Restrict organization creation via Microsoft Entra tenant policy
Azure DevOps Services
Learn how to turn on the Microsoft Entra tenant policy, which restricts users from creating an organization in Azure DevOps. This policy is turned off, by default.
Prerequisites
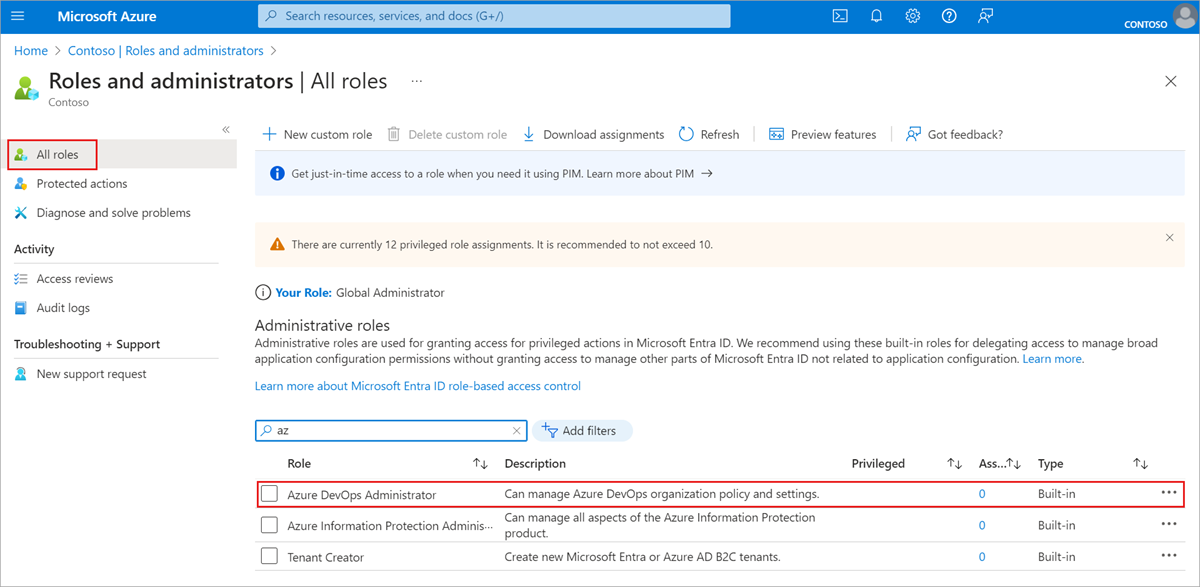
You must be an Azure DevOps Administrator in Microsoft Entra ID to manage this policy. It isn't a requirement to be a Project Collection Administrator.
If you don't see the policy section in Azure DevOps, then you aren't an administrator. To check your role, sign in to the Azure portal, and then choose Microsoft Entra ID > Roles and administrators. In case that you aren't an Azure DevOps administrator, talk to your administrator.
Turn on the policy
Sign in to your organization (
https://dev.azure.com/{yourorganization}).Select
 Organization settings.
Organization settings.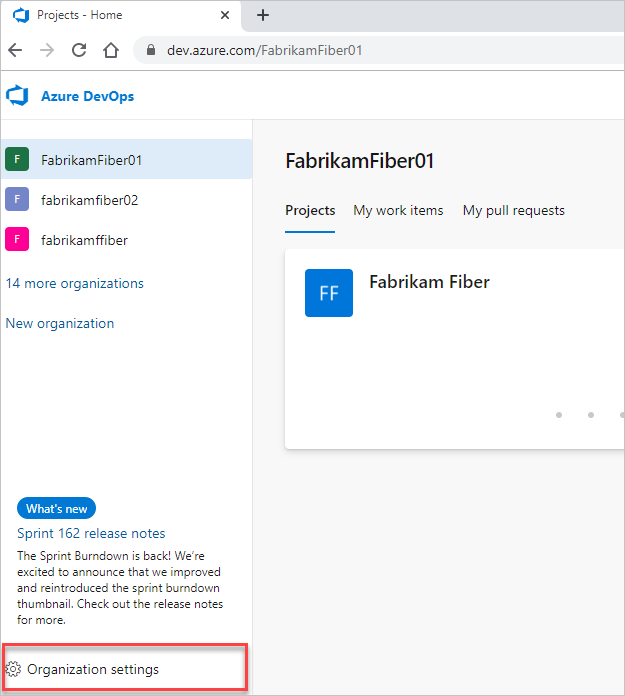
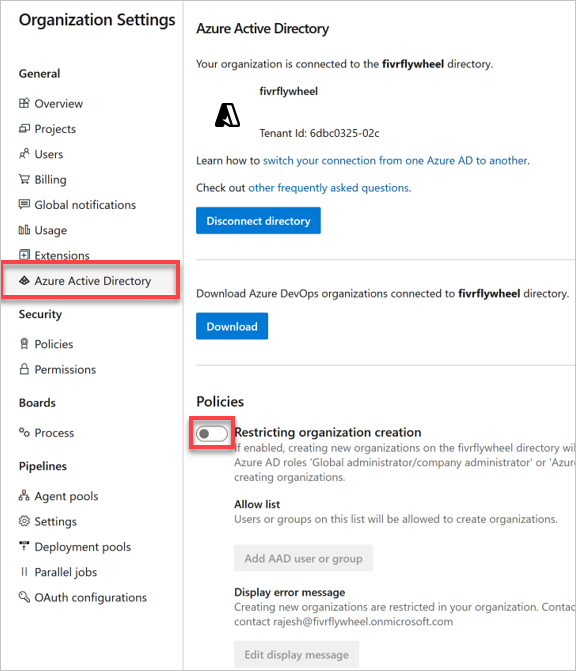
Select Microsoft Entra ID, and then switch the toggle to turn on the policy, restricting organization creation.
