Configure a point-to-site VPN connection to a VNet using multiple authentication types: Azure portal
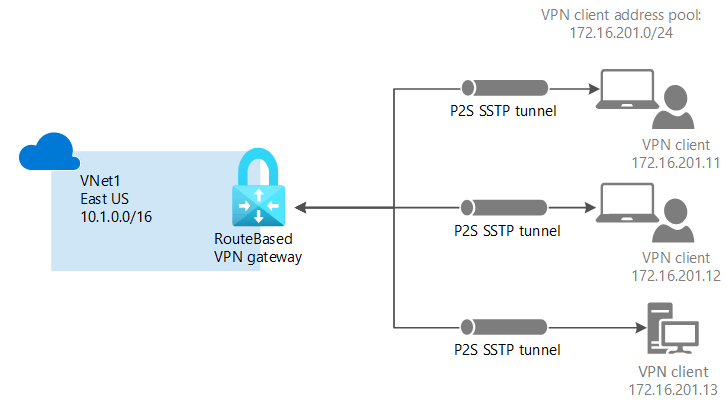
This article helps you securely connect individual clients running Windows, Linux, or macOS to an Azure VNet. point-to-site VPN connections are useful when you want to connect to your VNet from a remote location, such when you are telecommuting from home or a conference. You can also use P2S instead of a Site-to-Site VPN when you have only a few clients that need to connect to a VNet. Point-to-site connections do not require a VPN device or a public-facing IP address. P2S creates the VPN connection over either SSTP (Secure Socket Tunneling Protocol), or IKEv2. For more information about point-to-site VPN, see About point-to-site VPN.
For more information about point-to-site VPN, see About point-to-site VPN. To create this configuration using the Azure PowerShell, see Configure a point-to-site VPN using Azure PowerShell.
Prerequisites
Verify that you have an Azure subscription. If you don't already have an Azure subscription, you can activate your MSDN subscriber benefits or sign up for a free account.
Multiple authentication types on the same VPN gateway are only supported with OpenVPN tunnel type.
Example values
You can use the following values to create a test environment, or refer to these values to better understand the examples in this article:
- VNet Name: VNet1
- Address space: 10.1.0.0/16
For this example, we use only one address space. You can have more than one address space for your VNet. - Subnet name: FrontEnd
- Subnet address range: 10.1.0.0/24
- Subscription: If you have more than one subscription, verify that you are using the correct one.
- Resource Group: TestRG1
- Location: East US
- GatewaySubnet: 10.1.255.0/27
- SKU: VpnGw2
- Generation: Generation 2
- Gateway type: VPN
- VPN type: Route-based
- Public IP address name: VNet1GWpip
- Connection type: Point-to-site
- Client address pool: 172.16.201.0/24
VPN clients that connect to the VNet using this point-to-site connection receive an IP address from the client address pool.
Create a virtual network
Before beginning, verify that you have an Azure subscription. If you don't already have an Azure subscription, you can activate your MSDN subscriber benefits or sign up for a free account.
Note
When you use a virtual network as part of a cross-premises architecture, be sure to coordinate with your on-premises network administrator to carve out an IP address range that you can use specifically for this virtual network. If a duplicate address range exists on both sides of the VPN connection, traffic will route in an unexpected way. Additionally, if you want to connect this virtual network to another virtual network, the address space can't overlap with the other virtual network. Plan your network configuration accordingly.
Sign in to the Azure portal.
In Search resources, service, and docs (G+/) at the top of the portal page, enter virtual network. Select Virtual network from the Marketplace search results to open the Virtual network page.
