Tips and Tools for Deploying Windows 7 Part 1–Planning and Pre-Deployment Remediation
Like everyone else, you love Windows 7 and can’t wait to get it deployed throughout your organization. Let’s take a look at the many tips and tools available today to ease your burden of deployment. I have broken it down into several steps (or categories of steps). While writing all of this, it became obvious really fast that there is way too much stuff for a single post so I have broken it down into 5 parts. They are: 
If you like this post, please contact me on Twitter @ITProGuru to let me know. To keep from missing other posts, make sure you add an RSS to my blog.
Before I get too deep into these topics, I want to let you know about an eBook available for download. It is Deploying Windows 7 – Essential Guidance from the Windows 7 Resource Kit and TechNet Magazine. It is 412 pages of very detailed content for those that really want to learn as much as they can about all aspects of Deployment.
Part 1: Planning and Pre-Deployment Remediation
First let’s take a look at planning. If you only have a few workstations, maybe you feel not much planning is needed. However, if that were the case, you would have likely already completed your deployment. The first thing we need to understand is what do we have in/on our network now? The best way to figure this out is to do a network assessment. You can download the Microsoft Assessment and Planning Toolkit or MAP which is a “Solution Accelerator” from Microsoft. The Microsoft Assessment and Planning (MAP) Toolkit is an agentless tool designed to simplify and streamline the IT infrastructure planning process across multiple scenarios through network-wide automated discovery and assessments. MAP performs an inventory of heterogeneous IT environments and provides you with usage information. The discovery and assessment can be used for consolidation, and/or a readiness assessment for the most widely used Microsoft technologies including Windows 7, Office 2010, and Windows Server 2008 R2 as well as other applications such as SQL Server and Exchange Server. MAP also provides server virtualization scenarios to help you identify underutilized resources and the hardware specifications needed to successfully consolidate your servers using Microsoft Hyper-V technology. Just download the MAP (5.5) and install it. It uses SQL Express to store the data it collects. During the installation of MAP it will automatically download and install SQL Express for you if you like. The first thing you will need to do is setup your environment to allow a “discovery” and inventory. Discovery will scan for computers that can be analyzed by MAP. You can discover in many different ways including: Active Directory (AD DS), Windows Networking protocols, System Center Configuration Manager (more on this later), Import computer names from a file (list of up to 120,000 computer names), Scan an IP range or manually enter computer names. Once the computers are discovered, an inventory will be needed. For each computer in a network that is to be included in the inventory and assessment process, you must specify an account that is a member of the local Administrators group on that computer. To inventory domain controllers in your network, you need to specify domain administrator credentials. The inventory methods used include: Windows Management Instrumentation (WMI), Remote Registry Service, VMware Webservice and Secure Shell (SSH) which gives you full capabilities to inventory not only Microsoft systems but also VMWare servers and Linux/Unix operating systems.
Revision: 1/20/2011 – The MAP 5.5 is available so the reference link above was changed from the beta site to the release site.
In order for the MAP computer to see what is on your network, you should make sure that firewalls allow the communication and that remote administration is enabled.
The Remote Registry service is used to find the roles installed on a server. It is also required for running the Performance Metrics Wizard. This service is installed on Windows-based clients and servers, but the following conditions must exist for this inventory method to be successful:
· The Remote Registry service must be started. By default, it is configured to start automatically.
· The Windows Firewall Remote Administration exception must be enabled.
· You must authenticate using local Administrator equivalent privileges.
If the Remote Registry service is disabled on a server, you need to enable it before performing the inventory. You can either manually enable the service or configure it to start via Group Policy and wait until the servers are rebooted (and the service starts) before starting the Windows Server® 2008 Hardware Assessment or Performance Metrics Wizard.
To manually enable the Remote Registry service
1. On the computer on which you want to access Reliability Monitor data, click Start, right-click Computer, and then click Manage.
Microsoft Management Console (MMC) starts.
2. In the navigation pane, expand Services and Applications, and then click Services.
3. In the console pane, right-click Remote Registry, and then click Start. 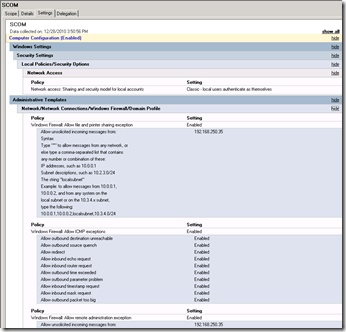
You can setup the environment for the Windows machines by simply creating a group policy and linking it.
To enable Windows Firewall exceptions using Group Policy
1. Using the Local Group Policy Editor, click Computer Configuration, click Windows Settings, click Security Settings, click Local Policies, and then click Security Options.
2. In the Network access: Sharing and security model for local accounts section, click Classic – local users authenticate as themselves.
3. Using the Local Group Policy Editor, click Computer Configuration, click Administrative Templates, click Network, click Network Connections, click Windows Firewall, and then click Domain Profile.
4. In the Windows Firewall: Allow remote administration exception section, click Enabled.
5. In the Allow unsolicited incoming messages from text box, type the IP address or subnet of the computer that will be performing the inventory.
6. In the Windows Firewall: Allow file and print sharing exception section, click Enabled.
7. In the Allow unsolicited incoming messages from text box, type the IP address or subnet of the computer performing the inventory.
After saving the policy changes, you will need to wait for up to two hours for the Group Policy settings to be applied to the client computers. In the screen shot above you can see the what the Group Policy Manager report would look like on these changes. Note I added the ICMP exceptions in mine but that is not required. It may be helpful for troubleshooting.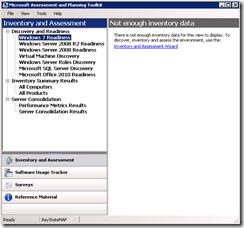
We now have our environment setup and the MAP is installed so go ahead and launch the program from the “Microsoft Assessment and Planning Toolkit” icon under All Programs. You will be prompted to create an inventory database. Just give it a name and click OK. On the left pane expand Discovery and Readiness and click “Windows 7 Readiness”. On the right pane, you can now click “Inventory and assessment Wizard”. Go ahead and step through the simple wizard filling in the blanks. If you are not sure what to put in, just leave the defaults. You will need to put in the credentials to get a complete assessment. Depending on how many machines you are doing it could take some time for the discovery to complete. The first time you run it, you might want to limit the discovery to one or two machines so it goes pretty quickly. Once the discovery and inventory is done you can check out the software Usage Tracker, look at the data for current versions of software, patches, etc running on the box and even generate an executive report to tweak if you like and give to the boss to show what exactly is needed for you to get to create an environment that has fully deployed Windows 7 and even Office 2010.
If you like this post, please contact me on Twitter @ITProGuru to let me know. To keep from missing other posts, make sure you add an RSS to my blog.