Exercise - Create a Microsoft Sentinel playbook
As a Security Operations Analyst working for Contoso, you recently notice that a significant number of alerts are generated when someone deletes a virtual machine. You want to analyze such occurrences in the future and reduce the alerts generated for false positive occurrences.
Exercise: Threat response using Microsoft Sentinel playbooks
You decide to implement a Microsoft Sentinel playbook to automate responses to an incident.
In this exercise, you'll explore the Microsoft Sentinel playbooks by performing the following tasks:
Configure Microsoft Sentinel Playbook permissions.
Create a playbook to automate an action to respond to incidents.
Test your playbook by invoking an incident.
Note
You need to have completed the Exercise Setup unit, in order to be able to complete this exercise. If you have not done so, complete it now, and then continue with the exercise steps.
Task 1: Configure Microsoft Sentinel Playbook permissions
In the Azure portal, search for and select Microsoft Sentinel, and select the previously created Microsoft Sentinel workspace.
In the Microsoft Sentinel page, on the menu bar, in the Configuration section, select Settings.
In the Settings page, select the Settings tab and scroll down and expand the Playbook permissions
In Playbook permissions, select the Configure permissions button.
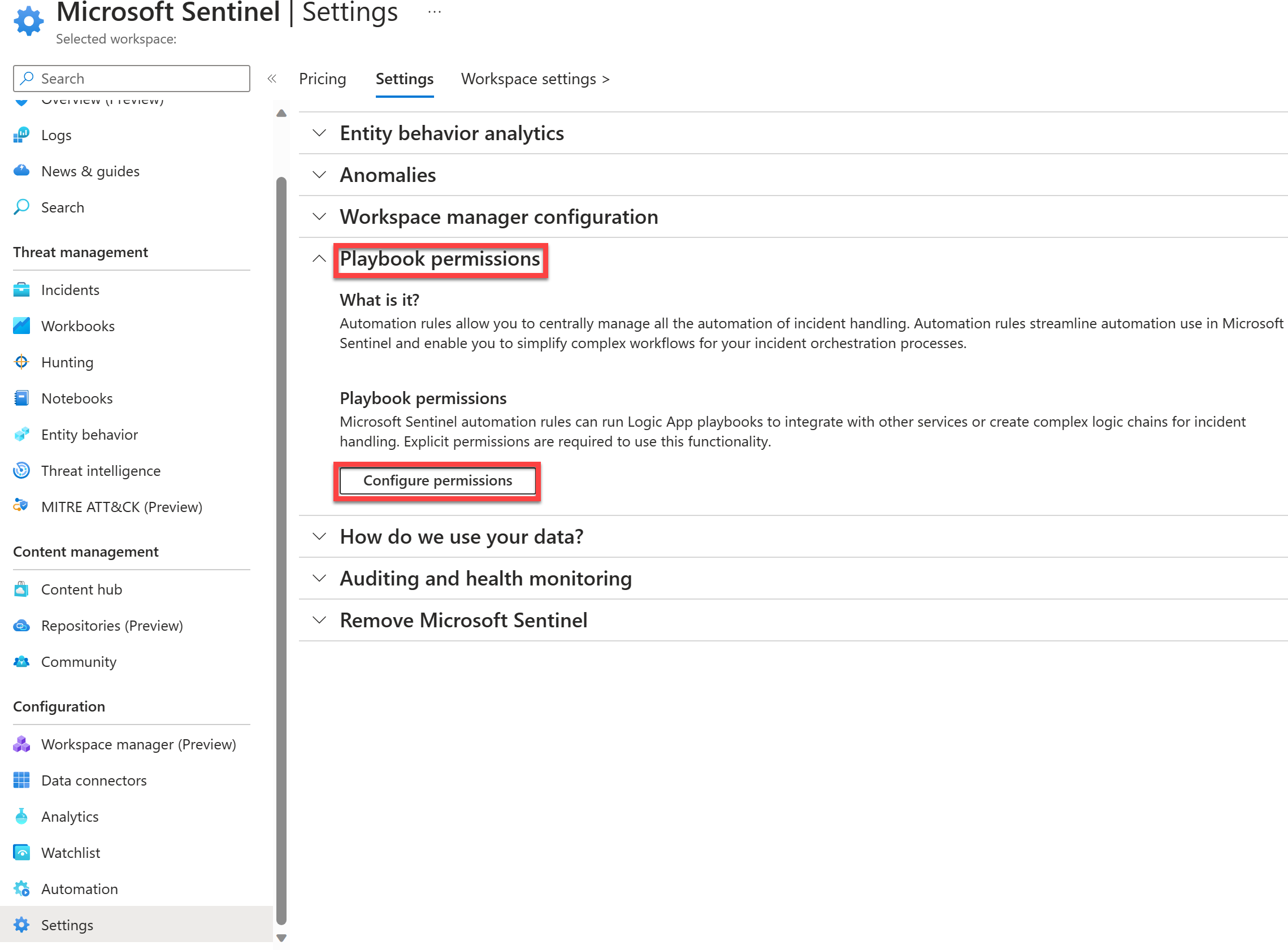
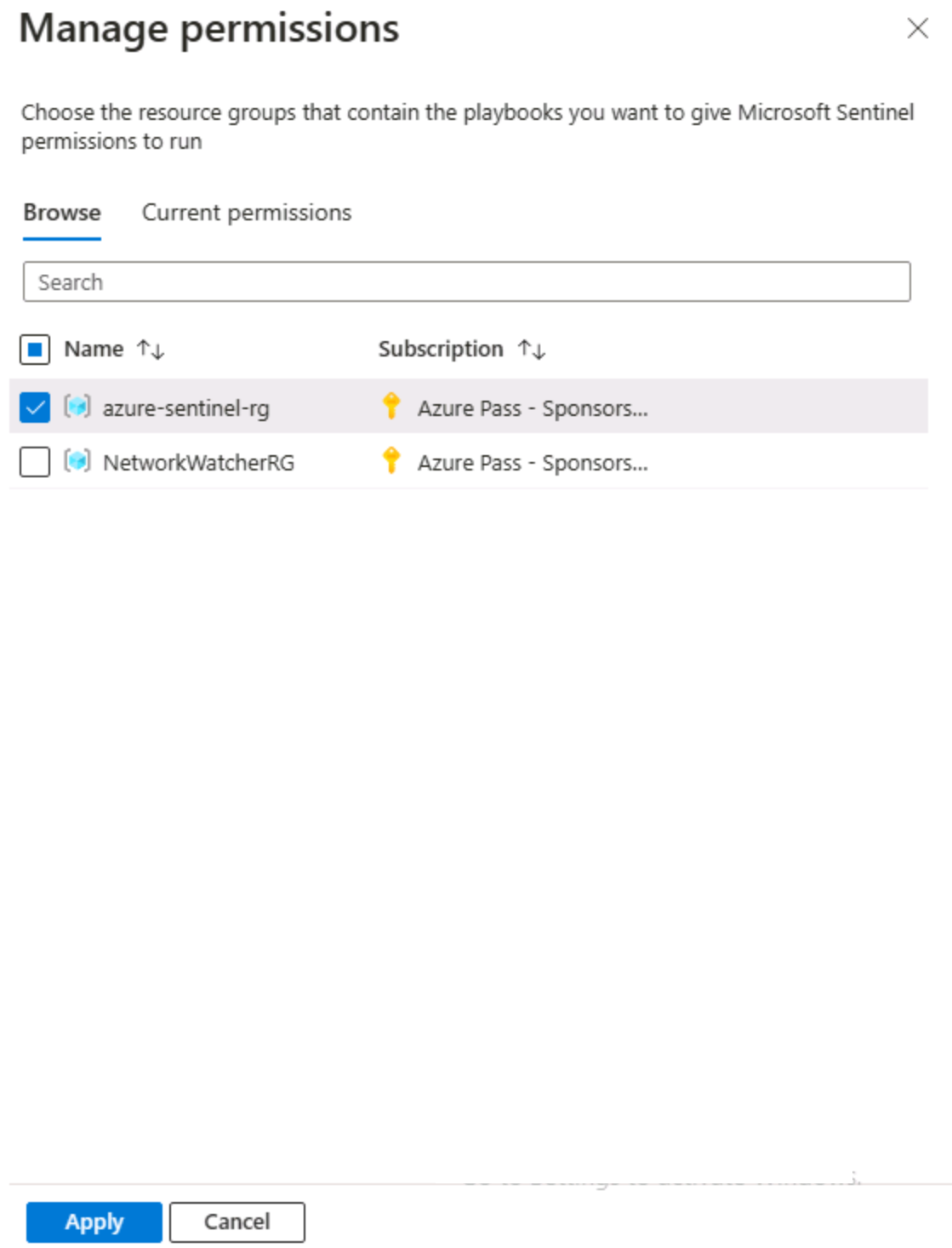
In the Manage permissions page under the Browse tab, select the resource group that your Microsoft Sentinel workspace belongs to. Select Apply.