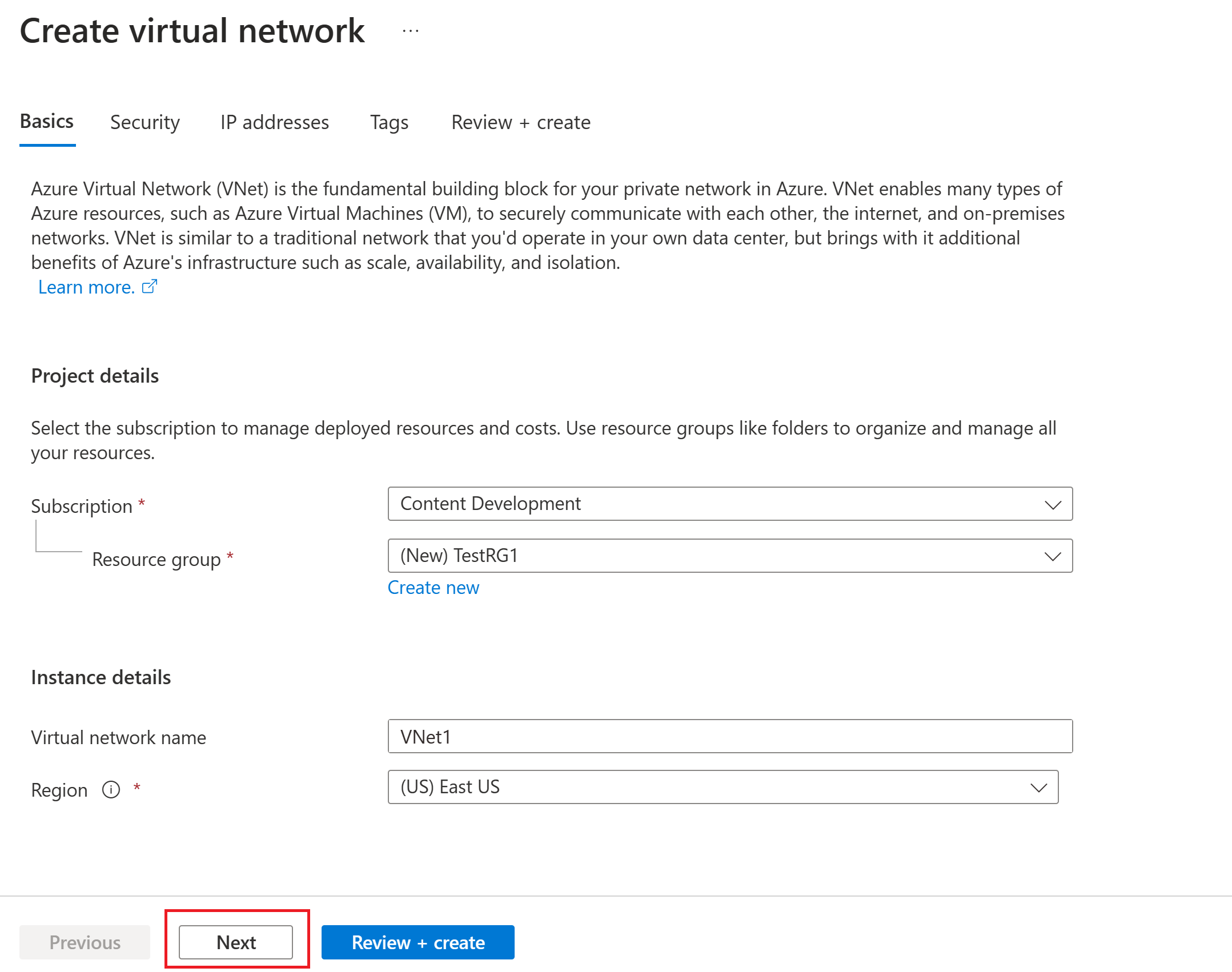
On the Virtual network page, select Create to open the Create virtual network page.
On the Basics tab, configure the virtual network settings for Project details and Instance details. You see a green check mark when the values you enter are validated. You can adjust the values shown in the example according to the settings that you require.
- Subscription: Verify that the subscription listed is the correct one. You can change subscriptions by using the dropdown box.
- Resource group: Select an existing resource group or select Create new to create a new one. For more information about resource groups, see Azure Resource Manager overview.
- Name: Enter the name for your virtual network.
- Region: Select the location for your virtual network. The location determines where the resources that you deploy to this virtual network will reside.
Select Next or Security to go to the Security tab. For this exercise, leave the default values for all the services on this page.
Select IP Addresses to go to the IP Addresses tab. On the IP Addresses tab, configure the settings.
IPv4 address space: By default, an address space is automatically created. You can select the address space and adjust it to reflect your own values. You can also add a different address space and remove the default that was automatically created. For example, you can specify the starting address as 10.1.0.0 and specify the address space size as /16. Then select Add to add that address space.
+ Add subnet: If you use the default address space, a default subnet is created automatically. If you change the address space, add a new subnet within that address space. Select + Add subnet to open the Add subnet window. Configure the following settings, and then select Add at the bottom of the page to add the values.
- Subnet name: An example is FrontEnd.
- Subnet address range: The address range for this subnet. Examples are 10.1.0.0 and /24.
Review the IP addresses page and remove any address spaces or subnets that you don't need.
Select Review + create to validate the virtual network settings.
After the settings are validated, select Create to create the virtual network.
