教學課程:探索和管理影子 IT
如果詢問 IT 系統管理員他們認為員工使用多少雲端應用程式,通常會回答 30 或 40 個,而實際上組織的員工平均使用超過 1,000 個不同應用程式。 影子IT可協助您瞭解並識別正在使用哪些應用程式,以及風險層級為何。80% 的員工使用未經核准的應用程式,且可能不符合您的安全性和合規性政策。 而且,由於您的員工可以從公司網路外部存取您的資源和應用程式,因此您防火牆上的規則和原則已不再足夠。
在本教學課程中,您將瞭解如何使用 Cloud Discovery 來探索正在使用的應用程式、探索這些應用程式的風險、設定原則以識別正在使用的新有風險應用程式,以及取消批准這些應用程式,以使用 Proxy 或防火牆設備原生封鎖這些應用程式
提示
根據預設,適用於雲端的 Defender 應用程式無法探索不在目錄中的應用程式。
如何在您的網路中探索和管理影子 IT
使用此程序可在您的組織中推出影子 IT Cloud Discovery。
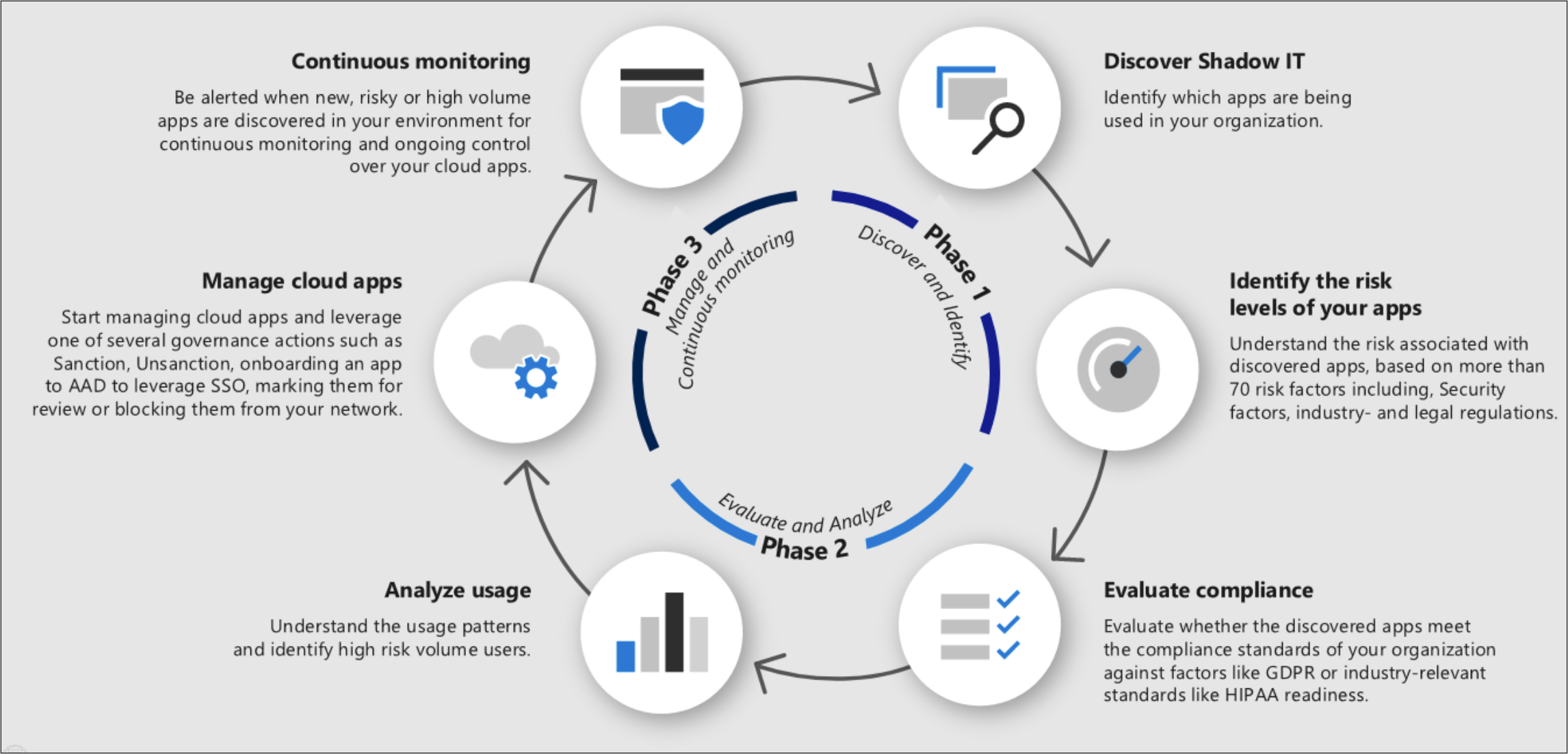
階段 1:探索和識別影子 IT
探索影子 IT:藉由在組織中執行 Cloud Discovery 來識別組織的安全性狀態,以查看網路中實際發生的情況。 如需詳細資訊,請參閱 設定雲端探索。 這可以使用下列任一方法來完成:
藉由與 適用於端點的 Microsoft Defender 整合,快速啟動並執行 Cloud Discovery。 此原生整合可讓您立即開始收集跨 Windows 10 和 Windows 11 裝置、在網路上和關閉雲端流量的數據。
若要涵蓋連線到您網路的所有裝置,請務必在防火牆和其他 Proxy 上部署 適用於雲端的 Defender Apps 記錄收集器,以從端點收集數據,並將其傳送至 適用於雲端的 Defender Apps 進行分析。
將 適用於雲端的 Defender Apps 與您的 Proxy 整合。 適用於雲端的 Defender Apps 原生整合一些第三方 Proxy,包括Zscaler。
由於原則因不同使用者群組、區域和業務群組而異,建議您為每個單位建立專用的影子 IT 報告。 如需詳細資訊,請參閱 建立自定義連續報告。
現在 Cloud Discovery 已在您的網路上執行,請查看產生的連續報告,並查看 Cloud Discovery 儀表板以了解正在組織中使用之應用程式的完整情況。 依類別來查看它們是個好主意,因為您通常會發現未獲批准的應用程式正用於未由獲批准的應用程式解決的合法工作相關用途。
識別應用程式的風險層級:使用 適用於雲端的 Defender Apps 目錄深入瞭解與每個探索到的應用程式相關的風險。 適用於雲端的 Defender 應用程式類別目錄包含超過 31,000 個使用 90 個風險因素進行評估的應用程式。 從應用程式的相關一般資訊 (應用程式總部位置、發行者身分),到安全性措施和控制 (待用加密的支援、提供使用者活動的稽核記錄),皆在風險因素涵蓋範圍內。 如需詳細資訊,請參閱使用風險分數,