You should see the Finished adding permissions message.
Task 2: Work with Microsoft Sentinel playbooks
In the Azure portal, search for and select Microsoft Sentinel, and select the previously created Microsoft Sentinel workspace.
In the Microsoft Sentinel page, on the menu bar, in the Configuration section, select Automation.
On the top menu, select Create and Playbook with incident trigger.
In the Create Playbooks page, on the Basics tab, specify the following settings:
Settings Value Subscription Select your Azure subscription. Resource group Select the resource group of your Microsoft Sentinel service. Playbook name ClosingIncident (you can choose any name) Region Select the same location as the location of Microsoft Sentinel. Log Analytics workspace Don't enable diagnostic logs Select Next:Connections >, then select Next: Review and Create >
Select Create and continue to designer
Note
Wait for the deployment to complete. The deployment should take less than 1 minute. If it keeps running you may need to refresh the page.
In the Logic Apps Designer pane, you should see the Microsoft Sentinel incident (preview) displayed.

On the Microsoft Sentinel incident (preview) page, select the Change connection link.
On the Connections page, select Add new.
On the Microsoft Sentinel page, select Sign in.
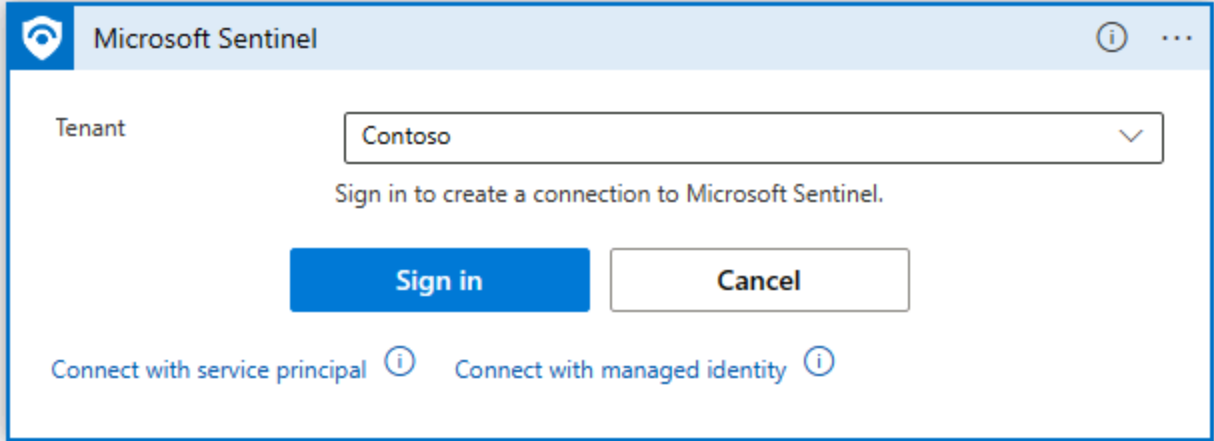
On the Sign in to your account page, provide the credentials for your Azure subscription.