Virtual network gateway
In this step, you create the virtual network gateway for your VNet. Creating a gateway can often take 45 minutes or more, depending on the selected gateway SKU.
Note
The Basic gateway SKU does not support OpenVPN tunnel type.
The virtual network gateway requires a specific subnet named GatewaySubnet. The gateway subnet is part of the IP address range for your virtual network and contains the IP addresses that the virtual network gateway resources and services use.
When you create the gateway subnet, you specify the number of IP addresses that the subnet contains. The number of IP addresses needed depends on the VPN gateway configuration that you want to create. Some configurations require more IP addresses than others. It's best to specify /27 or larger (/26, /25, etc.) for your gateway subnet.
If you see an error that specifies that the address space overlaps with a subnet, or that the subnet isn't contained within the address space for your virtual network, check your virtual network address range. You might not have enough IP addresses available in the address range you created for your virtual network. For example, if your default subnet encompasses the entire address range, there are no IP addresses left to create more subnets. You can either adjust your subnets within the existing address space to free up IP addresses or specify another address range and create the gateway subnet there.
In Search resources, services, and docs (G+/), enter virtual network gateway. Locate Virtual network gateway in the Marketplace search results and select it to open the Create virtual network gateway page.
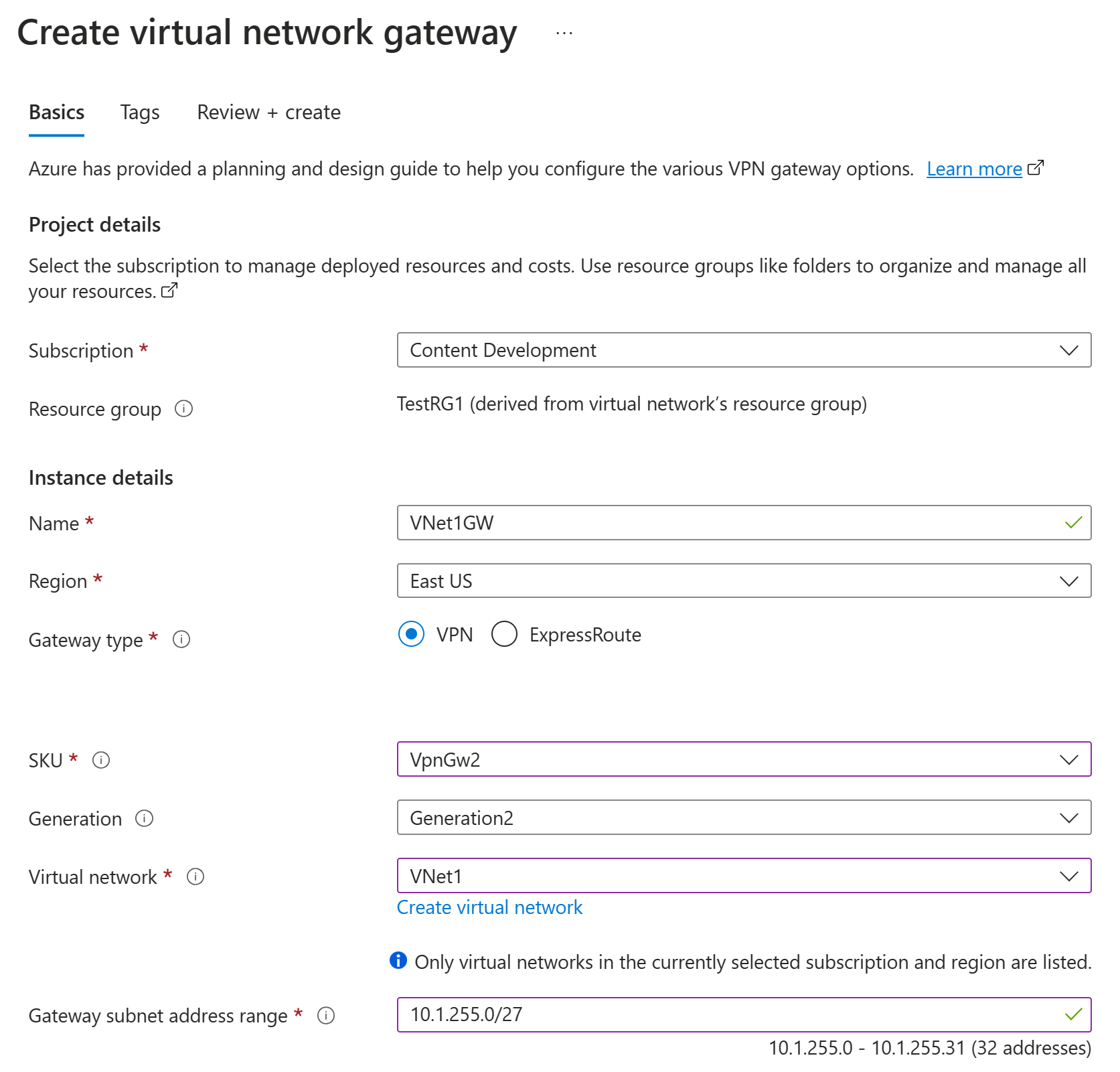
On the Basics tab, fill in the values for Project details and Instance details.
