使用適合拆分式 DNS 部署的 DNS 原則
適用於:Windows Server 2022、Windows Server 2019、Windows Server 2016
您可以使用本主題來瞭解如何在 Windows Server® 2016 中設定 DNS 原則以進行拆分式 DNS 部署,單一區域有兩個版本:一個供組織內部網路上的內部使用者使用,另一個則供外部使用者 (通常是網際網路上的使用者) 使用。
注意
如需如何使用 DNS 原則在 Active Directory 整合式 DNS 區域進行拆分式 DNS 部署的詳細資訊,請參閱使用 DNS 原則在 Active Directory 中進行拆分式 DNS。
先前,此案例要求 DNS 系統管理員維護兩部不同的 DNS 伺服器,每部伺服器都會個別為每組使用者 (內部和外部使用者) 提供服務。 如果區域內只有少數記錄是拆分式,或者兩個區域執行個體 (內部和外部) 都委派給同一個父系網域,這將成為一個管理難題。
拆分式部署的另一個組態案例是適用於 DNS 名稱解析的選擇性遞迴控制。 在某些情況下,企業 DNS 伺服器應透過網際網路為內部使用者執行遞迴解析,同時這些伺服器也必須作為外部使用者的授權名稱伺服器,並阻止他們進行遞迴。
本主題包含下列各節。
DNS 拆分式部署範例
以下範例說明如何使用 DNS 原則來完成先前描述的拆分式 DNS 案例。
此章節包含下列主題。
此範例使用一家虛構公司 Contoso,該公司維護以下職涯網站:www.career.contoso.com。
該網站有兩個版本,一個供內部使用者使用,可發佈內部職位資訊。 此內部網站位於本機 IP 位址 10.0.0.39。
第二個版本是同一個網站的公用版本,位於公用 IP 位址 65.55.39.10。
在沒有 DNS 原則的情況下,系統管理員必須將這兩個區域裝載在個別的 Windows Server DNS 伺服器上,並單獨進行管理。
使用 DNS 原則,這些區域現在就可以裝載在同一部 DNS 伺服器上。
下圖描述此案例。
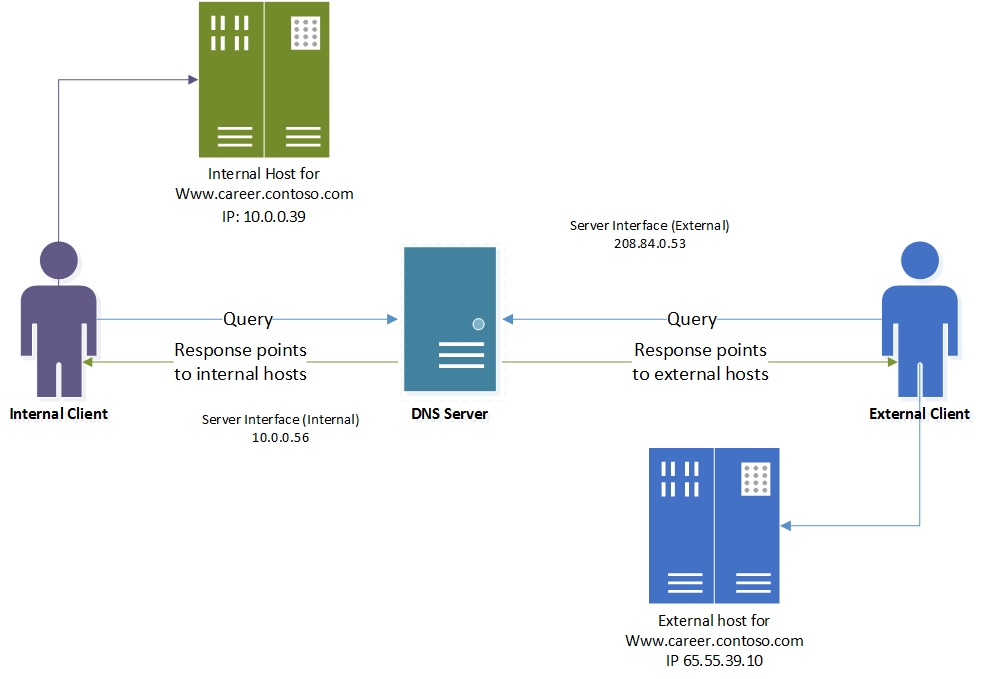
DNS 拆分式部署的運作方式
在 DNS 伺服器設定必要的 DNS 原則後,就會根據 DNS 伺服器上的原則來評估每個名稱解析要求。
此範例使用伺服器介面作為準則,以區分內部和外部用戶端。
如果收到查詢的伺服器介面符合任何原則,則會使用關聯的區域範圍來回應查詢。
因此,在我們的範例中,私人 IP (10.0.0.56) 上收到的 www.career.contoso.com 的 DNS 查詢會收到包含內部 IP 位址的 DNS 回應;而在公用網路介面上收到的 DNS 查詢則會收到在預設區域範圍中包含公用 IP 位址的 DNS 回應 (這與一般查詢解析相同)。
如何設定 DNS 拆分式部署
若要使用 DNS 原則來設定 DNS 拆分式部署,您必須採用下列步驟。
下列各節提供詳細的組態指示。
重要
以下幾節提供範例 Windows PowerShell 命令,其中包含許多參數的範例值。 在執行這些命令之前,請務必先將這些命令中的範例值取代為您的部署所需的值。
建立區域範圍
區域範圍是區域的唯一執行個體。 一個 DNS 區域可以有多個區域範圍,而且每個區域範圍都會包含其本身的 DNS 記錄集。 相同的 DNS 記錄可以出現在多個區域範圍中,這些記錄可具有不同的 IP 位址,也可具有相同的 IP 位址。
注意
根據預設,DNS 區域上會有區域範圍。 這個預設區域範圍的名稱與該區域的名稱相同,而且舊的 DNS 作業都在這個範圍上進行。 這個預設區域範圍將裝載 www.career.contoso.com 的外部版本。
