Centralized security operations with external identities for defense organizations
This article is for multitenant defense organizations with a centralized security operations team. It explains how you can manage multiple tenants and meet zero trust requirements with a single identity and privileged access device. With this configuration, security operators don't need multiple user accounts, credentials, and workstations to secure your environment. The setup supports zero trust capabilities in secondary tenants.
Understand configuration components
This scenario combines Azure Lighthouse, Entra External ID, Entra Privileged Identity Management, and multitenant management in Microsoft Defender XDR.
Use Azure Lighthouse to manage Microsoft Sentinel in secondary tenants. You need to use Azure Lighthouse to manage Microsoft Sentinel workspaces in subscriptions attached to secondary tenants. Azure Lighthouse enables multitenant management with scalability, higher automation, and enhanced governance across resources.
Azure Lighthouse allows a security principal (user, group, or service principal) in one tenant have an Azure role to manage resources in a different tenant. With this setup, security operators in a primary tenant can seamlessly manage both Sentinel and Defender for Cloud across tenants.
Note
Permissions for Microsoft Sentinel workspaces attached to secondary tenants can be assigned to users local to the secondary tenant, B2B guest users from the primary tenant, or directly to primary tenant users using Azure Lighthouse. Azure Lighthouse is the recommended option for Sentinel because it let's you extend cross-workspace activities across tenant boundaries.
Use Entra External ID to manage Microsoft Defender for Endpoint in secondary tenants. You can't use Azure Lighthouse to share Microsoft Defender for Endpoint (MDE) between tenants, so you need to use external identities (B2B guests). External identities let security operators in the primary tenant manage MDE in a secondary tenant without signing in with a different account or credential. The security operator needs to specify the tenant they're using. They should include the tenant ID in the Microsoft Defender portal URL to specify the tenant. Your operators should bookmark the Microsoft Defender portals for each tenant they need to manage. To complete the setup, you need to configure cross-tenant access settings in the secondary tenant. Set the inbound trust settings to trust multifactor authentication (MFA) and device compliance from the primary tenant. This configuration lets the guest users manage MDE without creating exceptions for existing conditional access policies for secondary tenants.
When you enable Defender for Server in a subscription linked to the secondary tenant, the MDE extension automatically deploys and begins providing security signals to the MDE service. It uses the same secondary tenant. MDE permissions can't use Azure Lighthouse. You must assign them to users or groups in the local (secondary) Microsoft Entra ID. You need to onboard security operators as external identities (B2B guests) in the secondary tenant. Then you can add the guest to an MDE role using a Microsoft Entra security group. With this configuration, a primary tenant security operator can take response actions on servers protected by MDE in the secondary tenant.
Use Privileged Identity Management. Microsoft Entra Privileged Identity Management (PIM) enables just-in-time role elevation for Azure and Microsoft Entra roles. PIM for Groups extends this functionality to group membership for Microsoft 365 groups and Microsoft Entra security groups. Once you set up PIM for Groups, you need to review active and eligible membership of the privileged group by creating an access review of PIM for Groups.
Important
There are two ways to use Entra Privileged Identity Management with Azure Lighthouse. You can use PIM for groups to elevate membership to an Entra security group with a permanent authorization configured in Azure Lighthouse as described in the previous section. Another option is to configure Azure Lighthouse with eligible authorizations. For more information, see onboard a customer to Azure Lighthouse.
Configure centralized security operations
To set up centralized security operations for a multitenant environment, you must configure Azure Lighthouse, Entra External ID, and Entra Privileged Identity Management. A security operator in the primary tenant can use a single identity secure multiple tenants. They sign in once, elevate their access with PIM, monitor resources across tenants and services, and respond to threats across tenants (see figure 1).
 Figure 1. How to set up security operations in multitenant defense organizations.
Figure 1. How to set up security operations in multitenant defense organizations.
1. Deploy Sentinel and enable Defender for Cloud. Create a Microsoft Sentinel workspace in subscriptions associated with each tenant. Configure relevant data connectors and enable analytics rules. Enable Defender for Cloud enhanced workload protections for hosted workloads, including Defender for Server, in all Azure environments, and connect Defender for Cloud to Microsoft Sentinel.
