="openingMessage" class="groupMargin bigText">
An error occurred
</div>
<div id="errorMessage" class="groupMargin">
The selected authentication method is not available for 'username@contoso.com'. Choose another authentication method or contact your system administrator for details.
</div>
擷取錯誤並更新頁面文字
若要擷取錯誤並顯示使用者自訂指引,請將 JavaScript 附加至 AD FS Web 佈景主題的 onload.js 檔案結尾。 這麼做可以:
- 搜尋識別的錯誤字串。
- 提供自訂的 Web 內容。
注意
如需如何自訂 onload.js 檔案的一般指引,請參閱 AD FS 登入頁面的進階自訂。
下列步驟顯示簡單的範例:
在主要 AD FS 伺服器上開啟 Windows PowerShell,然後執行下列命令來建立新的 AD FS Web 佈景主題。
New-AdfsWebTheme –Name ProofUp –SourceName default建立資料夾,並匯出預設的 AD FS Web 佈景主題。
New-Item -Path 'C:\Theme' -ItemType Directory;Export-AdfsWebTheme –Name default –DirectoryPath C:\Theme在文字編輯器中開啟 C:\Theme\script\onload.js 檔案。
將下列程式碼附加到 onload.js 檔案的尾端:
//Custom Code //Customize MFA exception //Begin var domain_hint = "<YOUR_DOMAIN_NAME_HERE>"; var mfaSecondFactorErr = "The selected authentication method is not available for"; var mfaProofupMessage = "You will be automatically redirected in 5 seconds to set up your account for additional security verification. After you've completed the setup, please return to the application you are attempting to access.<br><br>If you are not redirected automatically, please click <a href='{0}'>here</a>." var authArea = document.getElementById("authArea"); if (authArea) { var errorMessage = document.getElementById("errorMessage"); if (errorMessage) { if (errorMessage.innerHTML.indexOf(mfaSecondFactorErr) >= 0) { //Hide the error message var openingMessage = document.getElementById("openingMessage"); if (openingMessage) { openingMessage.style.display = 'none' } var errorDetailsLink = document.getElementById("errorDetailsLink"); if (errorDetailsLink) { errorDetailsLink.style.display = 'none' } //Provide a message and redirect to Azure AD MFA Registration Url var mfaRegisterUrl = "https://account.activedirectory.windowsazure.com/proofup.aspx?proofup=1&whr=" + domain_hint; errorMessage.innerHTML = "<br>" + mfaProofupMessage.replace("{0}", mfaRegisterUrl); window.setTimeout(function () { window.location.href = mfaRegisterUrl; }, 5000); } } } //End Customize MFA Exception //End Custom Code重要
您需要變更「<YOUR_DOMAIN_NAME_HERE>」;使用您的網域名稱。 例如:
var domain_hint = "contoso.com";。儲存 onload.js 檔案。
輸入下列 Windows PowerShell 命令,將 onload.js 檔案匯入您的自訂佈景主題:
Set-AdfsWebTheme -TargetName ProofUp -AdditionalFileResource @{Uri='/adfs/portal/script/onload.js';path="c:\theme\script\onload.js"}輸入下列 Windows PowerShell 命令,以套用自訂的 AD FS Web 佈景主題:
Set-AdfsWebConfig -ActiveThemeName "ProofUp"