Subscription: Select the subscription you want to use from the dropdown list.
Resource group: This setting is autofilled when you select your virtual network on this page.
Name: Name your gateway. Naming your gateway isn't the same as naming a gateway subnet. It's the name of the gateway object you're creating.
Region: Select the region in which you want to create this resource. The region for the gateway must be the same as the virtual network.
Gateway type: Select VPN. VPN gateways use the virtual network gateway type VPN.
SKU: From the dropdown list, select the gateway SKU that supports the features you want to use. See Gateway SKUs. In the portal, the SKUs available in the dropdown list depend on the
VPN typeyou select. The Basic SKU can only be configured using Azure CLI or PowerShell. You can't configure the Basic SKU in the Azure portal.Generation: Select the generation you want to use. We recommend using a Generation2 SKU. For more information, see Gateway SKUs.
Virtual network: From the dropdown list, select the virtual network to which you want to add this gateway. If you can't see the virtual network for which you want to create a gateway, make sure you selected the correct subscription and region in the previous settings.
Gateway subnet address range or Subnet: The gateway subnet is required to create a VPN gateway.
At this time, this field can show various different settings options, depending on the virtual network address space and whether you already created a subnet named GatewaySubnet for your virtual network.
If you don't have a gateway subnet and you don't see the option to create one on this page, go back to your virtual network and create the gateway subnet. Then, return to this page and configure the VPN gateway.
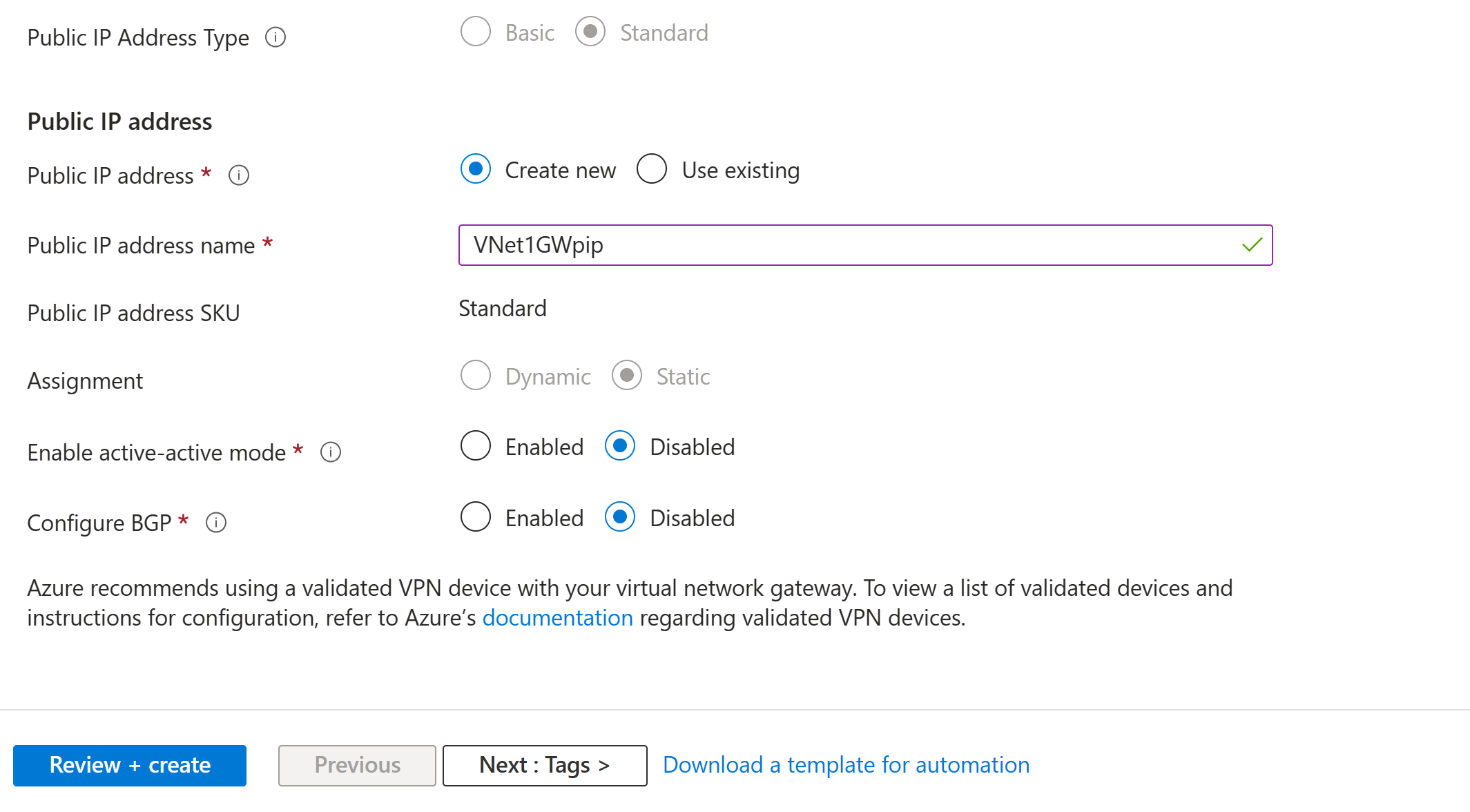
Specify the values for Public IP address. These settings specify the public IP address object that gets associated to the VPN gateway. The public IP address is assigned to this object when the VPN gateway is created. The only time the primary public IP address changes is when the gateway is deleted and re-created. It doesn't change across resizing, resetting, or other internal maintenance/upgrades of your VPN gateway.