Optional
Create allowlist
Warning
We recommend using groups with your tenant policy allow list(s). If you use a named user, be aware that a reference to the named user's identity will reside in the United States, Europe (EU), and Southeast Asia (Singapore).
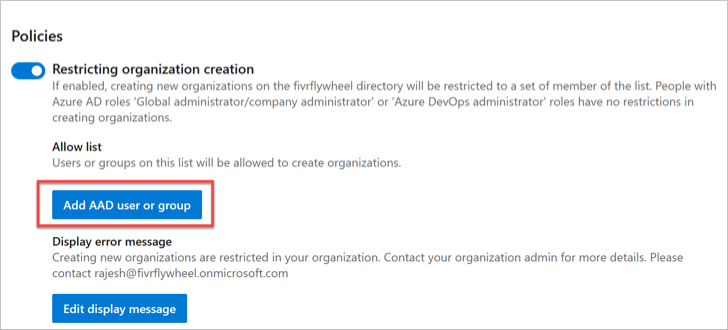
With the policy turned on, all users are restricted from creating new organizations. Grant an exception to users with an allowlist. Users on the allowlist can create new organizations, but they can't manage the policy.
- Select Add Microsoft Entra user or group.
Create error message
When administrators, who aren't on the allowlist, try to create an organization they get an error similar to the following example.
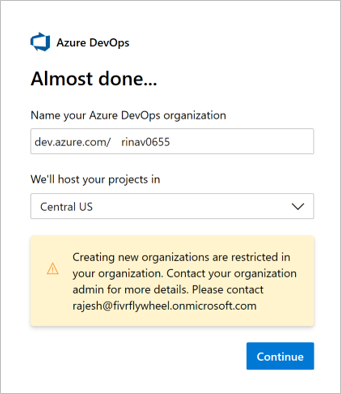
Customize this error message in the policy settings in Azure DevOps.
Select Edit display message.
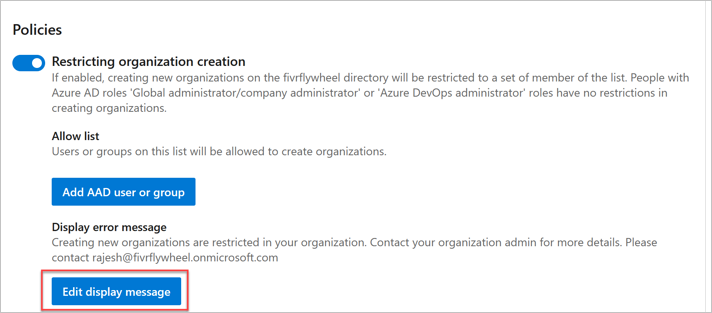
Enter your customized message, and then choose Save.

The error message is customized.
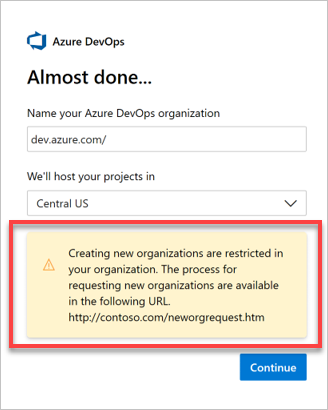
Note
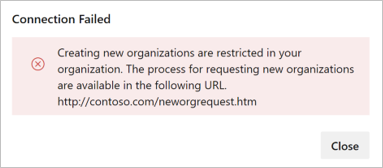
Administrators, who aren't on the allow list, can't connect their organization to the Microsoft Entra tenant where the policy is turned on.
Related articles
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for