Tutorial: Configure Playvox for automatic user provisioning
This tutorial describes the steps to follow in both Playvox and Microsoft Entra ID to configure automatic user provisioning. When configured, Microsoft Entra ID automatically provisions and de-provisions users or groups to Playvox by using the Microsoft Entra provisioning service. For important details on what this service does and how it works, and for frequently asked questions, see Automate user provisioning and deprovisioning to SaaS applications with Microsoft Entra ID.
Capabilities supported
- Create users in Playvox.
- Remove users in Playvox when they don't need access anymore.
- Keep user attributes synchronized between Microsoft Entra ID and Playvox.
Prerequisites
The scenario in this tutorial assumes that you already have the following prerequisites:
- A Microsoft Entra tenant.
- One of the following roles: Application Administrator, Cloud Application Administrator, or Application Owner.
- A user account in Playvox with Super Admin permissions.
Step 1: Plan your provisioning deployment
Determine who will be in scope for provisioning.
Determine what data to map between Microsoft Entra ID and Playvox.
Step 2: Configure Playvox to support provisioning by using Microsoft Entra ID
Log in to the Playvox admin console and go to Settings > API Keys.
Select Create API Key.
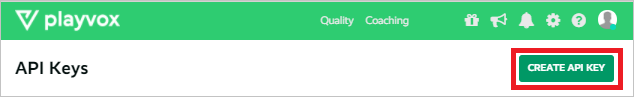
Enter a meaningful name for the API key, and then select Save. After the API key is generated, select Close.
On the API key that you created, select the Details icon.
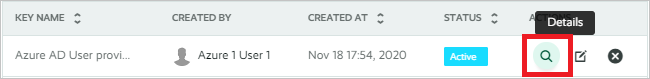
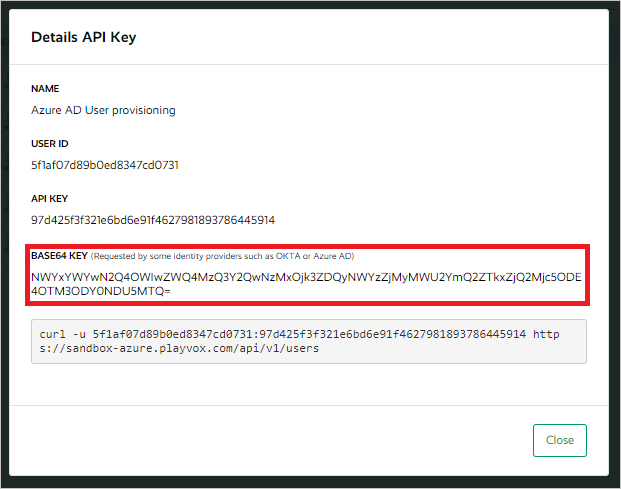
Copy and save the BASE64 KEY value. Later, in the Azure portal, you'll enter this value in the Secret Token text box in the Provisioning tab of your Playvox application.
Step 3: Add Playvox from the Microsoft Entra application gallery
To start to manage provisioning to Playvox, add Playvox to your Microsoft Entra tenant from the application gallery. To learn more, see Quickstart: Add an application to your Microsoft Entra tenant.
If you've previously set up Playvox for single sign-on (SSO), you can use the same application. However, we recommend that you create a separate app when testing the integration initially.
Step 4: Define who will be in scope for provisioning
You use the Microsoft Entra provisioning service to scope who will be provisioned, based either on assignment to the application or on attributes of the user or group. To scope who will be provisioned to your app based on assignment, see Manage user assignment for an app in Microsoft Entra ID to learn how to assign users or groups to the application. To scope who will be provisioned based solely on attributes of the user or group, use a scoping filter as described in Attribute-based application provisioning with scoping filters.
Remember these points:
When assigning users to Playvox, you must select a role other than Default Access. Users with the Default Access role are excluded from provisioning and will be marked as not effectively entitled in the provisioning logs. If Default Access is the only role available on the application, you can update the application manifest to add other roles.
Start small. Test with a small set of users or groups before rolling out to everyone. When provisioning scope is based on assigned users or groups, you can control the size of the set by assigning only one or two users or groups to the app. When provisioning scope includes all users and groups, you can specify an attribute-based scoping filter to limit the size of your test set.
Step 5: Configure automatic user provisioning to Playvox
This section guides you through the steps to configure the Microsoft Entra provisioning service to create, update, and disable users or groups, based on user or group assignments in Microsoft Entra ID.
To configure automatic user provisioning for Playvox in Microsoft Entra ID:
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications.
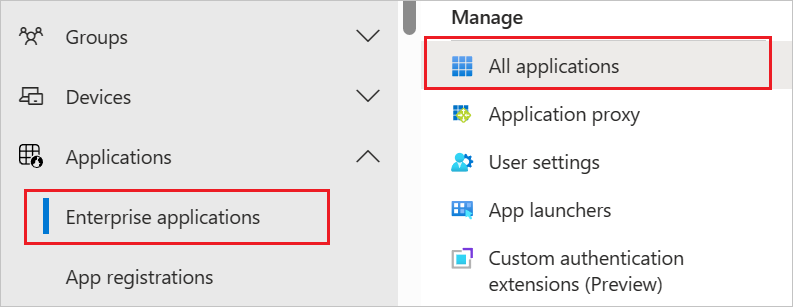
In the applications list, search for and select Playvox.
Select the Provisioning tab.
Set the Provisioning Mode to Automatic.