Back on the Microsoft Sentinel incident (preview) page, you should see you're connected to your account. Select + New step.
In the Choose an operation window, in the search field, type Microsoft Sentinel.
Select the Microsoft Sentinel Icon.
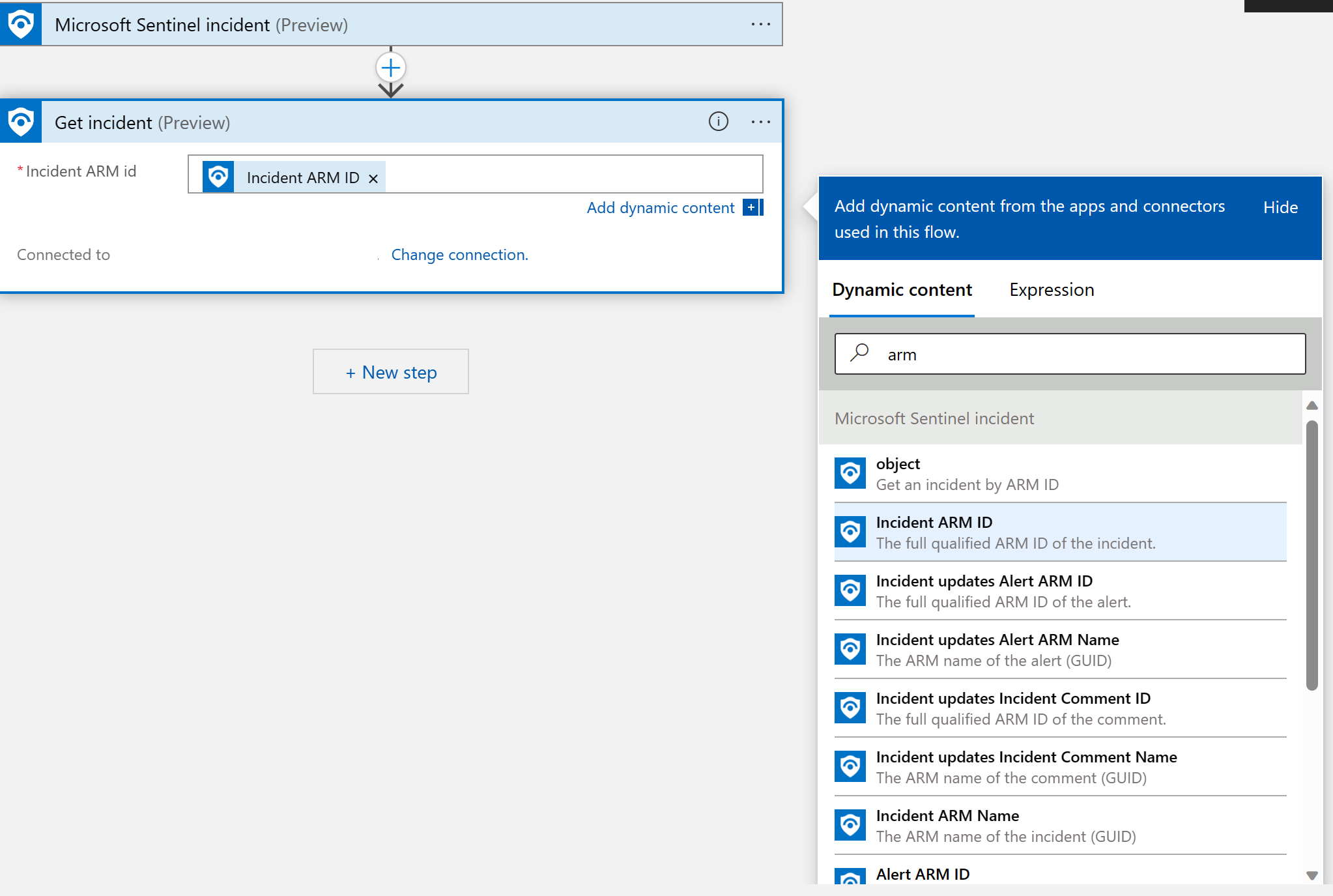
On the Actions tab, locate and select Get incident (Preview).
