Regulate deployments in Model Catalog using policies
The Model Catalog in Azure Machine Learning studio provides access to many open-source foundation models, and regulating the deployments of these models by enforcing organization standards can be of paramount importance to meet your security and compliance requirements. In this article, you learn how you can restrict the deployments from the Model Catalog using a built-in Azure Policy.
Azure Policy is a governance tool that gives users the ability to audit, perform real-time enforcement and manage their Azure environment at scale. For more information, see the Overview of the Azure Policy service.
Example Usage Scenarios:
- You want to enforce your organizational security policies, but you don't have an automated and reliable way to do so.
- You want to relax some requirements for your test teams, but you want to maintain tight controls over your production environment. You need a simple automated way to separate enforcement of your resources.
Azure Policy for Azure Machine Learning Registry model deployments
With the Azure Machine Learning built-in policy for registry model deployments(preview), you can deny all registry deployments or allow model deployments from a specific registry. You can also add an optional blocklist of models and add exceptions to the list within the allowed registry.
This built-in policy supports Deny effect only.
Deny: With the effect of the policy set to deny, the policy blocks the creation of new deployments from Azure Machine Learning registries that don't comply with the policy definition and generate an event in the activity log. Existing noncompliant deployments aren't affected.
Model Catalog collections are made available to users using the underlying registries. You can find the underlying registry name in the model asset ID.
Create a Policy Assignment
On the Azure home page, type Policy in the search bar and select the Azure Policy icon.
On the Azure Policy service, under Authoring, select Assignments.
On the Assignments page, select the Assign Policy icon at the top.
On the Assign Policy page basics tab, update the following fields:
- Scope: Select what Azure subscriptions and resource groups the policies apply to.
- Exclusions: Select any resources from the scope to exclude from the policy assignment.
- Policy Definition: Select the policy definition to apply to the scope with exclusions. Type "Azure Machine Learning" in the search bar and locate the policy '[Preview] Azure Machine Learning Model Registry Deployments are restricted except for allowed registry'. Select the policy and select Add.
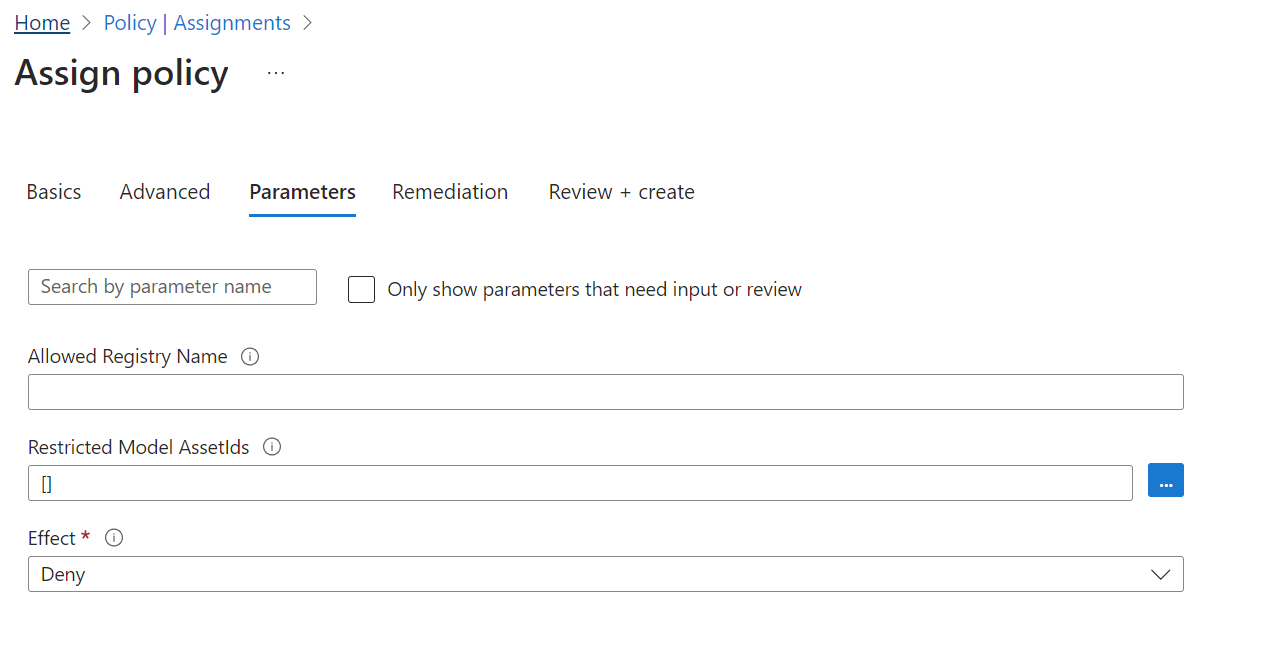
Select the Parameters tab and update the Effect and policy assignment parameters. Make sure to uncheck the 'Only show parameters that need input or review' so all the parameters show up. To further clarify what the parameter does, hover over the info icon next to the parameter name.
If no model asset IDs are set in the Restricted Model AssetIds parameter during the policy assignment, this policy only allows deploying all models from the model registry specified in Allowed Registry Name parameter.
Select Review + Create to finalize your policy assignment. The policy assignment takes approximately 15 minutes until it's active for new resources.
Disable the policy
You can remove the policy assignment in the Azure portal using the following steps:
- Navigate to the Policy pane on the Azure portal.
- Select Assignments.
- Select on the ... button next to your policy assignment and select Delete assignment.
Limitations
- Any change in the policy (including updating the policy definition, assignments, exemptions or policy set) takes 10 mins for those changes to become effective in the evaluation process.
- Compliance is reported for newly created and updated deployments. During public preview, compliance records remain for 24 hours. Model deployments that exist before these policy definitions are assigned won't report compliance. You also can’t trigger the evaluations of deployments that existed before setting up the policy definition and assignment.
- You can’t allowlist more than one registry in a policy assignment.
Next Steps
- Learn how to get compliance data.
- Learn how to create policies programmatically.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for