2. Configure PIM for Azure security operations. Create a role-assignable group (Azure SecOps in Figure 1) and permanently assign the group to Azure roles the security operators need. The example uses Microsoft Sentinel Contributor and Security Reader, but you might also consider Logic App Contributor and other roles they need. Configure PIM for Groups to assign Security Operators as eligible for the Azure SecOps group. This approach lets the Security Operator elevate access for all the roles they need in one PIM request. Configure permanent role assignments for read access if necessary.
3. Configure PIM for Microsoft Defender XDR security operations. Create a role-assignable group (Microsoft 365 Role Group in Figure 1) for assigning Microsoft Defender XDR permissions. Next create a PIM role for Microsoft 365 Role Group and assign eligibility for the Security Operator. If you don't want to manage multiple roles, you can use the same group (Azure SecOps) you configured in step 1 to assign Microsoft Defender XDR permissions and Azure roles.
4. Configure Azure Lighthouse. Use Azure Lighthouse to assign Azure roles for Secondary tenant Azure resource subscriptions. Use the object ID of the Azure SecOps group and the tenant ID of the primary tenant. The example in Figure 1 uses Microsoft Sentinel Responder and Security Reader roles. Configure permanent role assignments using Azure Lighthouse to provide permanent read access if needed.
5. Configure external user access in the secondary tenant. Use entitlement management to configure end user-initiated scenario or use a guest invitation to bring primary tenant security operators as external identities in the secondary tenant. Configure cross-tenant access settings in the secondary tenant are configured to trust MFA and device compliance claims from the primary tenant. Create a role-assignable group (Microsoft 365 Role Group in Figure 1), assign Microsoft Defender for Endpoint permissions, and configure a PIM role following the same process as step 2.
Manage centralized security operations
Security operators need accounts and eligible access to secure the environment and respond to threats. Security operators should know which roles they're eligible for and how to elevate their permissions using Microsoft Entra PIM. For Microsoft Defender for Endpoint (MDE), they must know how to switch between tenants to hunt and respond to threats using MDE.
Security operators use the multitenant security operations setup (see figure 1) to secure multiple tenants. They can monitor, investigate, and respond to threats across Microsoft 365 and Azure across Microsoft Entra tenants (see figure 2).
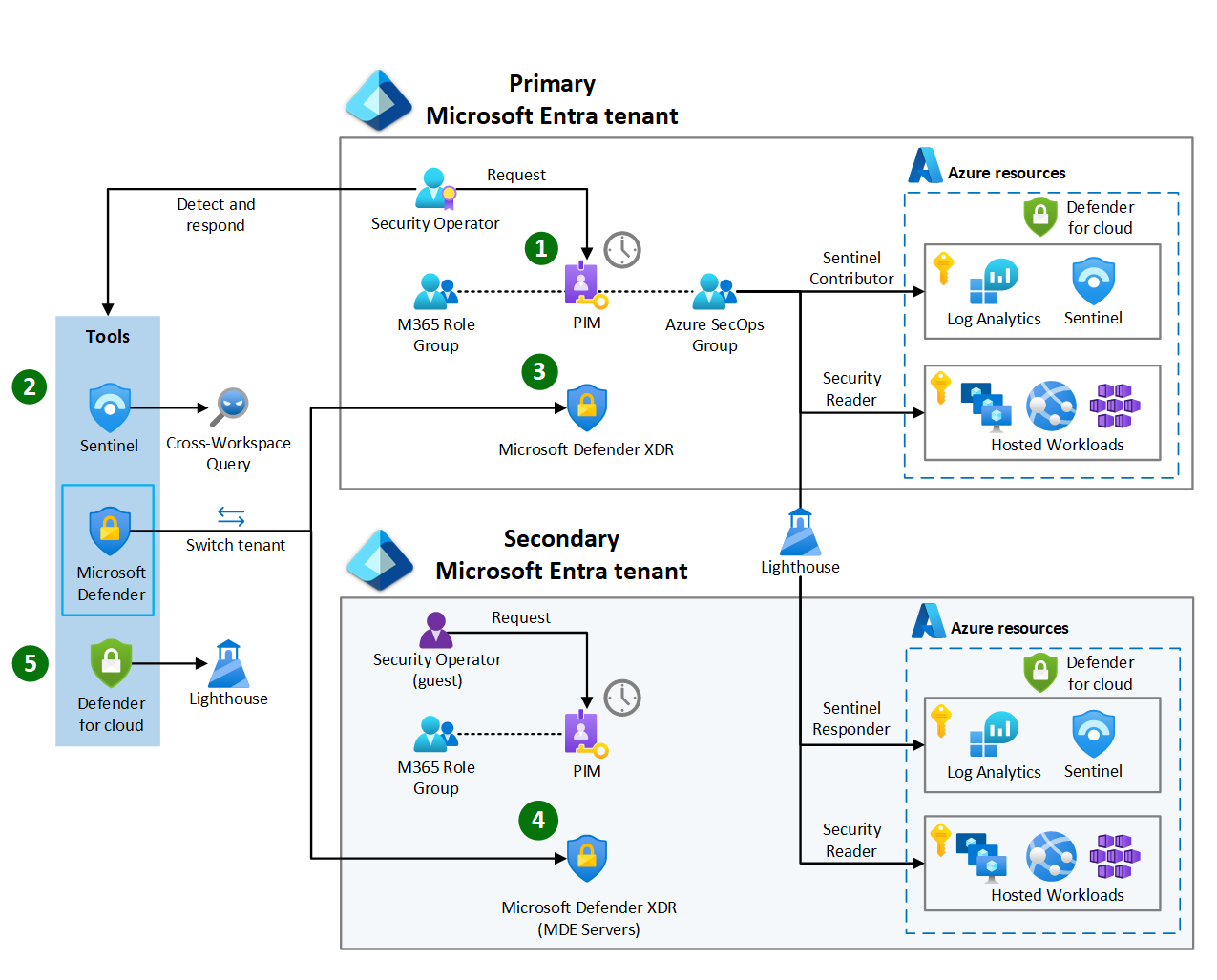 Figure 2. How to use a multitenant security operations setup.
Figure 2. How to use a multitenant security operations setup.
1. Request Sentinel and Defender for cloud access. The security operator needs to sign into the Azure portal to request and activate the Azure SecOps role using PIM. Once their role is active, they can access Microsoft Sentinel and Defender for Cloud.
