Integrate Defender for Cloud Apps with Microsoft Defender for Identity
Microsoft Defender for Identity integrates with your on-premises Active Directory Domain Services (AD DS) environment. This integration can help you detect, investigate, and identify advanced threats, compromised identities, and other malicious actions targeted at your organization.
By using Defender for Identity, you can:
- Monitor activities, users, and entity behavior
- Help protect AD DS identities and credentials
- Identify and investigate suspicious user activities and advanced attacks
- Provide clear incident information to help triage security threats
Enable integration
You can integrate Defender for Identity with Microsoft Defender for Cloud Apps. By doing so, you can use the Defender for Cloud Apps portal to access alerts and insights from:
- Defender for Cloud Apps, which monitors cloud apps
- Defender for Identity, which identifies attacks in your on-premises network environment
- Microsoft Entra ID Protection, which helps detect and prevent user and sign-in risks for cloud-based identities
Note
To access user investigation features across your hybrid environment, you'll need a license for both Microsoft Defender for Cloud Apps and Microsoft Defender for Identity.
To enable integration, use the following procedure:
From within the Defender for Cloud Apps portal, open Settings.
In the Threat Protection section, select Microsoft Defender for Identity.
On the Microsoft Defender for Identity page, select Enable Microsoft Defender for Identity data integration.
Note
In can take up to 12 hours for Defender for Cloud Apps to complete its initial setup and integration.
Investigate Defender for Identity activities
After you have enabled integration, you can use the Defender for Cloud Apps portal to investigate Defender for Identity activities. In the portal, select the Alerts in the navigation pane. You can then filter for specific users, devices, or actions. In the following example, the administrator has filtered the alerts for a specific USER NAME.
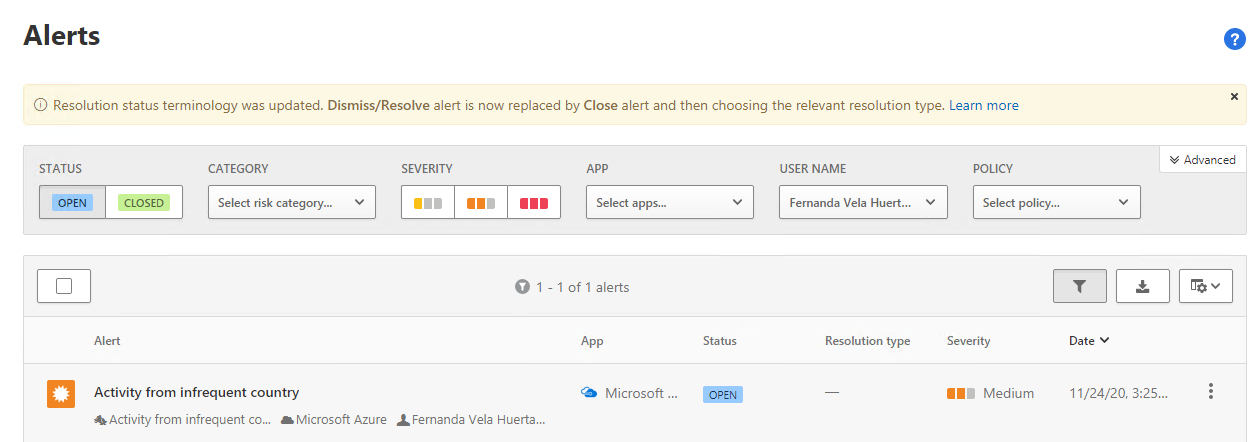
If you need more information, you can select Advanced and build a more detailed query. You can also create activity policies in Defender for Cloud Apps to take action against suspected threats. As with other policies, you can create a policy from within a query in the Activity log, or else use the Policies node in the navigation pane.

For example, to save a query as an activity policy, use the following procedure:
- From any Activity log page, apply a filter such as App, User Name, or Activity type. For example, to filter activities from Defender for Identity, select Active Directory in the App filter.
- Select New policy from search.
- Enter a Policy name and a policy Description.
- Assign the Severity of the policy.
- Select a Category for the policy.
- Choose or modify filters to create and assign for the policy.
- Refine or add more filters.
- Save and apply the new policy.