在 Microsoft Defender 入口網站的 [Cloud Apps] 底下,選取 [Cloud Discovery]。 然後移至 [ 探索到的應用程式 ] 索引標籤。依您關心的風險因素篩選組織中探索到的應用程式清單。 例如,您可以使用 進階篩選 來尋找風險分數低於 8 的所有應用程式。
您可以選取應用程式名稱,然後選取 [資訊 ] 索引標籤,以查看應用程式安全性風險因素的詳細數據,以深入瞭解其合規性。
階段 2:評估和分析
評估合規性:檢查應用程式是否符合組織的標準,例如 HIPAA 或 SOC2。
在 Microsoft Defender 入口網站的 [Cloud Apps] 底下,選取 [Cloud Discovery]。 然後移至 [ 探索到的應用程式 ] 索引標籤。依您關心的合規性風險因素篩選組織中探索到的應用程式清單。 例如,使用建議的查詢篩掉不符合規範的應用程式。
您可以選取應用程式名稱,然後選取 [資訊 ] 索引標籤,以查看應用程式合規性風險因素的詳細數據,以深入瞭解其合規性。
分析使用量:現在您知道是否要讓應用程式在組織中使用,您想要調查其使用方式和人員。 如果只是有限度地在組織中使用應用程式,也許沒有問題,但是如果使用量持續增加,您可能希望收到其相關通知,以便決定是否要封鎖該應用程式。
在 Microsoft Defender 入口網站的 [Cloud Apps] 底下,選取 [Cloud Discovery]。 然後移至 [ 探索到的應用程式 ] 索引標籤,然後選取您想要調查的特定應用程式,向下切入。 [使用量] 索引標籤可讓您知道有多少使用中使用者正在使用應用程式,以及其產生的流量。 這已經可讓您瞭解應用程式發生的情況。 然後,如果您想要查看誰,特別是使用應用程式,您可以選取 [ 作用中用戶總數] 來進一步向下切入。 這個重要步驟可以為您提供相關資訊,例如,如果您發現特定應用程式的所有使用者都來自行銷部門,則可能該應用程式為業務所需,而如果存在風險,應在封鎖該應用程式前,告知使用者替代方案。
調查探索到使用探索到的應用程式時,更深入地探討。 檢視子域和資源,以了解雲端服務中的特定活動、數據存取和資源使用量。 如需詳細資訊,請參閱 深入探討探索到的應用程式 和 探索資源和自定義應用程式。
識別替代應用程式:使用雲端應用程式目錄來識別更安全的應用程式,這些應用程式可達到與偵測到的風險應用程式類似的商務功能,但確實符合貴組織的原則。 您可以使用進階篩選來尋找與您不同安全性控制項相符合之相同類別中的應用程式,以達成此動作。
階段3:管理您的應用程式
管理雲端應用程式:適用於雲端的 Defender Apps 可協助您管理組織中應用程式使用的程式。 在您識別出組織中使用的不同模式和行為後,您可以建立新的自訂應用程式標籤,以根據其業務狀態或理由來分類每個應用程式。 然後您可以將這些標籤用於特定的監視用途,例如,找出流向標記為具風險雲端儲存體應用程式之應用程式的高流量。 您可以在 設定> Cloud Apps>Cloud Discovery>應用程式標籤管理應用程式標籤。 然後之後可在 Cloud Discovery 頁面中使用這些標籤來篩選,以及用來建立原則。
