Explore directory synchronization
Directory synchronization is the synchronization of identities or objects (users, groups, contacts, and computers) between two different directories. For Microsoft 365 deployments, synchronization is typically between an organization's on-premises Active Directory environment and Microsoft Entra ID. Directory synchronization isn't limited to any one specific directory. In fact, it can include other directories such as HR databases and an LDAP directory, as seen in the following diagram.
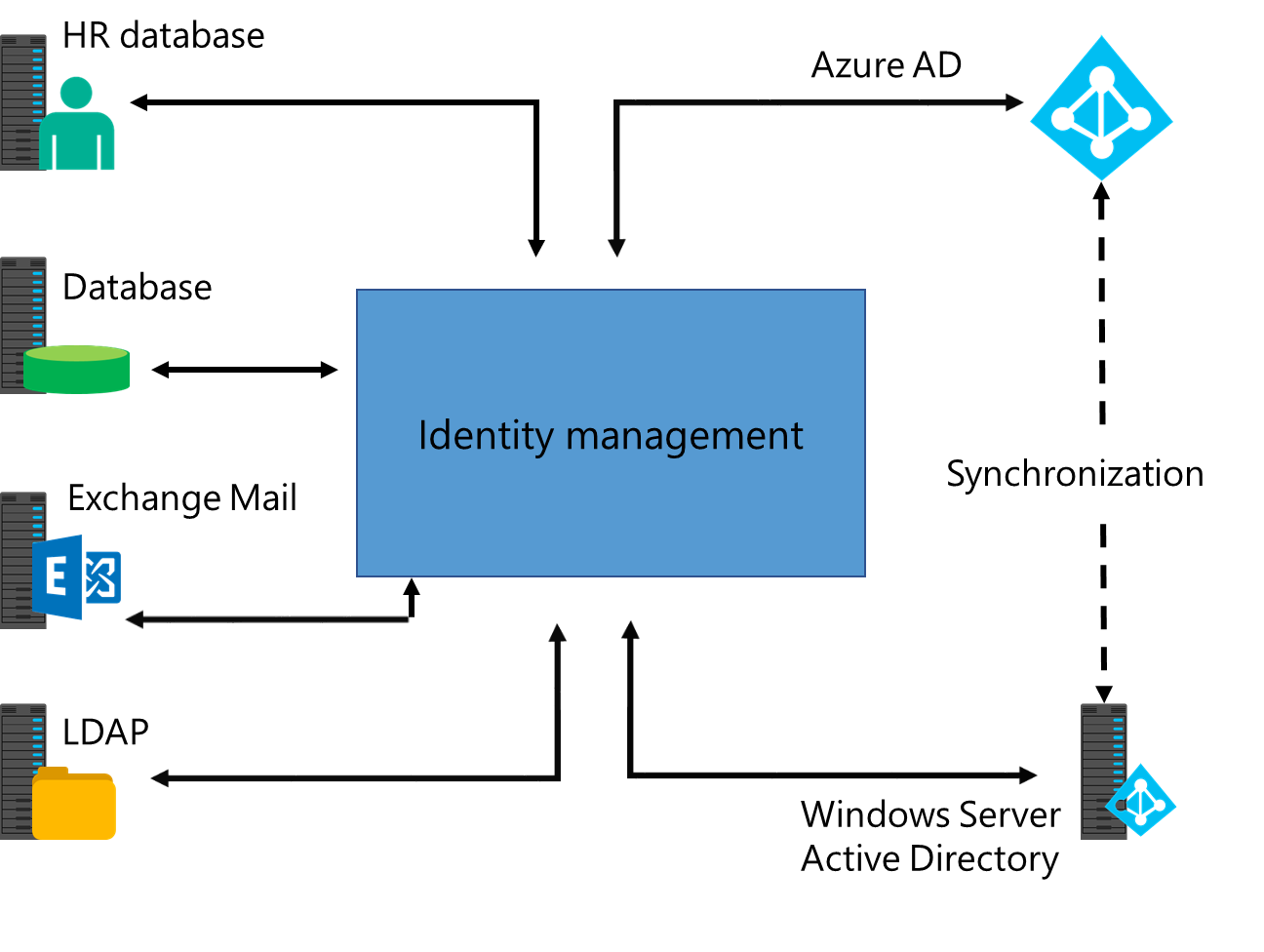
In Microsoft 365, directory synchronization is commonly used to synchronize in one direction, from on-premises to Microsoft Entra ID. However, Microsoft's recommended synchronization tool, Microsoft Entra Connect, can write back specific objects and attributes to the on-premises directory. This feature creates a form of two-way synchronization.
Besides writing back directory objects, directory synchronization can also provide two-way synchronization of user passwords. Microsoft Entra Connect is a directory synchronization tool that provides two-way synchronization. It should be installed on a dedicated computer in an organization's on-premises environment.
Integrating on-premises directories with Microsoft Entra ID helps improve user productivity. Users will no longer have to spend time typing in passwords for accessing both cloud and on-premises resources.
With this integration, users and organizations can take advantage of the following features:
- Hybrid identity. Organizations that use Active Directory and then connect to Microsoft Entra ID can provide users with a common hybrid identity across on-premises or cloud-based services, including consistent group membership.
- Single Sign-On (SSO). Because all the servers and services used in SSO are mastered and controlled on-premises, organizations can have confidence in knowing their user identities and information are protected.
- Multifactor authentication (MFA). MFA provides enhanced authentication security with the cloud service. MFA is based on the premise that an unauthorized actor won't have all the information required for access.
- AD policies. Administrators can use policies set through Active Directory to provide conditional access. These AD policies can be based on application resource, device and user identity, network location, and multifactor authentication. Conditional access can be provided without having to do extra tasks in the cloud.
- Use common identity. Users can apply their common identity through accounts in Microsoft Entra ID to Microsoft 365, Intune, SaaS apps, and non-Microsoft applications.
- Common identity model. Developers can build applications that use the common identity model. This design integrates applications into on-premises Active Directory when using services such as Microsoft Entra application proxy or Azure for cloud-based applications).
Additional reading. For more information, see Get started with conditional access in Microsoft Entra ID.