In the Admin Credentials section, enter your Playvox Tenant URL as:
https://{tenant}.playvox.com/scim/v1Enter the Secret Token that you copied earlier in Step 2. Then, select Test Connection to ensure that Microsoft Entra ID can connect to Playvox. If the connection fails, make sure your Playvox account has Admin permissions and try again.

In the Notification Email text box, enter the email address of a person or group who will receive the provisioning error notifications. Then, select the Send an email notification when a failure occurs check box.
Select Save.
In the Mappings section, select Synchronize Microsoft Entra users to Playvox.
Review the user attributes that are synchronized from Microsoft Entra ID to Playvox in the Attribute-Mapping section. The attributes selected as Matching properties are used to match the user accounts in Playvox for update operations. If you choose to change the matching target attribute, make sure that the Playvox API supports filtering users based on that attribute. Select Save to commit any changes.
Attribute Type Supported for filtering userName String ✓ active Boolean displayName String emails[type eq "work"].value String name.givenName String name.familyName String name.formatted String externalId String To configure scoping filters, see the instructions in the Scoping filter tutorial.
To enable the Microsoft Entra provisioning service for Playvox, change the Provisioning Status to On in the Settings section.

Still in Settings, define the users or groups to provision to Playvox by choosing the values you want in Scope.
When you're ready to provision, select Save.

This operation starts the initial synchronization cycle of all users and groups defined in Scope in the Settings section. The initial cycle takes longer than later cycles. Later cycles occur approximately every 40 minutes, provided that the Microsoft Entra provisioning service is running.
Step 6: Monitor your deployment
After you've configured provisioning, use the following resources to monitor your deployment:
- Use the provisioning logs to determine which users have been provisioned successfully or unsuccessfully.
- Check the progress bar to see the status of the provisioning cycle and how close it is to completion.
- If the provisioning configuration seems to be in an unhealthy state, the application will go into quarantine. To learn more about quarantine states, see Application provisioning in quarantine status.
Additional resources
- Managing user account provisioning for enterprise apps
- What is application access and single sign-on with Microsoft Entra ID?
Next steps
Tilbakemeldinger
Kommer snart: Gjennom 2024 faser vi ut GitHub Issues som tilbakemeldingsmekanisme for innhold, og erstatter det med et nytt system for tilbakemeldinger. Hvis du vil ha mer informasjon, kan du se: https://aka.ms/ContentUserFeedback.
Send inn og vis tilbakemelding for