- Public IP address type: If you are presented with this option, select Standard. The Basic public IP address SKU is only supported for Basic SKU VPN gateways.
- Public IP address: Leave Create new selected.
- Public IP address name: In the text box, enter a name for your public IP address instance.
- Public IP address SKU: Setting is autoselected.
- Assignment: The assignment is typically autoselected. For the Standard SKU, assignment is always Static.
- Enable active-active mode: Select Disabled. Only enable this setting if you're creating an active-active gateway configuration.
- Configure BGP: Select Disabled, unless your configuration specifically requires this setting. If you do require this setting, the default ASN is 65515, although this value can be changed.
Select Review + create to run validation.
After validation passes, select Create to deploy the VPN gateway.
You can see the deployment status on the Overview page for your gateway. A gateway can often take 45 minutes or more to fully create and deploy. After the gateway is created, you can view the IP address that has been assigned to it by looking at the virtual network in the portal. The gateway appears as a connected device.
Important
When you work with gateway subnets, avoid associating a network security group (NSG) to the gateway subnet. Associating a network security group to this subnet might cause your virtual network gateway (VPN and ExpressRoute gateways) to stop functioning as expected. For more information about network security groups, see What is a network security group?.
Client address pool
The client address pool is a range of private IP addresses that you specify. The clients that connect over a point-to-site VPN dynamically receive an IP address from this range. Use a private IP address range that does not overlap with the on-premises location that you connect from, or the VNet that you want to connect to. If you configure multiple protocols and SSTP is one of the protocols, then the configured address pool is split between the configured protocols equally.
