Configure Azure Firewall application rules with SQL FQDNs
You can now configure Azure Firewall application rules with SQL FQDNs. This allows you to limit access from your virtual networks to only the specified SQL server instances.
With SQL FQDNs, you can filter traffic:
- From your VNets to an Azure SQL Database or Azure Synapse Analytics. For example: Only allow access to sql-server1.database.windows.net.
- From on-premises to Azure SQL Managed Instances or SQL IaaS running in your VNets.
- From spoke-to-spoke to Azure SQL Managed Instances or SQL IaaS running in your VNets.
SQL FQDN filtering is supported in proxy-mode only (port 1433). If you use SQL in the default redirect mode, you can filter access using the SQL service tag as part of network rules. If you use non-default ports for SQL IaaS traffic, you can configure those ports in the firewall application rules.
Configure using Azure CLI
Deploy an Azure Firewall using Azure CLI.
If you filter traffic to Azure SQL Database, Azure Synapse Analytics, or SQL Managed Instance, ensure the SQL connectivity mode is set to Proxy. To learn how to switch SQL connectivity mode, see Azure SQL Connectivity Settings.
Note
SQL proxy mode can result in more latency compared to redirect. If you want to continue using redirect mode, which is the default for clients connecting within Azure, you can filter access using the SQL service tag in firewall network rules.
Create a new rule collection with an application rule using SQL FQDN to allow access to a SQL server:
az extension add -n azure-firewall az network firewall application-rule create \ --resource-group Test-FW-RG \ --firewall-name Test-FW01 \ --collection-name sqlRuleCollection \ --priority 1000 \ --action Allow \ --name sqlRule \ --protocols mssql=1433 \ --source-addresses 10.0.0.0/24 \ --target-fqdns sql-serv1.database.windows.net
Configure using Azure PowerShell
Deploy an Azure Firewall using Azure PowerShell.
If you filter traffic to Azure SQL Database, Azure Synapse Analytics, or SQL Managed Instance, ensure the SQL connectivity mode is set to Proxy. To learn how to switch SQL connectivity mode, see Azure SQL Connectivity Settings.
Note
SQL proxy mode can result in more latency compared to redirect. If you want to continue using redirect mode, which is the default for clients connecting within Azure, you can filter access using the SQL service tag in firewall network rules.
Create a new rule collection with an application rule using SQL FQDN to allow access to a SQL server:
$AzFw = Get-AzFirewall -Name "Test-FW01" -ResourceGroupName "Test-FW-RG" $sqlRule = @{ Name = "sqlRule" Protocol = "mssql:1433" TargetFqdn = "sql-serv1.database.windows.net" SourceAddress = "10.0.0.0/24" } $rule = New-AzFirewallApplicationRule @sqlRule $sqlRuleCollection = @{ Name = "sqlRuleCollection" Priority = 1000 Rule = $rule ActionType = "Allow" } $ruleCollection = New-AzFirewallApplicationRuleCollection @sqlRuleCollection $Azfw.ApplicationRuleCollections.Add($ruleCollection) Set-AzFirewall -AzureFirewall $AzFw
Configure using the Azure portal
Deploy an Azure Firewall using Azure CLI.
If you filter traffic to Azure SQL Database, Azure Synapse Analytics, or SQL Managed Instance, ensure the SQL connectivity mode is set to Proxy. To learn how to switch SQL connectivity mode, see Azure SQL Connectivity Settings.
Note
SQL proxy mode can result in more latency compared to redirect. If you want to continue using redirect mode, which is the default for clients connecting within Azure, you can filter access using the SQL service tag in firewall network rules.
Add the application rule with the appropriate protocol, port, and SQL FQDN and then select Save.
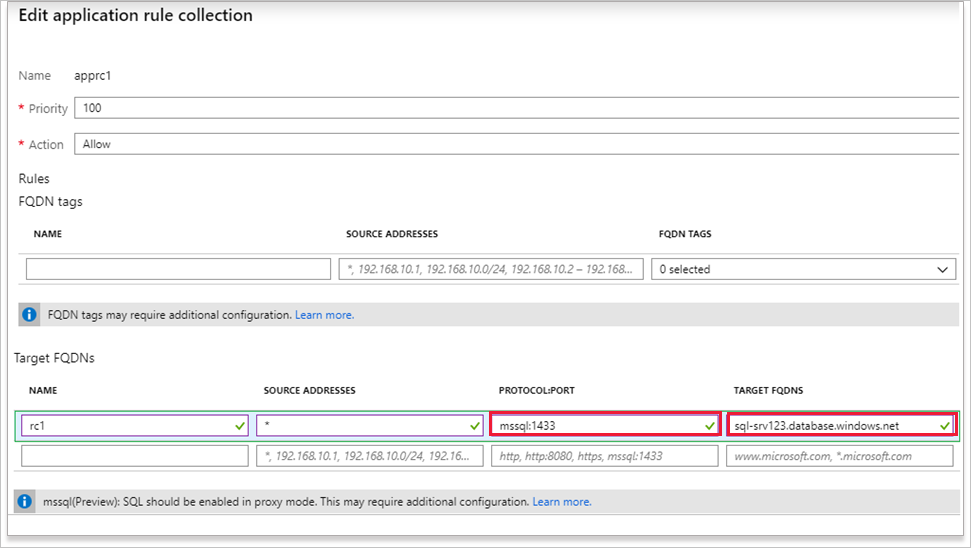
Access SQL from a virtual machine in a VNet that filters the traffic through the firewall.
Validate that Azure Firewall logs show the traffic is allowed.
Next steps
To learn about SQL proxy and redirect modes, see Azure SQL Database connectivity architecture.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for