Connect your organization to Microsoft Entra ID
Azure DevOps Services
Learn how to connect your Azure DevOps organization to Microsoft Entra ID. You can sign in with the same username and password that you use with Microsoft services. Add members to your Azure DevOps organization who are already a part of your work organization. You can also enforce policies for accessing your team's critical resources and key assets.
For more information about using Microsoft Entra ID with Azure DevOps, see the conceptual overview.
Prerequisites
Have 100 or fewer users in your organization. If your organization has more than 100 users, contact Support for help with connecting to Microsoft Entra ID.
You must be a member of the Project Collection Administrators group or the organization Owner to make the connection.
Ensure that you exist in Microsoft Entra ID as a member. For more information, see how you can convert a Microsoft Entra ID guest into a member.
Inform users of the upcoming change. There's no downtime during this change, but users are affected. Let them know before you begin that there's a short series of steps they need to complete. As your company transitions from Microsoft account (MSA) to Microsoft Entra identities, your users' benefits continue with their new identity, as long as their emails match.
Delete unwanted users from your organization. For example, you can remove a user who left the company and is no longer an employee.
Prepare your mapping list for inviting users to Microsoft Entra ID.
Sign in to your organization (
https://dev.azure.com/{yourorganization}).Select
 Organization settings.
Organization settings.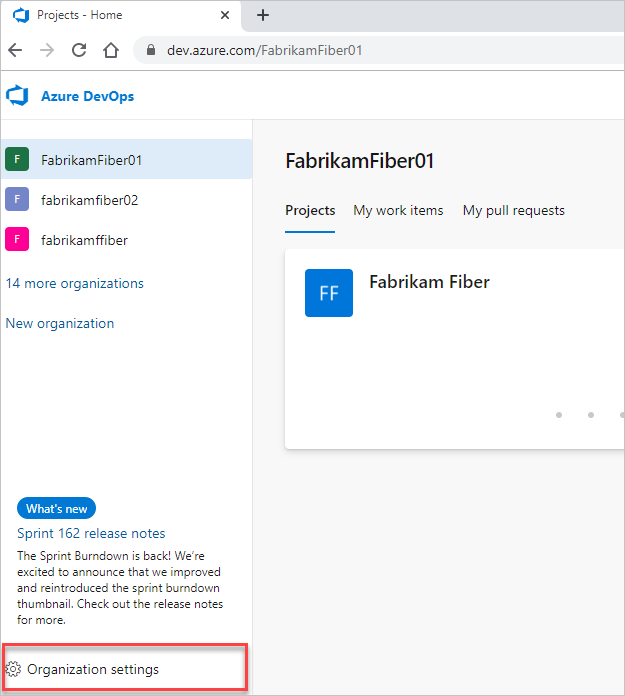
Select Users.

Compare your Azure DevOps email list with your Microsoft Entra ID email list. Create a Microsoft Entra ID email address entry for every user who's in the Azure DevOps organization and not in the Microsoft Entra ID. Afterward, you can invite users as guests who don't have Microsoft Entra ID email addresses.
Note
Ensure you're using Microsoft Entra Public. Connecting Azure DevOps Services organizations to Microsoft Entra Government and accessing Azure DevOps Services with user accounts from Microsoft Entra Government isn't supported.
Connect your organization to Microsoft Entra ID
Sign in to your organization (
https://dev.azure.com/{yourorganization}).Select
 Organization settings.
Organization settings.
Select Microsoft Entra ID, and then select Connect directory.
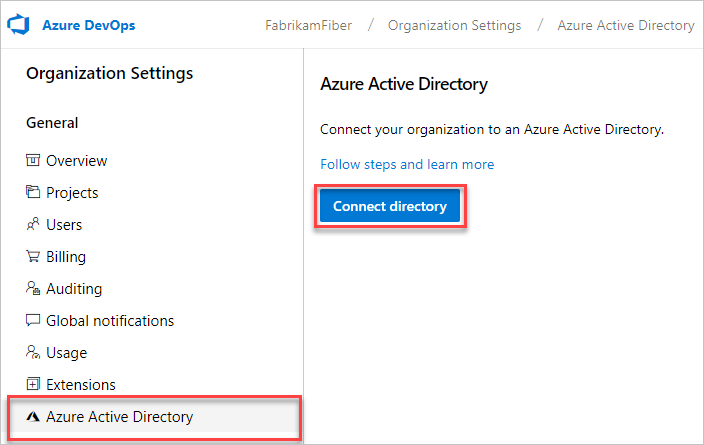
Select a directory from the dropdown menu, and then select Connect.