2. Use Sentinel across workspaces and tenants. When their Azure SecOps role is active, the security operator can navigate to Microsoft Sentinel and perform operations across tenants. You configure Microsoft Defender XDR and Defender for Cloud data connectors for the Sentinel instances in the primary tenant and secondary tenant. When you configure Azure Lighthouse for the Azure SecOps role, the security operator can see all Sentinel alerts, query across workspaces, and manage incidents and investigations across all tenants.
3. Use the Microsoft Defender portal in the primary tenant to respond to workstation threats. When the security operator needs access to Microsoft Defender XDR, they use Microsoft Entra PIM to activate their Microsoft 365 Role. This group membership assigns permissions needed to respond to the security threats on workstation devices managed by Intune and onboarded to MDE in the primary tenant. The security operator uses the Microsoft Defender portal to take a response action and isolate a workstation.
4. Use the Microsoft Defender portal in the secondary tenant to respond to server threats. When security operators need to respond to threats detected by MDE for servers in secondary tenant subscriptions, they need to use Microsoft Defender for the secondary tenant. Multitenant management in Microsoft Defender XDR simplifies this process and can present a combined view of Microsoft Defender XDR across all tenants. The operator needs to elevate their MDE access in the secondary tenant before they can initiate a response action. The security operator must sign in to either the Azure or Entra portals and switch to the secondary tenant directory. Next, the security operator must use PIM to activate the Microsoft 365 Role Group. Once the role is active, the operator can navigate to the Microsoft Defender portal. From here, the security operator can initiate a live response to collect logs from the server or perform other MDE response actions.
5. Use Lighthouse to manage Defender for Cloud across tenants. The security operator should check Defender for Cloud recommendations. The operator needs to use the Azure portal to switch directories back to the primary tenant. Azure Lighthouse enables the security operator to find secondary tenant Azure resources from the primary tenant. Defender for Cloud might show several recommendations. These recommendations might be enabling just-in-time virtual machine access and the management ports accessible via the internet. In this scenario, the security operator doesn't have the Azure role to implement Defender for Cloud recommendations. The security operator must contact the secondary tenant infrastructure management team to remediate the vulnerability. The security operator must also assign Azure Policy to prevent deploying virtual machines with exposed management ports.
Other security operations patterns
The management pattern presented in this article is one of many patterns possible using a combination of external identities and Azure Lighthouse. Your organization might decide to implement a different pattern that better meets the needs of your security operators.
Related links
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for