您可以使用下列範例命令來分割區域範圍 contoso.com,從而建立內部區域範圍。 內部區域範圍將用來保留 www.career.contoso.com 的內部版本。
Add-DnsServerZoneScope -ZoneName "contoso.com" -Name "internal"
如需詳細資訊,請參閱 Add-DnsServerZoneScope
將記錄新增到區域範圍
下一步會將代表 Web 伺服器主機的記錄新增到兩個區域範圍:內部和預設 (適用於外部用戶端)。
在內部區域範圍中,記錄 www.career.contoso.com 新增了 IP 位址 10.0.0.39,這是一個私人 IP;而在預設區域範圍的相同記錄 www.career.contoso.com 中則新增了 IP 位址 65.55.39.10。
將記錄新增到預設區域範圍後,下列範例命令中不提供 –ZoneScope 參數。 這類似於將記錄新增到普通區域。
Add-DnsServerResourceRecord -ZoneName "contoso.com" -A -Name "www.career" -IPv4Address "65.55.39.10"
Add-DnsServerResourceRecord -ZoneName "contoso.com" -A -Name "www.career" -IPv4Address "10.0.0.39” -ZoneScope "internal"
如需詳細資訊,請參閱 Add-DnsServerResourceRecord。
建立 DNS 原則
識別出外部網路和內部網路的伺服器介面並建立區域範圍後,您必須建立連接內部和外部區域範圍的 DNS 原則。
注意
此範例使用伺服器介面作為準則,以區分內部和外部用戶端。 另一個區分外部和內部用戶端的方法,是使用用戶端子網路作為準則。 如果您可以識別內部用戶端所屬的子網路,則可以設定 DNS 原則,以根據用戶端子網路進行區分。 如需如何使用用戶端子網路準則設定流量管理的相關資訊,請參閱使用 DNS 原則對主要伺服器進行地理位置流量管理。
DNS 伺服器在專用介面上收到查詢時,將從內部區域範圍傳回 DNS 查詢回應。
注意
對應預設區域範圍不需要任何原則。
在下列範例命令中,10.0.0.56 是私人網路介面上的 IP 位址,如下圖所示。
Add-DnsServerQueryResolutionPolicy -Name "SplitBrainZonePolicy" -Action ALLOW -ServerInterface "eq,10.0.0.56" -ZoneScope "internal,1" -ZoneName contoso.com
如需詳細資訊,請參閱 Add-DnsServerQueryResolutionPolicy。
DNS 選擇性遞迴控制範例
以下範例說明如何使用 DNS 原則來完成先前描述的 DNS 選擇性遞迴控制案例。
此章節包含下列主題。
此範例使用與先前範例相同的虛構公司 Contoso,該公司維護以下職涯網站:www.career.contoso.com。
在 DNS 拆分式部署範例中,同一部 DNS 伺服器會同時回應外部和內部用戶端,並提供不同的答案。
部分 DNS 部署除了作為外部用戶端的授權名稱伺服器之外,可能還需要同一部 DNS 伺服器才能為內部用戶端執行遞迴名稱解析。 這種情況稱為 DNS 選擇性遞迴控制。
