Ask Learn
PreviewPlease sign in to use this experience.
Sign inThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Password hash synchronization is one of the sign-in methods used to accomplish hybrid identity. Microsoft Entra Connect synchronizes a hash, of the hash, of a user's password from an on-premises Active Directory instance to a cloud-based Microsoft Entra instance.
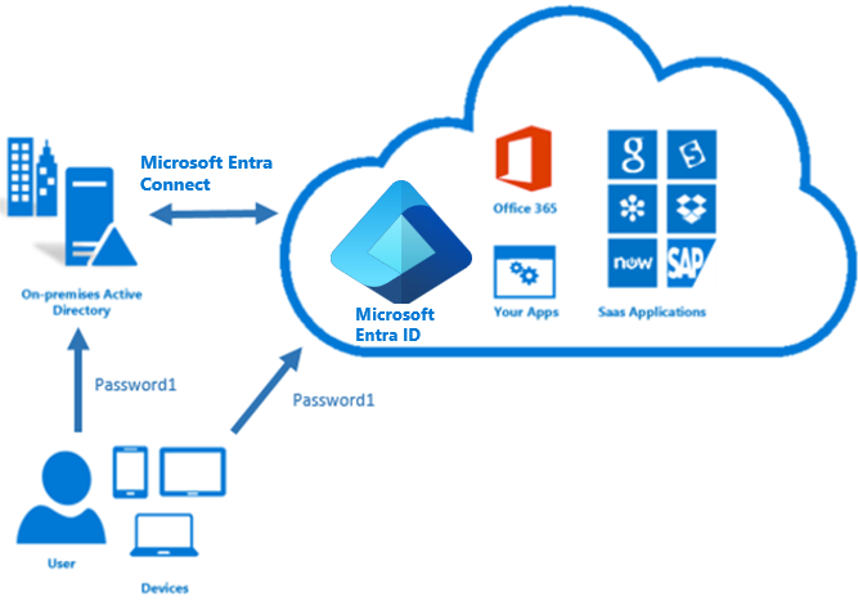
Active Directory Domain Services stores passwords in the form of a hash value representation of the actual user password. A hash value is a result of a one-way mathematical function (the hashing algorithm). There is no method to revert the result of a one-way function to the plain text version of a password. To synchronize your password, Microsoft Entra Connect sync extracts your password hash from the on-premises Active Directory instance. Extra security processing is applied to the password hash before it is synchronized to the Microsoft Entra authentication service. Passwords are synchronized on a per-user basis and in chronological order.
The actual data flow of the password hash synchronization process is similar to the synchronization of user data. However, passwords are synchronized more frequently than the standard directory synchronization window for other attributes. The password hash synchronization process runs every 2 minutes. You cannot modify the frequency of this process. When you synchronize a password, it overwrites the existing cloud password.
The first time you enable the password hash synchronization feature, it performs an initial synchronization of the passwords of all in-scope users. You cannot explicitly define a subset of user passwords that you want to synchronize during the first synchronization. Once the initial synchronization completes, you can set up a selective password hash synch for future synchronizations.
If there are multiple connectors, it is possible to disable password hash sync for some connectors but not others. When you change an on-premises password, the updated password is synchronized, most often in a matter of minutes. The password hash synchronization feature automatically retries failed synchronization attempts. If an error occurs during an attempt to synchronize a password, an error is logged in your event viewer.
When you install Microsoft Entra Connect by using the Express Settings option, password hash synchronization is automatically enabled. If you use custom settings when you install Microsoft Entra Connect, password hash synchronization is available on the user sign-in page.
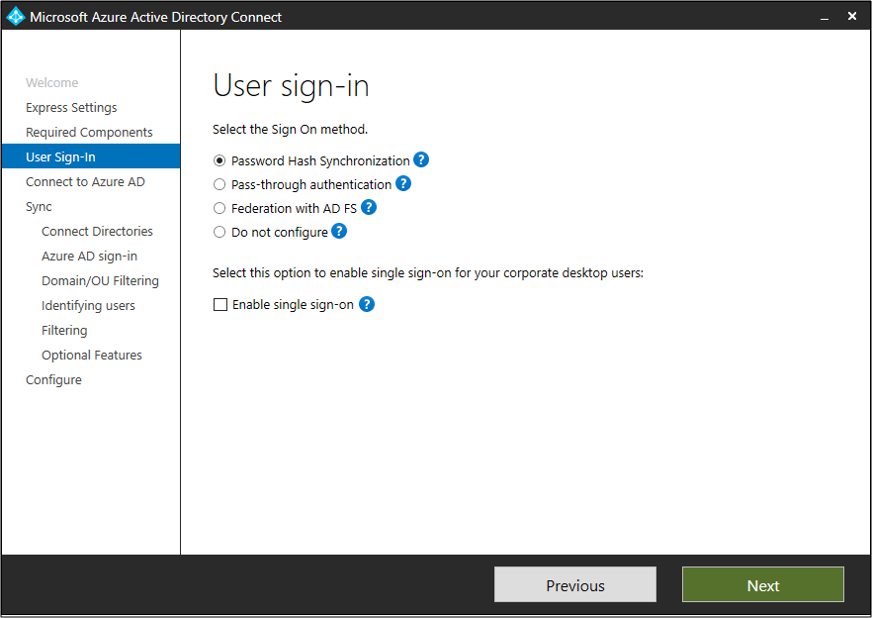
If your server is locked down according to Federal Information Processing Standard (FIPS), then MD5 is disabled.
To enable MD5 for password hash synchronization, perform the following steps:
%programfiles%\Azure A D Sync\Bin.<enforceFIPSPolicy enabled="false"/>For reference, this snippet is what it should look like:
<configuration>
<runtime>
<enforceFIPSPolicy enabled="false"/>
</runtime>
</configuration>
Configure PingFederate with Microsoft Entra Connect to set up federation with the domain you want connected. The following prerequisites are required:
After you choose to set up federation by using PingFederate in AD Connect, you're asked to verify the domain you want to federate. Select the domain from the drop-down menu.
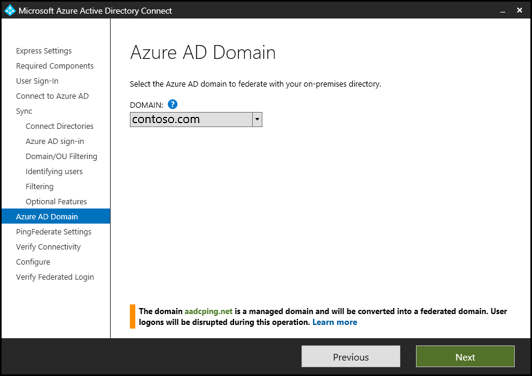
Configure PingFederate as the federation server for each federated Azure domain. Then select Export Settings to share this information with your PingFederate administrator. The federation server administrator updates the configuration and provides the PingFederate server URL and port number so that Microsoft Entra Connect can verify the metadata settings.
Please sign in to use this experience.
Sign in