Examine the anti-malware pipeline
Exchange Online Protection (EOP) uses multiple anti-malware engines. This design enables it to offer multilayered protection to catch all known malware. Messages transported through the service are scanned for malware (viruses and spyware). If malware is detected, the message is deleted. Notifications may also be sent to senders or administrators when an infected message is deleted and not delivered. You can also choose to replace infected attachments with either default or custom messages that notify the recipients of the malware detection.
Note
Anti-malware scanning can't be disabled.
For standalone EOP customers, the service only scans inbound and outbound messages that are routed by the service. It doesn't scan messages sent from a sender in one organization to a recipient in the same organization. However, for another layer of defense, you can pair the service with the built-in anti-malware protection capabilities of Exchange Server. By doing so, internal messages will be scanned for malware.
For Exchange Online customers and the EOP that's included in Exchange Enterprise CAL with Services for on-premises Exchange customers, EOP scans inbound and outbound messages that are routed by the service. It also scans internal messages sent from a sender in an organization to a recipient in the same organization.
Anti-malware policies in EOP
In Microsoft 365 organizations with mailboxes in Exchange Online or standalone Exchange Online Protection (EOP) organizations without Exchange Online mailboxes, email messages are automatically protected against malware by EOP. EOP uses anti-malware policies for malware protection settings.
Microsoft 365 comes with a default anti-malware policy. Admins can view, edit, and configure (but not delete) the default anti-malware policy to meet the needs of their organizations. For greater granularity, they can also create custom anti-malware policies that apply to specific users, groups, or domains in their organization. Custom policies always take precedence over the default policy. However, an organization can change the priority (that is, the running order) of its custom policies.
An organization can configure anti-malware policies in the Microsoft Defender portal. It can also configure anti-malware policies in Exchange Online PowerShell for Microsoft 365 organizations with mailboxes in Exchange Online. For organizations without Exchange Online mailboxes, they can use standalone EOP PowerShell.
To add, modify, and delete anti-malware policies, you must be a member of the Organization Management or Security Administrator role groups. For read-only access to anti-malware policies, you must be a member of the Global Reader or Security Reader role groups.
The anti-malware pipeline
Organizations that have hosted mailboxes in Exchange Online rely on Exchange Online Protection (EOP) to protect incoming and outgoing mail. When an organization joins Microsoft 365, an administrator must add Microsoft 365 specific MX and TXT records to their domain name in DNS.
- The MX record ensures that email sent to the tenant’s domain will arrive in mailboxes hosted in Exchange Online through the EOP service.
- The Sender Protection Framework (SPF) record is a special type of TXT record in DNS. It identifies a host as a valid sender for the organization's domain.
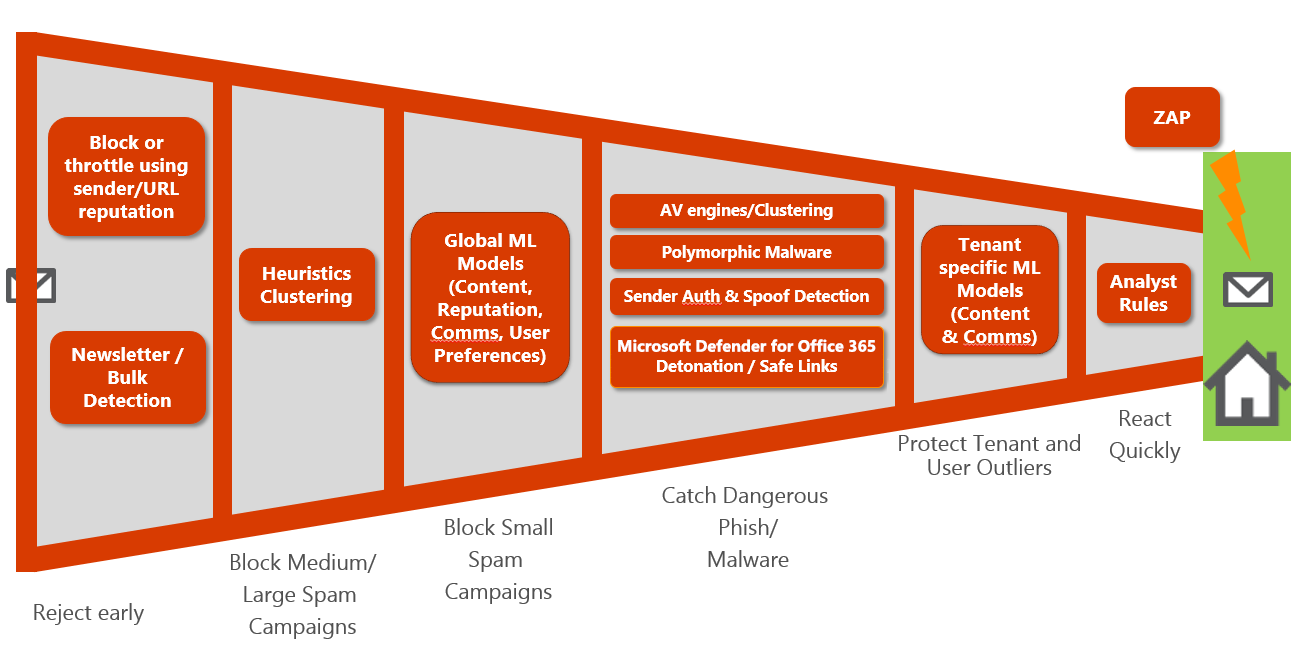
Before mail enters the Microsoft 365 network and is processed by EOP, techniques such as IP and sender reputation, combined with heuristics, catch a sizeable amount of spam and bulk email at the first entry point in Microsoft 365. Once mail passes through the first entry point in Microsoft 365, it's scanned by multiple signature-based anti-virus scanners. This process alone is effective in catching up to 80% of commodity malware coming into the network. But malicious attachments that are heavily modified or released with many different variants coming out at the same time can still get through.