使用 Microsoft Entra 資源庫管理探索到的應用程式:適用於雲端的 Defender 應用程式也會使用其原生整合 Microsoft Entra ID,讓您能夠管理 Microsoft Entra Gallery 中探索到的應用程式。 對於已出現在 Microsoft Entra Gallery 中的應用程式,您可以套用單一登錄,並使用 Microsoft Entra ID 管理應用程式。 若要這樣做,請在相關應用程式出現的數據列上,選擇數據列結尾的三個點,然後選擇 [ 使用 Microsoft Entra ID 管理應用程式]。
持續監視:既然您已徹底調查應用程式,您可能想要設定原則來監視應用程式,並在需要時提供控制權。
現在就來建立原則,以便在發生您擔心的情況時,自動發出警示。 例如,您可能想要建立 應用程式探索原則 ,讓您知道當您所關注的應用程式下載或流量激增時。 若要達成此目的,您應該在探索到的用戶原則、雲端記憶體應用程式合規性檢查和新的具風險應用程式中啟用異常行為。 您也應該設定原則,以透過電子郵件通知您。 如需詳細資訊,請參閱 原則範本參考、更多關於 Cloud Discovery原則 和設定 應用程式探索原則的詳細資訊。
查看警示頁面,並使用 [原則類型] 篩選來查看應用程式探索警示。 針對應用程式探索原則所比對的應用程式,建議您進行進階調查,以深入瞭解使用應用程式的商業理由,例如連絡應用程式的使用者。 然後,重複階段 2 中的步驟來評估應用程式風險。 接著,為應用程式決定後續步驟,可以是核准以後可使用該應用程式,或要在使用者下次存取該應用程式時將其禁止,若是後者,您應該將其標記為未獲批准,來禁止其使用您的防火牆、Proxy 或安全 Web 閘道。 如需詳細資訊,請參閱整合 適用於端點的 Microsoft Defender、與 Zscaler 整合、與 iboss 整合,以及導出區塊腳本來封鎖應用程式。
階段 4:進階陰影 IT 探索報告
除了 適用於雲端的 Defender Apps 中可用的報告選項之外,您還可以將 Cloud Discovery 記錄整合到 Microsoft Sentinel 中,以進行進一步的調查和分析。 數據在 Microsoft Sentinel 中之後,您可以在儀錶板中檢視數據、使用 Kusto 查詢語言執行查詢、將查詢導出至 Microsoft Power BI、與其他來源整合,以及建立自定義警示。 如需詳細資訊,請參閱 Microsoft Sentinel 整合。
階段5:控制獲批准的應用程式
若要透過 API 啟用應用程控,請 透過 API 連線應用程式以進行持續監視。
使用條件式存取應用程式控制來保護應用程式。
雲端應用程式的性質表示它們每天都會更新,而新的應用程式一直都會出現。 因此,員工會持續使用新的應用程式,請務必持續追蹤並檢閱與更新您的原則,檢查您的使用者正在使用哪些應用程式,以及其使用方式與行為模式。 您隨時可以前往 Cloud Discovery 儀表板查看哪些新的應用程式正有人使用,並再次遵循本文指示確保您的組織與資料受到保護。
下一步
如果您遇到任何問題,我們會在這裡提供説明。 若要取得產品問題的協助或支援,請 開啟支援票證。