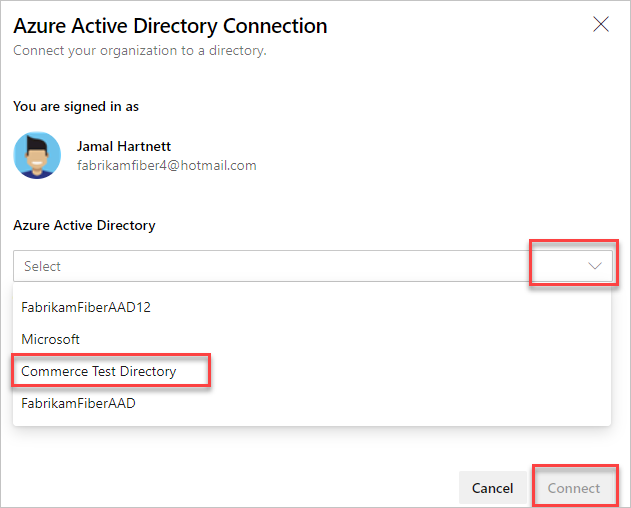
If you can't find your directory, contact your Microsoft Entra administrator and request that they add you as a member to the Microsoft Entra ID.
Select Sign out.
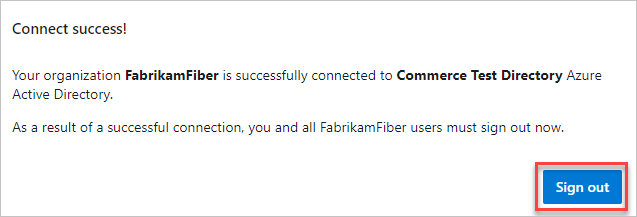
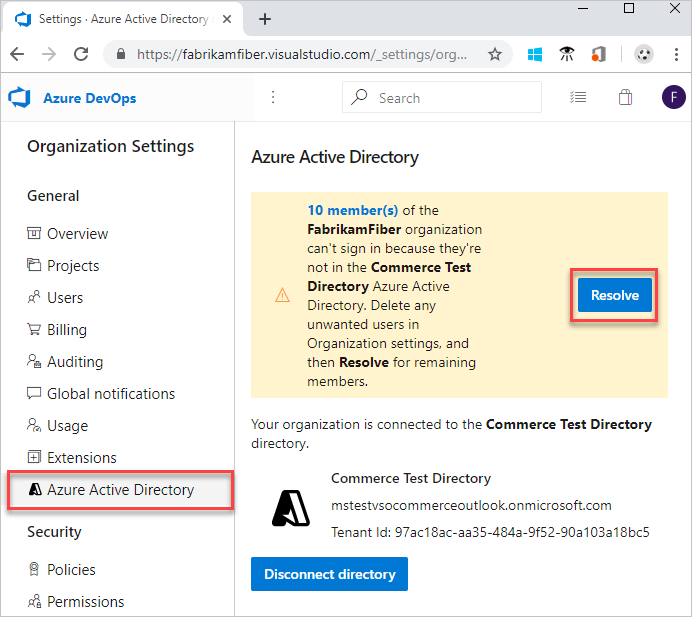
Your organization is now connected to your Microsoft Entra ID.
Confirm that the process is complete. Sign out, and then open your browser in a private session and sign in to your organization with your Microsoft Entra ID or work credentials.
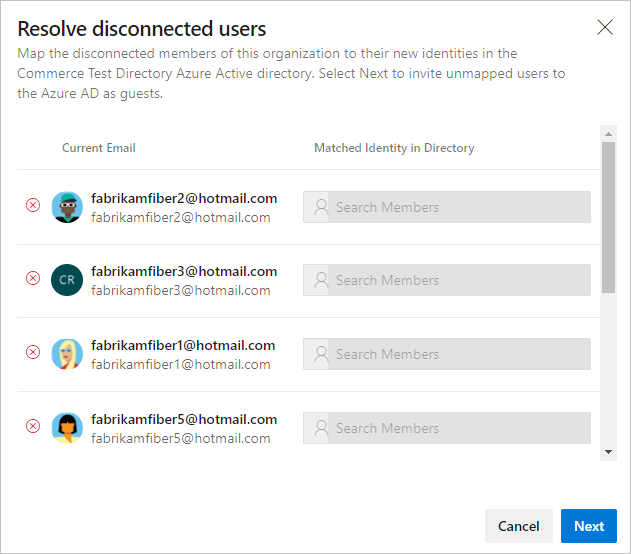
Sign back in to Azure DevOps and map any disconnected members to their Microsoft Entra identities. Or, you can invite them as guests into the Microsoft Entra ID. For more information, see the FAQs.
