Visualize risk
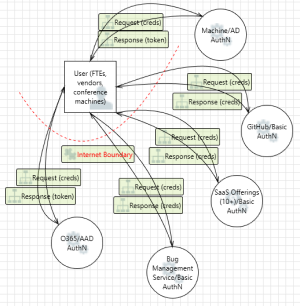
The next step in the infrastructure threat modeling process is to create a data-flow diagram.
General assumptions
To build this diagram, we make the following assumptions:
- Zero trust - The data-flow starts from outside of the corporate network and can't be trusted.
- Context level - The data-flow diagram begins with a high-level context diagram, followed by more in-depth diagrams as needed. For more information, see Provide context with the right depth layer module from the Threat Modeling Security Fundamentals learning path.
Elements
Process

What is process?
Process is a task that receives, modifies, or redirects input to output.
Process context to include
| Context | Questions |
|---|---|
| Code | Is this process running in C#, C++, Objective C, Java, or a scripting language? |
| Permission level | Does this process need kernel, local, or administration level permissions to run? |
| Service isolation | Is the process running in a sandbox? |
| Input | Can this process accept input from everyone, local accounts, or just administrators? |
| Validation | How does the process parse, handle and accept input? |
| Authentication | Does the process rely on Microsoft Entra ID for authentication? If not, what does it rely on? |
| Authorization | Does it rely on Access Control Lists (ACL) for authorization? If not, what does it rely on? |
Woodgrove process elements
- Microsoft 365
- Open-source bug management service
- SaaS offerings (grouped)
- GitHub
- Machine
- Firewall service
- VPN service
- NAS file share service
- Logging and monitoring service
- NAS backup service
- SQL server
- Build servers (grouped)
- Active directory service
- Removable drive backup service
- Azure Iaas
Process labeling example
Microsoft 365 - Microsoft 365/SaaS/Azure ADauth (user credentials, session token, request/response)
Data-store

What is data store?
Data store refers to permanent and temporary storing of data.
Data store context to include
| Context | Questions |
|---|---|
| Type | Does the system use Azure SQL, cookies, local or some other type of storage? If so, what is it? |
| Function | How is the storage used? Is it used to share data, store backups, security logs, credentials, secrets? |
| Permission level | How is access control implemented? Who has read and write permissions? |
| Extra controls | Is data encrypted? What about the disk? Are digital signatures used? |
Woodgrove data store elements
- Credentials and tokens VPN store
- NAS store
- Logging and monitoring store
- Active directory store
- Removable drive store
Data store labeling example
NAS - (file share, backup, credentials, secrets)
External entity

What is external entity?
External entity is a task, entity, or data store outside of your direct control.
External entity context to include
| Context | Questions |
|---|---|
| Source | Is the entity internal or external? |
| Type | Is the entity human, a service provider, or web service? |
| Authentication | Does the process rely on Microsoft Entra ID for authentication? If not, what does it rely on? |
| Authorization | Does it rely on Access Control Lists (ACL) for authorization? If not, what does it rely on? |
Woodgrove external entity elements
- User
External entity labeling example
User - User/AD (FTE)
Data-flow

What is data-flow?
Data-flow refers to data movement between processes, data stores, and external entities.
Data-flow context to include
| Context | Questions |
|---|---|
| Description | Is the data-flow passing a session token, SQL string, or user credentials? If not, what is it passing? |
| Protocol | Does the flow use HTTPS or SOAP? If not, what does it use? |
| Flow sequence | Is the data-flow enumerated to make it easier to follow the flow sequence? |
| Type | What type of data is in the data-flow? Cookies? XML? SOAP payload? REST payload? JSON payload? |
| Extra controls | Does the data-flow have forgery protection enabled? Other security flags enabled? |
| Authentication | Does the process rely on Microsoft Entra ID for authentication? If not, what does it rely on? |
| Authorization | Does it rely on Access Control Lists (ACL) for authorization? If not, what does it rely on? |
Woodgrove data-flow elements
- Request and responses between element connections
Data-flow labeling example
Data-flow - 1- HTTPS Request(session token)
Trust boundary