Once mail enters the Microsoft 365 network, EOP scans individual files using a technique called reputation block. With reputation block, EOP compares file attachments with the results of scans that were previously completed throughout Microsoft 365. It then checks to see if there are specific files – or pieces of files – that were previously identified as malicious that appear to match something in an incoming message.
Heuristic clustering is used to identify mail as suspicious based on an analysis of delivery patterns. When this process occurs, a sample from a cluster is sent to a hypervisor sandbox environment where the file is opened for further analysis. This analysis includes:
- Checking for anomalies such as changes in memory, the registry, or encryption of the hard drive.
- Checking for changes in network traffic, such as connections to hacker’s command and control servers.
- Identifying when malware tries to obfuscate itself or use evasion techniques.
Once these signals are collected, the results are run through a machine-learning (ML) model and a set of static rules. This process determines whether the file is suspicious or, in fact, truly malicious.
If Microsoft Defender for Office 365 is enabled in the tenant, it extends the protection of EOP. It provides this extra protection by scanning mail that made it through the filters and techniques described earlier.
- Microsoft Defender's Safe Attachments feature scans all file attachments. In fact, it scans files even if they don't appear to be suspicious. By doing so, it protects against malware that doesn’t have a known anti-virus signature. Attachments are opened in the same sandboxing environment used by EOP and analyzed for behavioral changes to the registry, memory, and so on.
- After the Safe Attachments process has completed, the actual body of the message - including the message headers - is run through EOP’s anti-spam, phish, and spoof filters.
- If there are any URLs embedded in the message body, and Microsoft Defender for Office 365 is enabled in the tenant, then its Safe Links feature checks the link against a list of known malicious URLs. This list is updated approximately every 20 minutes.
- Finally, Microsoft is also engaged with a team of security analysts, or cyber hunters. These analysts identify new threat campaigns and quickly implement rules to further protect the Microsoft 365 network against cyber-attacks.
The anti-malware pipeline that's composed of EOP and Microsoft Defender for Office 365 provides protection against all types of spam and advanced threats. This protection is provided through a multi-layered, defense-in-depth approach to solving email security.
Create anti-malware policies in the Microsoft Defender portal
When an organization creates a custom anti-malware policy in the Microsoft Defender portal, it creates:
- the malware filter rule
- the associated malware filter policy
The same name is used for both the malware filter rule and policy. You must complete the following steps to create an anti-malware policy in the Microsoft Defender portal:
Use one of the following methods to navigate to the Microsoft Defender portal:
- In the Microsoft 365 admin center, select Show all in the navigation pane. Under Admin centers, select Security.
- In your browser, enter the following URL in the address bar: https://security.microsoft.com
In the Microsoft Defender portal, under the Email & Collaboration section in the navigation pane, select Policies & rules.