在舊版 Windows Server 中,啟用遞迴表示在整個 DNS 伺服器上對所有區域啟用遞迴。 由於 DNS 伺服器也會接聽外部查詢,因此會同時對內部和外部用戶端啟用遞迴,使 DNS 伺服器成為一個開放式解析程式。
設定為開放式解析程式的 DNS 伺服器會很容易耗盡資源,而且可能會遭到惡意用戶端濫用而建立反射攻擊。
因此,Contoso DNS 系統管理員不希望 contoso.com 的 DNS 伺服器對外部用戶端執行遞迴名稱解析。 僅內部用戶端需要遞迴控制,外部用戶端則可以阻止遞迴控制。
下圖描述此案例。

DNS 選擇性遞迴控制的運作方式
如果收到的查詢指出 Contoso DNS 伺服器是未經授權的伺服器,例如 https://www.microsoft.com,則會根據 DNS 伺服器上的原則來評估名稱解析要求。
由於這些查詢不屬於任何區域,因此不會評估區域層級原則 (如拆分式範例中所定義)。
DNS 伺服器會評估遞迴原則,且在私人介面上收到的查詢符合 SplitBrainRecursionPolicy。 此原則指向啟用遞迴的遞迴範圍。
DNS 伺服器接著會執行遞迴,以從網際網路取得 https://www.microsoft.com 的答案,並在本機快取回應。
如果是在外部介面上收到查詢,則沒有任何符合的 DNS 原則,且會套用預設遞迴設定:在本例中為 [已停用]。
這可以防止伺服器作為外部用戶端的開放式解析程式,同時作為內部用戶端的快取解析程式。
如何設定 DNS 選擇性遞迴控制
若要使用 DNS 原則來設定 DNS 選擇性遞迴控制,您必須採用下列步驟。
建立 DNS 遞迴範圍
遞迴範圍是一組設定的唯一執行個體,用於控制 DNS 伺服器上的遞迴。 遞迴範圍包含轉寄站清單,並指定是否啟用遞迴。 DNS 伺服器可以有多個遞迴範圍。
舊的遞迴設定和轉寄站清單稱為預設遞迴範圍。 您無法新增或移除由名稱點 (“.”) 所確定的預設遞迴範圍。
在此範例中,預設遞迴設定被停用,同時會在啟用遞迴的內部用戶端建立新的遞迴範圍。
Set-DnsServerRecursionScope -Name . -EnableRecursion $False
Add-DnsServerRecursionScope -Name "InternalClients" -EnableRecursion $True
如需詳細資訊,請參閱 Add-DnsServerRecursionScope
建立 DNS 遞迴原則
您可以建立 DNS 伺服器遞迴原則,為符合特定準則的一組查詢選擇一個遞迴範圍。
如果 DNS 伺服器不是某些查詢的授權伺服器,則 DNS 伺服器遞迴原則可供您控制解析這些查詢的方式。
在此範例中,啟用遞迴的內部遞迴範圍與私人網路絡介面相關聯。
您可以使用下列範例命令來設定 DNS 遞迴原則。
Add-DnsServerQueryResolutionPolicy -Name "SplitBrainRecursionPolicy" -Action ALLOW -ApplyOnRecursion -RecursionScope "InternalClients" -ServerInterfaceIP "EQ,10.0.0.39"
如需詳細資訊,請參閱 Add-DnsServerQueryResolutionPolicy。
現在,DNS 伺服器會針對拆分式名稱伺服器或針對為內部用戶端啟用選擇性遞迴控制的 DNS 伺服器,設定必要的 DNS 原則。
您可以根據流量管理需求建立幾千個 DNS 原則,且所有新原則都會動態套用至傳入的查詢,而無需重新啟動 DNS 伺服器。
如需詳細資訊,請參閱 DNS 原則案例指南。