What is trust boundary?
Trust Boundary refers to trust zone changes as data flows through the system.
Lines are used to represent large trust zone changes like the internet.
Boxes are used to represent smaller trust zone changes, like a corporate network.
Trust boundary context to include
| Context | Questions |
|---|---|
| Description | Is it a corporate network boundary? internet? Azure subscription? |
Woodgrove trust boundary elements
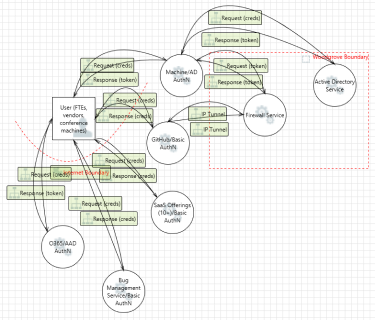
- Woodgrove corporate boundary
- Azure IaaS boundary
- Internet boundary
Trust boundary labeling example
Azure IaaS boundary - Boundary box that identifies when data flows from Woodgrove corporate boundary into Azure.
Note
Check out the Create a threat model using data-flow diagram elements module from our Threat Modeling Security Fundamentals learning path for an in-depth review of each element.
Interactions
The next step is to capture the data-flow between each interaction:
User
| Element A | Data-flow | Element B | Crosses boundary | Details |
|---|---|---|---|---|
 User User |
 Bi-directional Bi-directional |
 Microsoft 365 Microsoft 365 |
|
|
 User User |
 Bi-directional Bi-directional |
 Bug management service Bug management service |
|
|
 User User |
 Bi-directional Bi-directional |
 SaaS offerings (grouped) SaaS offerings (grouped) |
|
|
 User User |
 Bi-directional Bi-directional |
 GitHub GitHub |
|
|
 User User |
 Bi-directional Bi-directional |
 Machine Machine |
|
Initial services
| Element A | Data-flow | Element B | Crosses boundary | Details |
|---|---|---|---|---|
 GitHub GitHub |
 Bi-directional Bi-directional |
 Firewall service Firewall service |
|
|
 Machine Machine |
 Bi-directional Bi-directional |
 Firewall service Firewall service |
|
|
 Machine Machine |
 Bi-directional Bi-directional |
 Active Directory service Active Directory service |
|
|
 Machine Machine |
 Bi-directional Bi-directional |
 User User |
See User for details | |
 GitHub GitHub |
 Bi-directional Bi-directional |
 User User |
See User for details | |
 Microsoft 365 Microsoft 365 |
 Bi-directional Bi-directional |
 User User |
See User for details | |
 Bug management service Bug management service |
 Bi-directional Bi-directional |
 User User |
See User for details | |
 SaaS offerings (grouped) SaaS offerings (grouped) |
 Bi-directional Bi-directional |
 User User |
See User for details |
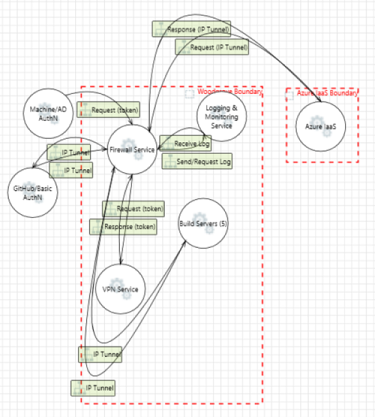
Firewall
| Element A | Data-flow | Element B | Crosses boundary | Details |
|---|---|---|---|---|
 Firewall service Firewall service |
 Bi-directional Bi-directional |
 VPN service VPN service |
|
|
 Firewall service Firewall service |
 Bi-directional Bi-directional |
 Build servers (grouped) Build servers (grouped) |
|
|
 Firewall service Firewall service |
 Bi-directional Bi-directional |
 Logging and monitoring service Logging and monitoring service |
|
|
 Firewall service Firewall service |
 Bi-directional Bi-directional |
 Azure IaaS Azure IaaS |
|
|
 Firewall service Firewall service |
 Bi-directional Bi-directional |
 Machine Machine |
See Initial services for details | |
 Firewall service Firewall service |
 Bi-directional Bi-directional |
 GitHub GitHub |
See Initial services for details |
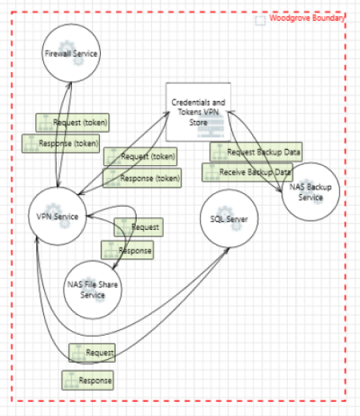
VPN
| Element A | Data-flow | Element B | Crosses boundary | Details |
|---|---|---|---|---|
 VPN service VPN service |
 Bi-directional Bi-directional |
 Firewall service Firewall service |
|
|
 VPN service VPN service |
 Bi-directional Bi-directional |
 Credentials and tokens VPN store Credentials and tokens VPN store |
|
|
 VPN service VPN service |
 Bi-directional Bi-directional |
 NAS file share service NAS file share service |
|
|
 VPN service VPN service |
 Bi-directional Bi-directional |
 SQL server SQL server |
|
|
 Credentials and tokens VPN store Credentials and tokens VPN store |
 Bi-directional Bi-directional |
 NAS backup service NAS backup service |
|
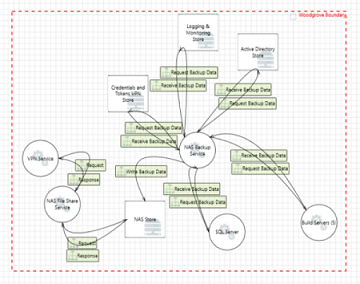
Network attached storage (NAS)
| Element A | Data-flow | Element B | Crosses boundary | Details |
|---|---|---|---|---|
 NAS file share service NAS file share service |
 Bi-directional Bi-directional |