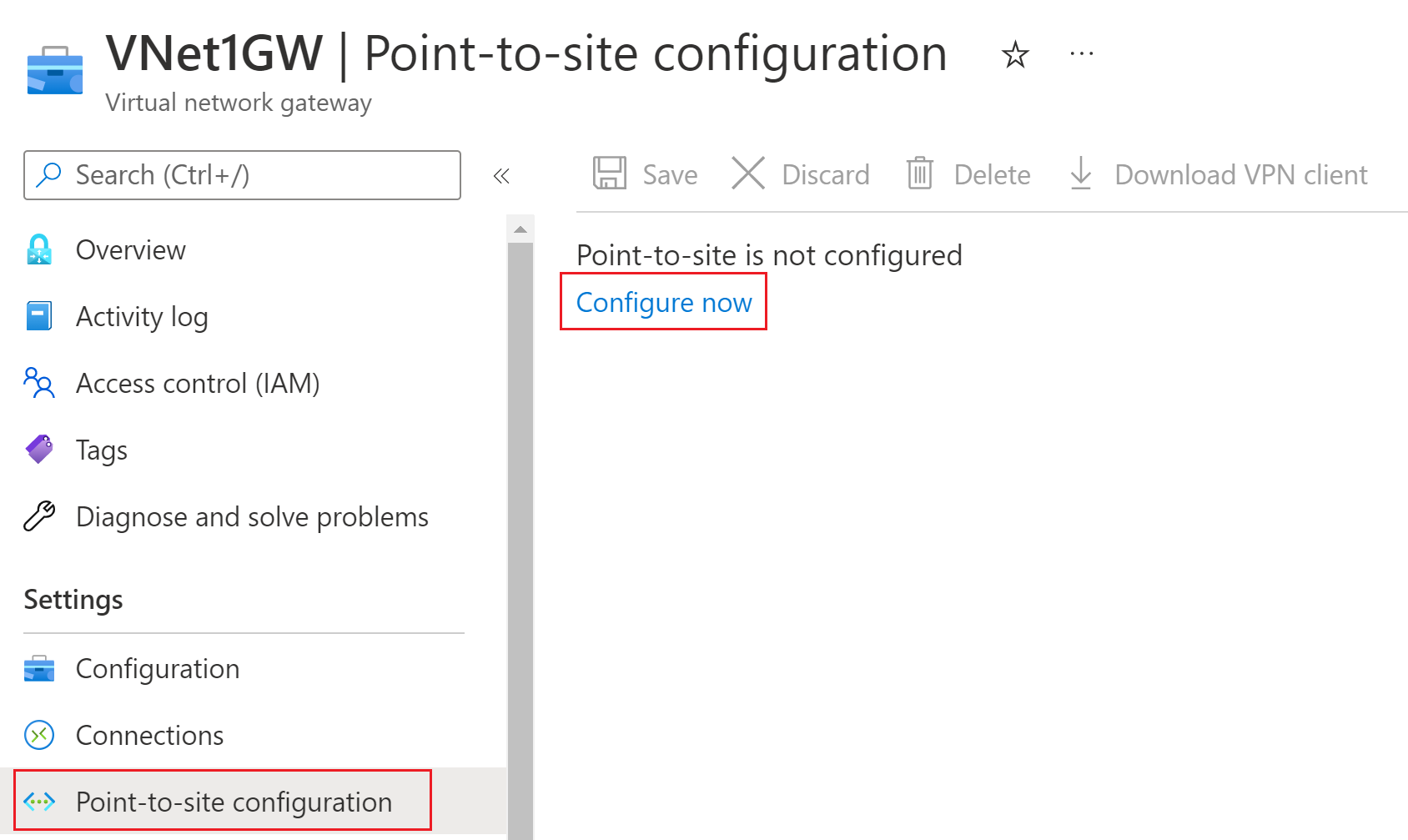
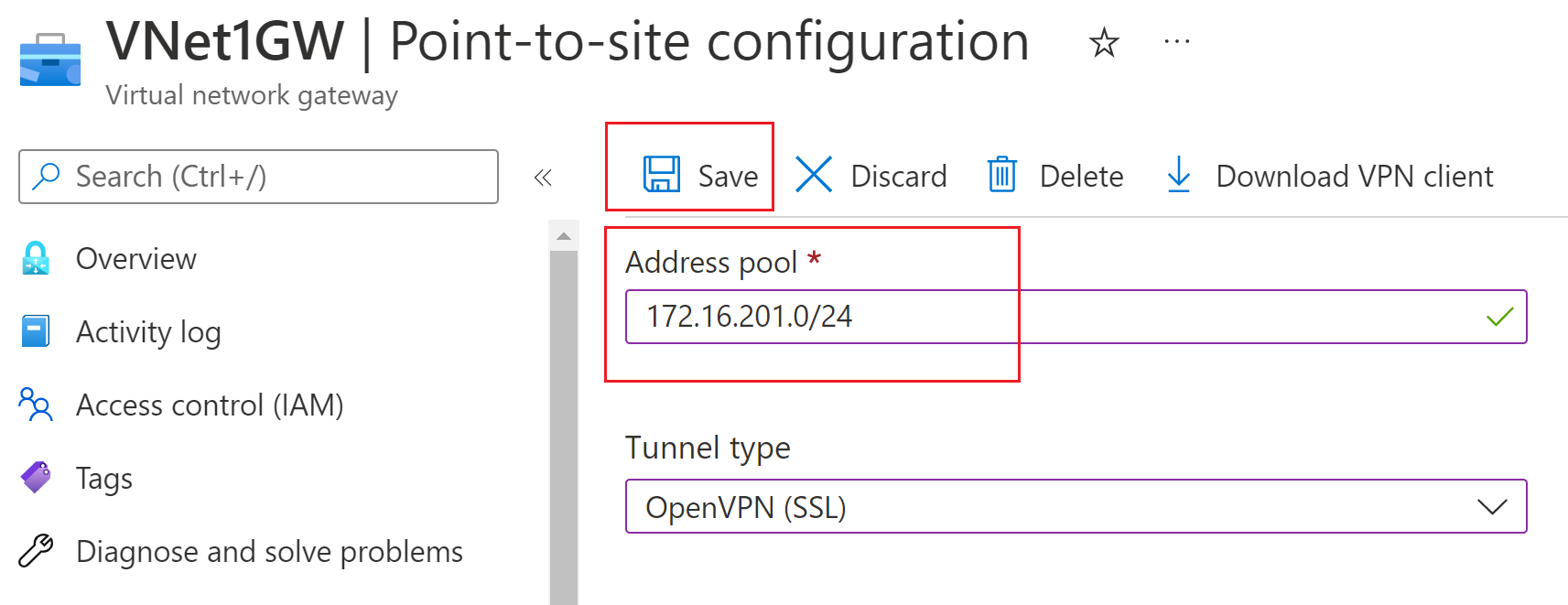
Once the virtual network gateway has been created, navigate to the Settings section of the virtual network gateway page. In Settings, select Point-to-site configuration. Select Configure now to open the configuration page.
On the Point-to-site configuration page, you can configure a variety of settings. In the Address pool box, add the private IP address range that you want to use. VPN clients dynamically receive an IP address from the range that you specify. The minimum subnet mask is 29 bit for active/passive and 28 bit for active/active configuration.
Continue to the next section to configure authentication and tunnel types.
Authentication and tunnel types
In this section, you configure authentication type and tunnel type. On the Point-to-site configuration page, if you don't see Tunnel type or Authentication type, your gateway is using the Basic SKU. The Basic SKU does not support IKEv2 or RADIUS authentication. If you want to use these settings, you need to delete and recreate the gateway using a different gateway SKU.
Important
The Azure portal is in the process of updating Azure Active Directory fields to Entra. If you see Microsoft Entra ID referenced and you don't see those values in the portal yet, you can select Azure Active Directory values.
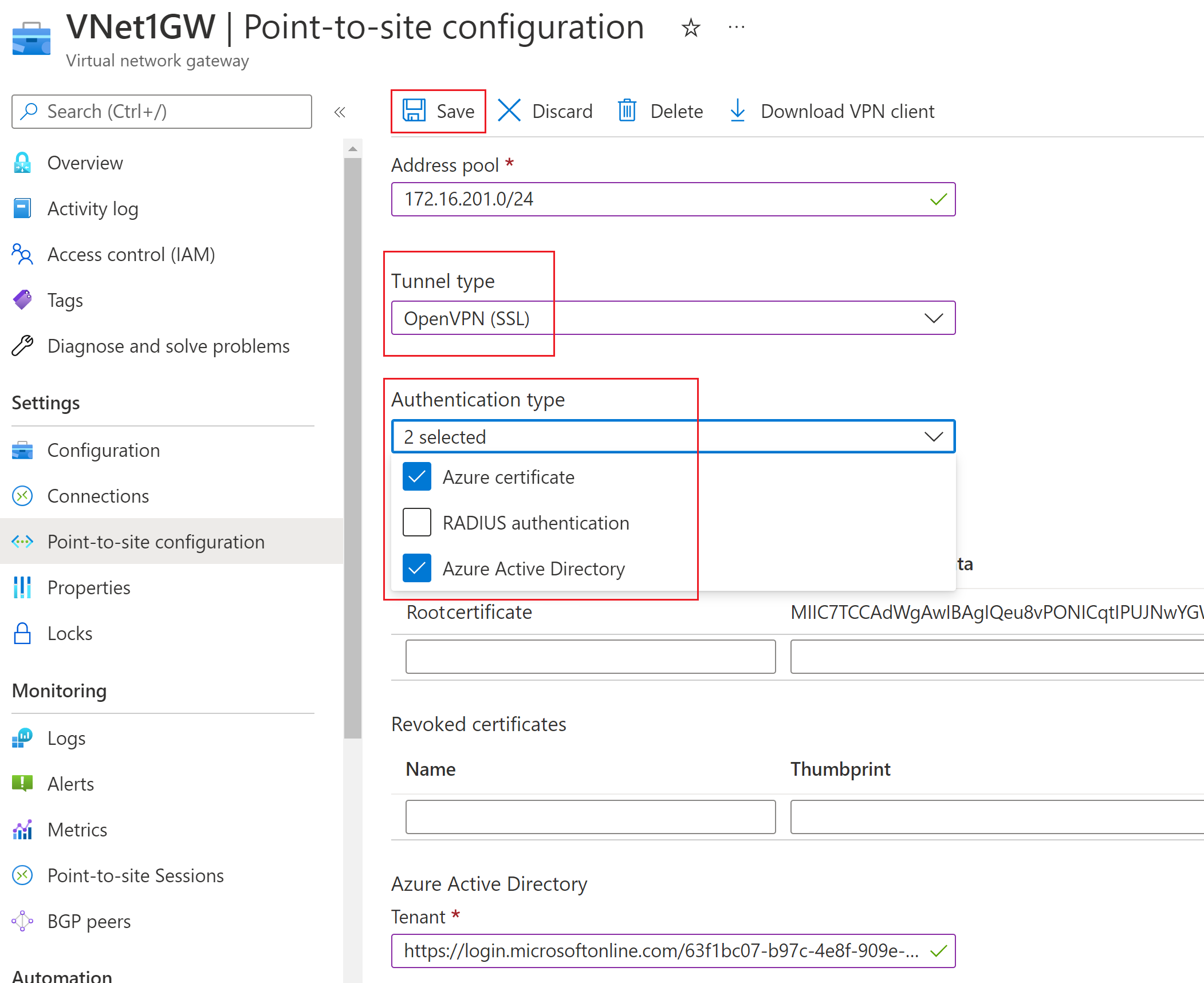
Tunnel type
