I have found a simple working solution that does not involve manually editing Windows Registry keys and other boring actions. The only thing you need is to use the built-in cmdkey tool and problem solved.
Solution (TL;DR)
Here is the only step you need to perform at Windows Command Prompt:
cmdkey /generic:TERMSRV/<targetname> /user:<username> /pass:<password>
That's it.
After that you can connect to your target machine using Windows Remote Desktop client and no password will be asked. I now again enjoy the comfort of immediate Remote Desktop connections without annoying credential prompts 😃.
Example
You want to connect to a machine at IP address 10.10.10.10 with the username Donald and the password qwerty. So add the following generic TERMSRV credentials:
cmdkey /generic:TERMSRV/10.10.10.10 /user:Donald /pass:qwerty
~
Additional info
It is important to add specifically GENERIC credentials. I have noticed that after using the related checkbox in Remote Desktop Connection tool ("Allow me to save credentials"), it actually works and saves the provided credentials, BUT it saves them with the type "Domain Password" and this does not work (you will see "Windows Defender Credential Guard does not allow using saved credentials" etc).
You can check the type of your saved TERMSRV credentials it by executing the following command (using asterisk * to list everything):
cmdkey /list:TERMSRV/*
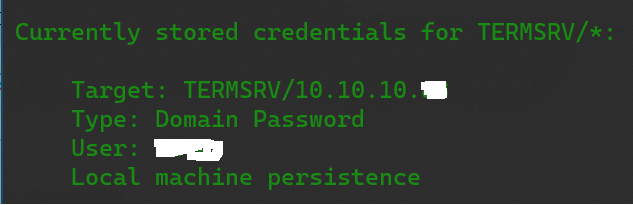
But when you add a GENERIC credentials - it works and Windows Defender has no objections about that ))
And now, after adding the generic credentials, when you execute cmdkey /list:TERMSRV/* command you will see this:
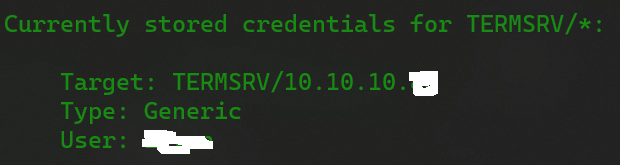
Notice how the Type is now Generic.
BTW if you wish you can delete the previously added credentials, e.g.:
cmdkey /delete:TERMSRV/10.10.10.10
~
Technical documentation
- The official Microsoft documentation for
cmdkey tool: cmdkey
- Microsoft Win32 API documentation for
wincred.h C header file, where you can see different types of credentials: CREDENTIALA structure (wincred.h)