In the Get Incident (Preview) window, select the Incident ARM ID field. The Add dynamic content window opens.
Tip
When you select a field, a new window opens to help you fill these fields with dynamic content.
On the Dynamic content tab, in the search box, you can start entering Incident ARM, and then select the entry from the list, as the following screenshot displays.
Select + New step.
In the Choose an operation window, in the search field, type Microsoft Sentinel.
Tip
In the For you tab, Recent selections should display the Microsoft Sentinel Icon.
Select the Microsoft Sentinel Icon.
From the Actions tab, locate and select Update incident (Preview).
In the Update incident (Preview) window, provide the following inputs:
Settings Values Specify Incident ARM id Incident ARM ID Specify Owner Object Id / UPN Incident Owner Object ID Specify Assign/Unassign owner From the drop-down menu, select Unassign Severity You can leave the default Incident severity Specify Status From the drop-down menu, select Closed. Specify Classification reason From the drop-down menu, select an entry like Undetermined, or select Enter custom value, and select IncidentClassification Dynamic content. Close reason text Write descriptive text. 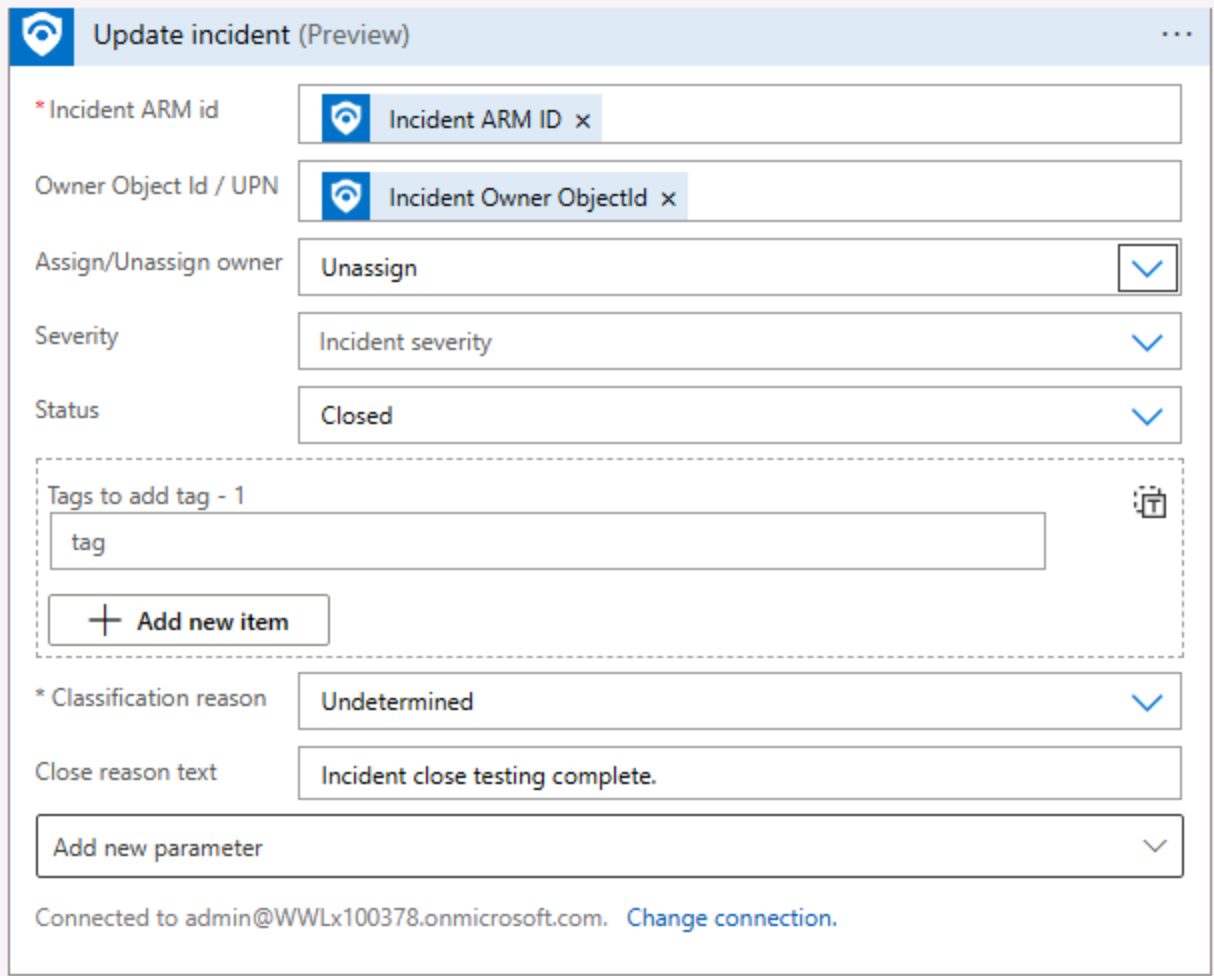
Select the Incident ARM ID field. The Add dynamic content window opens, in the search box, you can start entering Incident ARM. Select Incident ARM ID and then select the Owner Object Id / UPN field.