On the Point-to-site configuration page, select the desired types. Options are:
- OpenVPN (SSL)
- SSTP (SSL)
- IKEv2
- IKEv2 and OpenVPN (SSL)
- IKEv2 and SSTP (SSL)
Authentication type
For Authentication type, select the desired types. Options are:
- Azure certificate
- RADIUS
- Microsoft Entra ID
See the below table to check what authentication mechanisms are compatible with selected tunnel types.
| Tunnel Type | Authentication Mechanism |
|---|---|
| OpenVPN | Any subset of Microsoft Entra ID, Radius Auth and Azure Certificate |
| SSTP | Radius Auth/ Azure Certificate |
| IKEv2 | Radius Auth/ Azure Certificate |
| IKEv2 and OpenVPN | Radius Auth/ Azure Certificate/ Microsoft Entra ID and Radius Auth/ Microsoft Entra ID and Azure Certificate |
| IKEv2 and SSTP | Radius Auth/ Azure Certificate |
Note
For tunnel type "IKEv2 and OpenVPN" and selected authentication mechanisms "Microsoft Entra ID and Radius" or "Microsoft Entra ID and Azure Certificate", Microsoft Entra ID will only work for OpenVPN since it is not supported by IKEv2
Depending on the authentication type(s) selected, you will see different configuration setting fields that will have to be filled in. Fill in the required information and select Save at the top of the page to save all of the configuration settings.
For more information about authentication type, see:
VPN client configuration package