On the Policies & rules page, in the list of policies, select Threat policies.
On the Threat policies page, under the Policies section,select Anti-malware.
On the Anti-malware page, the Default policy is displayed in the list of policies. Select Create to create a custom policy.
The policy wizard opens. On the Name your policy page, configure the following settings:
- Name. Enter a unique, descriptive name for the policy.
- Description. Optionally enter a description of the policy.
When you're finished, select Next.
On the Users and domains page, identify the internal recipients that the policy applies to (recipient conditions) and then select Next:
Users. The specified mailboxes, mail users, or mail contacts.
Groups
- Members of the specified distribution groups or mail-enabled security groups.
- The specified Microsoft 365 Groups.
Domains. All recipients in the specified accepted domains in your organization.
Select inside the appropriate box, start typing a value, and select the value that you want from the results. Repeat this process as many times as necessary. To remove an existing value, select the X icon next to the value.
For users or groups, you can use most identifiers (name, display name, alias, email address, account name, etc.). However, the corresponding display name is shown in the results. For users, enter an asterisk (*) by itself to see all available values.
Multiple values in the same condition use OR logic (for example, <recipient1> or <recipient2>). Different conditions use AND logic (for example, <recipient1> and <member of group 1>).
Select the Exclude these users, groups, and domains option to add exceptions for the internal recipients that the policy applies to (recipient exceptions). If you select this option, you must then configure the exceptions. The settings and behavior are exactly like the conditions.
When you're finished, select Next.
On the Protection settings page that appears, configure the following settings:
Enable the common attachments filter. If you select this option, messages with the specified attachments are treated as malware and are automatically quarantined. You can modify the default list by selecting Customize file types.
Enable zero-hour auto purge for malware. If you select this option, ZAP quarantines malware messages that have already been delivered. For more information, see Zero-hour auto purge (ZAP) in Exchange Online. Select one of these values:
Quarantine policy. Select the quarantine policy that applies to messages that are quarantined as malware. Quarantine policies define what users are able to do to quarantined messages, and whether users receive quarantine notifications. For more information, see Quarantine policies.
A blank value means the default quarantine policy is used (AdminOnlyAccessPolicy for malware detections). When you later edit the anti-malware policy or view the settings, the default quarantine policy name is shown.
Notify recipients when messages are quarantined as malware. If you select this option, the message is quarantined. A copy of the message is delivered to the recipients. Every attachment (not just malware attachments) is replaced with a single text file named Malware Alert Text.txt. The default text in the replacement text file is described in Anti-malware policies. To use custom text instead, enter the text in the Custom notification text to recipient box. If you don't select this option, the message is silently quarantined.
Whether you select this option or not, the quarantine policy determines whether recipients receive quarantine notifications (email notifications for messages that were quarantined as malware).
Sender Notifications. Select none, one, or both of these options:
- Notify internal senders when messages are quarantined as malware. An internal sender is inside the organization.
- Notify external senders when messages are quarantined as malware. An external sender is outside the organization.
Admin notifications. Admin notifications are sent only for attachments that are classified as malware. Select none, one, or both of these options:
- Notify an admin about undelivered messages from internal senders. If you select this option, enter a notification email address in the Admin email address box that appears.
- Notify an admin about undelivered messages from external senders. If you select this option, enter a notification email address in the Admin email address box that appears.
Customize notifications. These settings replace the default notification text that's used for senders or admins. For more information about the default values, see Anti-malware policies.
- Use customized notification text. If you select this option, you must use the From name and From address boxes to specify the sender's name and email address that's used in the customized notification message.
- Customize notifications for messages from internal senders. If you chose to notify senders or admins about undeliverable messages from internal senders, you must use the Subject and Message boxes to specify the subject and message body of the custom notification message.
- Customize notifications for messages from external senders. If you chose to notify senders or admins about undeliverable messages from external senders, you must use the Subject and Message boxes to specify the subject and message body of the custom notification message.
When you're finished, select Next.
On the Review page that appears, review your settings. You can select Edit in each section to modify the settings within the section. Or you can select Back or select the specific page in the wizard.
When you're finished, select Submit.
On the confirmation page that appears, select Done.
Create anti-malware policies using PowerShell
Creating an anti-malware policy in PowerShell is a two-step process:
- Create the malware filter policy.