The Add dynamic content window opens, in the search box, you can start entering Incident owner. Select Incident Owner Object ID and then fill in the remaining fields using the table entries.
When done, choose Save from the Logic Apps Designer menu bar, and then close the Logic Apps Designer.
Task 3: Invoke an incident and review the associated actions
In the Azure portal, in the Search resources, services, and docs text box, type virtual machines, and then select Enter.
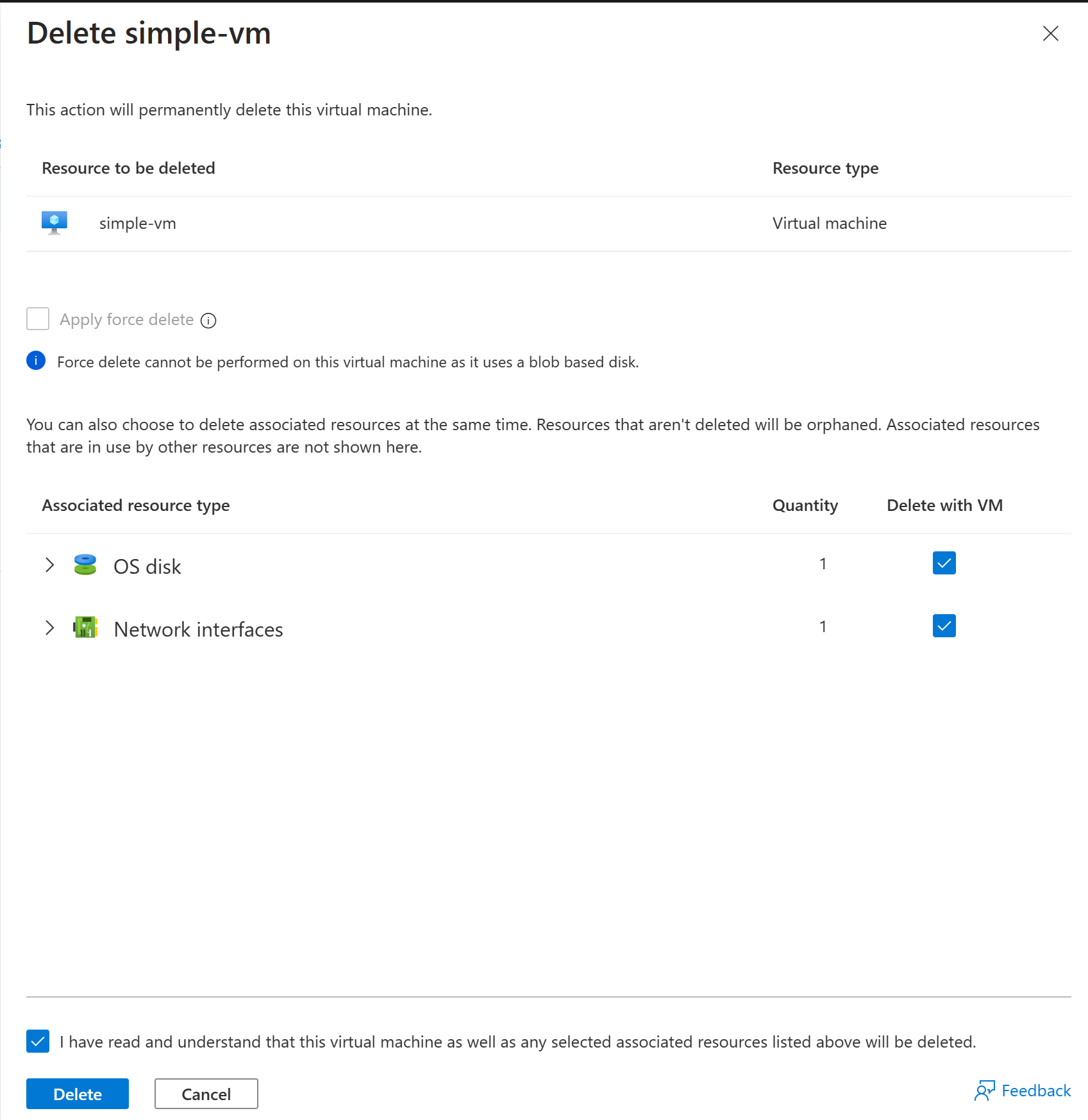
On the Virtual machines page, locate and select the simple-vm virtual machine, and then on the header bar, select Delete.
On the Delete simple-vm page, select Delete with VM for both the OS Disk and the Network Interface.
Select the box to acknowledge I have read and understand that this virtual machine as well as any selected resources will be deleted, then select Delete to delete the virtual machine.
Note
This task creates an incident based on the analytics rule that you created earlier in the exercise setup unit. Incident creation can take up to 15 minutes. Wait for it to complete before proceeding to the next step.
Task 4: Assign the playbook to an existing incident
In the Azure portal, search for and select Microsoft Sentinel, and then select the previously created Microsoft Sentinel workspace.