 NAS store NAS store |
|
|
 NAS backup service NAS backup service |
 Bi-directional Bi-directional |
 NAS store NAS store |
|
|
 NAS backup service NAS backup service |
 Bi-directional Bi-directional |
 Active Directory store Active Directory store |
|
|
 NAS backup service NAS backup service |
 Bi-directional Bi-directional |
 Logging and monitoring store Logging and monitoring store |
|
|
 NAS backup service NAS backup service |
 Bi-directional Bi-directional |
 SQL server SQL server |
|
|
 NAS backup service NAS backup service |
 Bi-directional Bi-directional |
 Build servers (grouped) Build servers (grouped) |
|
|
 NAS file share service NAS file share service |
 Bi-directional Bi-directional |
 VPN service VPN service |
See VPN for details | |
 NAS backup service NAS backup service |
 Bi-directional Bi-directional |
 Credentials and tokens VPN store Credentials and tokens VPN store |
See VPN for details |
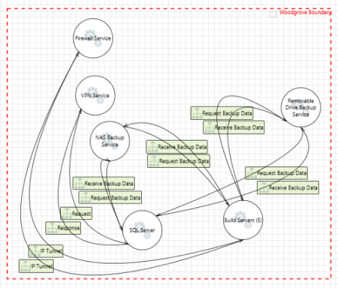
Servers
| Element A | Data-flow | Element B | Crosses boundary | Details |
|---|---|---|---|---|
 SQL server SQL server |
 Bi-directional Bi-directional |
 Removable drive backup service Removable drive backup service |
|
|
 Build servers (grouped) Build servers (grouped) |
 Bi-directional Bi-directional |
 Removable drive backup service Removable drive backup service |
|
|
 SQL server SQL server |
 Bi-directional Bi-directional |
 VPN service VPN service |
See VPN for details | |
 SQL server SQL server |
 Bi-directional Bi-directional |
 NAS backup service NAS backup service |
See NAS for details | |
 Build servers (grouped) Build servers (grouped) |
 Bi-directional Bi-directional |
 NAS backup service NAS backup service |
See NAS for details | |
 Build servers (grouped) Build servers (grouped) |
 Bi-directional Bi-directional |
 Firewall service Firewall service |
See Firewall for details |
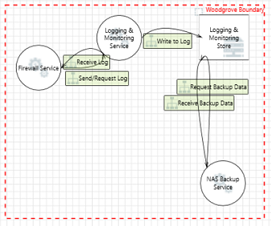
Logging and monitoring
| Element A | Data-flow | Element B | Crosses boundary | Details |
|---|---|---|---|---|
 Logging and monitoring service Logging and monitoring service |
 Bi-directional Bi-directional |
 Logging and monitoring store Logging and monitoring store |
|
|
 Logging and monitoring store Logging and monitoring store |
 Bi-directional Bi-directional |
 NAS backup service NAS backup service |
See NAS for details | |
 Logging and monitoring service Logging and monitoring service |
 Bi-directional Bi-directional |
 Firewall service Firewall service |
See Firewall for details |
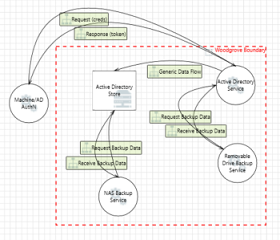
Active Directory
| Element A | Data-flow | Element B | Crosses boundary | Details |
|---|---|---|---|---|
 Active directory store Active directory store |
 Bi-directional Bi-directional |
 Active directory service Active directory service |
|
|
 Active directory service Active directory service |
 Bi-directional Bi-directional |
 Removable drive backup service Removable drive backup service |
|
|
 Active directory service Active directory service |
 Bi-directional Bi-directional |
 Machine Machine |
See Initial services for details | |
 Active directory store Active directory store |
 Bi-directional Bi-directional |
 NAS backup service NAS backup service |
See NAS for details |
Removable drive
| Element A | Data-flow | Element B | Crosses boundary | Details |
|---|---|---|---|---|
 Removable drive backup service Removable drive backup service |
 Bi-directional Bi-directional |
 Removable drive store Removable drive store |
|
|
 Removable drive backup service Removable drive backup service |
 Bi-directional Bi-directional |
 SQL server SQL server |
See Servers for details | |
 Removable drive backup service Removable drive backup service |
 Bi-directional Bi-directional |
 Build servers (grouped) Build servers (grouped) |
See Servers for details | |
 Removable drive backup service Removable drive backup service |
 Bi-directional Bi-directional |
 Active directory service Active directory service |
See Active directory for details |
Azure
| Element A | Data-flow | Element B | Crosses boundary | Details |
|---|---|---|---|---|
 Azure IaaS Azure IaaS |
 Bi-directional Bi-directional |
 Firewall service Firewall service |
|