Inform users of the completed change
When you inform your users of the completed change, include the following tasks for each user in the organization to complete:
Clear the cache for the Git Credential Manager if you use Visual Studio or the Git command-line tool. Delete the %LocalAppData%\GitCredentialManager\tenant.cache file on each client machine.
Regenerate new personal access tokens. Complete the following steps:
a. In Azure DevOps, open your User profile, and then select Security from the resulting dropdown menu.

b. Select Personal access tokens, and then select New Token.

c. Complete the form, and then select Create.
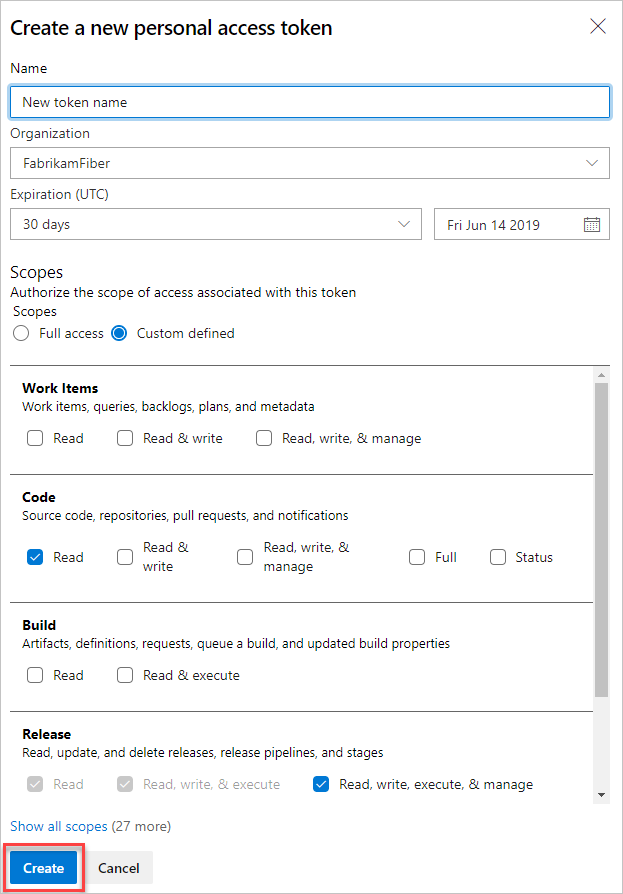
d. When the token is created, copy it, as it can't be viewed again.
Request that SSH keys be manually cleared by Support, and then recreate SSH keys. Complete the following steps.
a. In Azure DevOps, open your User profile, and then select Security from the resulting dropdown menu.

b. Select SSH public keys, and then select Add.
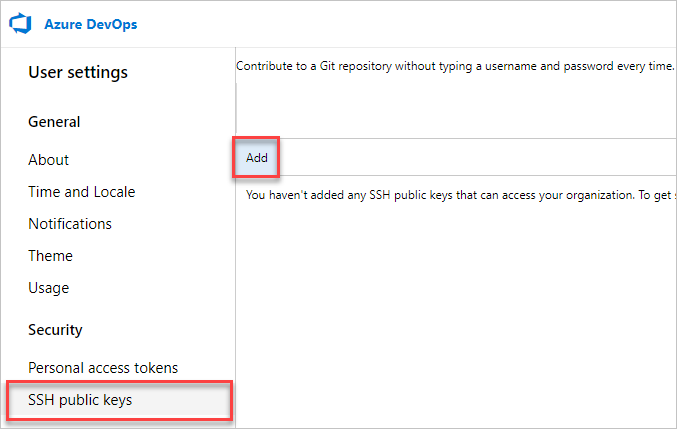
c. Enter a description and key data, and then select Save.
d. When the token's created, copy it, as it can't be viewed again.
Rename your Microsoft account to a different email that doesn't conflict with your Microsoft Entra identity. Doing so ensures that you won't be prompted to choose between accounts.
Adjust your Visual Studio subscription if the UPN used inside your Azure DevOps organization has changed. You can have it reassigned to your new UPN, or set that UPN as the alternate account inside the subscription. For more information, see how to add an alternate account to your subscription.
Related articles
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for