On the Microsoft Sentinel | Overview page, on the menu bar, in the Threat management section, select Incidents.
Note
As mentioned in the previous note, Incident creation can take up to 15 minutes. Refresh the page until incident appears in the Incidents page.
On the Microsoft Sentinel | Incidents page, select an incident that has been created based on the deletion of the virtual machine.
In the details pane, select Actions and Run playbook (Preview).
On the Run playbook on incident page, in the Playbooks tab, you should see the ClosingIncident playbook, select Run.
Verify that you receive the message Playbook was triggered successfully.
Close the Run playbook on incident page, to return to the Microsoft Sentinel | Incidents page.
In the Microsoft Sentinel | Incidents page, on the header bar, select Refresh. You'll notice that the incident disappears from the pane. On the Status menu, select Closed, and then select OK.
Note
It could take up to 5 minute for Alerts to be shown as Closed
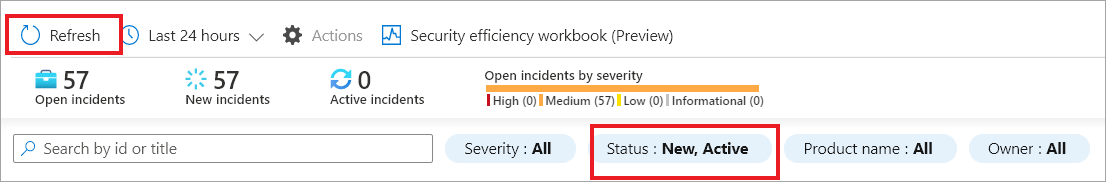
Verify that the incident displays again and notice the Status column to check that it's Closed.
Clean up the resources
In the Azure portal, search for Resource groups.
Select azure-sentinel-rg.
On the header bar, select Delete resource group.
In the TYPE THE RESOURCE GROUP NAME: field, enter the name of the resource group azure-sentinel-rg and select Delete.