VPN clients must be configured with client configuration settings. The VPN client configuration package contains files with the settings to configure VPN clients in order to connect to a VNet over a P2S connection.
For instructions to generate and install VPN client configuration files, use the article that pertains to your configuration:
| Authentication | Tunnel type | Generate config files | Configure VPN client |
|---|---|---|---|
| Azure certificate | IKEv2, SSTP | Windows | Native VPN client |
| Azure certificate | OpenVPN | Windows | - OpenVPN client - Azure VPN client |
| Azure certificate | IKEv2, OpenVPN | macOS-iOS | macOS-iOS |
| Azure certificate | IKEv2, OpenVPN | Linux | Linux |
| Microsoft Entra ID | OpenVPN (SSL) | Windows | Windows |
| Microsoft Entra ID | OpenVPN (SSL) | macOS | macOS |
| RADIUS - certificate | - | Article | Article |
| RADIUS - password | - | Article | Article |
| RADIUS - other methods | - | Article | Article |
Point-to-site FAQ
For point-to-site FAQ information, see the point-to-site sections of the VPN Gateway FAQ.
Next steps
Once your connection is complete, you can add virtual machines to your virtual networks. For more information, see Virtual Machines. To understand more about networking and virtual machines, see Azure and Linux VM network overview.
For P2S troubleshooting information, Troubleshooting Azure point-to-site connections.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for