- Create the malware filter rule that specifies the malware filter policy that the rule applies to.
Keep in mind the following items when using PowerShell to create anti-malware policies:
You can create a new malware filter rule and assign an existing, unassociated malware filter policy to it.
A malware filter rule can't be associated with more than one malware filter policy.
There are two settings that you can configure on new anti-malware policies in PowerShell that aren't available in the Microsoft Defender portal until after you create the policy:
- Create the new policy as disabled (Enabled
$falseon the New-MalwareFilterRule cmdlet). - Set the priority of the policy during creation (Priority <Number>) on the New-MalwareFilterRule cmdlet).
- Create the new policy as disabled (Enabled
A new malware filter policy that you create in PowerShell isn't visible in the Microsoft Defender portal until you assign the policy to a malware filter rule.
Step 1: Use PowerShell to create a malware filter policy
Note
In the cloud-based service, the Action parameter values DeleteMessage, DeleteAttachmentAndUseDefaultAlert, and DeleteAttachmentAndUseCustomAlert don't delete messages. Instead, the messages are always quarantined.
To create a malware filter policy, use this syntax:
New-MalwareFilterPolicy -Name "<PolicyName>" [-Action <DeleteMessage | DeleteAttachmentAndUseDefaultAlert | DeleteAttachmentAndUseCustomAlert>] [-AdminDisplayName "<OptionalComments>"] [-CustomNotifications <$true | $false>] [<Inbound notification options>] [<Outbound notification options>] [-QuarantineTag <QuarantineTagName>]
The following example creates a new malware filter policy named Contoso Malware Filter Policy with these settings:
- Quarantine messages that contain malware without notifying the recipients. It doesn't use the Action parameter because the default value is DeleteMessage.
- Don't notify the message sender when malware is detected in the message. It doesn't use the EnableExternalSenderNotifications or EnableInternalSenderNotifications parameters, and the default value for both is
$false. - Notify the administrator admin@contoso.com when malware is detected in a message from an internal sender.
- The default quarantine policy for malware detections is used. It doesn't use the QuarantineTag parameter.
New-MalwareFilterPolicy -Name "Contoso Malware Filter Policy" -EnableInternalSenderAdminNotifications $true -InternalSenderAdminAddress admin@contoso.com
Step 2: Use PowerShell to create a malware filter rule
To create a malware filter rule, use this syntax:
New-MalwareFilterRule -Name "<RuleName>" -MalwareFilterPolicy "<PolicyName>" <Recipient filters> [<Recipient filter exceptions>] [-Comments "<OptionalComments>"]
The following example creates a new malware filter rule named Contoso Recipients with these settings:
- The malware filter policy named Contoso Malware Filter Policy is associated with the rule.
- The rule applies to recipients in the contoso.com domain.
New-MalwareFilterRule -Name "Contoso Recipients" -MalwareFilterPolicy "Contoso Malware Filter Policy" -RecipientDomainIs contoso.com
Use the EICAR.txt file to verify your anti-malware policy settings
Important
The EICAR.txt file isn't a virus. The European Institute for Computer Antivirus Research (EICAR) developed this file to safely test anti-virus installations and settings. Use the EICAR.txt file to verify your anti-malware policy settings. In your desktop anti-virus program, be sure to exclude the EICAR.txt from scanning. Otherwise, the file will be quarantined.
Open Notepad and then copy and paste the following line of text into an empty file:
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*Be sure that these text characters are the only characters in the file. The file size should be 68 bytes.
Save the file as EICAR.txt.
Send an email message that contains the EICAR.txt file as an attachment. Use an email client that won't automatically block the file. Use an email service that doesn't automatically block outbound spam. Use your anti-malware policy settings to determine the following scenarios to test:
- Email from an internal mailbox to an internal recipient.
- Email from an internal mailbox to an external recipient.
- Email from an external mailbox to an internal recipient.
Verify the message was quarantined. You should also verify the recipient and sender notification results based on your anti-malware policy settings. For example:
- Recipients aren't notified, or recipients receive the original message with the EICAR.txt attachment replaced by Malware Alert Text.txt that contains the default or customized text.
- Internal or external senders are notified with the default or customized notification messages.
- The admin email address that you specified is notified for internal or external message senders with the default or customized notification messages.
Delete the EICAR.txt file after your testing is complete (so other users aren't alarmed by it).
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”