Important
The Microsoft Teams admin center is gradually replacing the Skype for Business admin center, and we're migrating Teams settings to it from the Microsoft 365 admin center. If a setting has been migrated, you'll see a notification and then be directed to the setting's location in the Teams admin center. For more information, see Manage Teams during the transition to the Teams admin center.
The audit log can help you investigate specific activities across Microsoft services. For Microsoft Teams, here are some of the activities that are audited:
- Team creation
- Team deletion
- Added channel
- Deleted channel
- Changed channel setting
For a complete list of Teams activities that are audited, see Teams activities in the audit log.
Note
Audit events from private channels are also logged as they are for teams and standard channels.
Turn on auditing in Teams
Before you can look at audit data, you have to first turn on auditing in the Microsoft Purview portal. For more information, see Turn auditing on or off.
Important
Audit data is only available from the point at which you turned on auditing.
Retrieve Teams data from the audit log
To retrieve audit logs for Teams activities, you'll use the Microsoft Purview portal. For step-by-step instructions, see Search the audit log.
Important
Audit data is only visible in the audit log if auditing is turned on.
The length of time that an audit record is retained and searchable in the audit log depends on your Microsoft 365 or Office 365 subscription, and specifically the type of license that's assigned to users. To learn more, see the Security & Compliance Center service description.
Tips for searching the audit log
Here are tips for searching for Teams activities in the audit log.
You can select specific activities to search for by clicking the checkbox next to one or more activities. If an activity is selected, you can select it to cancel the selection. You can also use the search box to display the activities that contain the keyword that you type.
To display events for activities run using cmdlets, select Show results for all activities in the Activities list. If you know the name of the operation for these activities, type it in the search box to display the activity, and then select it.
To clear the current search criteria, select Clear all. The date range returns to the default of the last seven days.
If 5,000 results are found, you can probably assume that there are more than 5,000 events that met the search criteria. You can refine the search criteria and rerun the search to return fewer results, or you can export all the search results by selecting Export > Download all results. For step-by-step instructions to export audit logs, see Search the audit log.
Check out this video for using audio log search. Join Ansuman Acharya, a program manager for Teams, as he demonstrates how to do an audit log search for Teams.
For a list of all events that are logged for user and admin activities in Teams in the Microsoft 365 audit log, see:
Office 365 Management Activity API
You can use the Office 365 Management Activity API to retrieve information about Teams events. To learn more about the Management Activity API schema for Teams, see Teams schema.
Attribution in Teams audit logs
Membership changes to Teams (such as users added or deleted) made through Microsoft Entra ID, Microsoft 365 admin portal, or Microsoft 365 Groups Graph API will appear in Teams audit messages and in the General channel with an attribution to an existing owner of the team, and not to the actual initiator of the action. In these scenarios, consult Microsoft Entra ID or Microsoft 365 Group audit logs to see the relevant information.
Use Defender for Cloud Apps to set activity policies
Using Microsoft Defender for Cloud Apps integration, you can set activity policies to enforce a wide range of automated processes using the app provider's APIs. These policies enable you to monitor specific activities carried out by various users, or follow unexpectedly high rates of one certain type of activity.
After you set an activity detection policy, it starts to generate alerts. Alerts are only generated on activities that occur after you create the policy. Here's some example scenarios for how you can use activity policies in Defender for Cloud Apps to monitor Teams activities.
One scenario you might want to keep an eye on, from a business perspective, is the addition of external users to your Teams environment. If external users are enabled, monitoring their presence is a good idea. You can use Defender for Cloud Apps to identify potential threats.

The screenshot of this policy to monitor adding external users allows you to name the policy, set the severity according to your business needs, set it as (in this case) a single activity, and then establish the parameters that will specifically monitor only the addition of noninternal users, and limit this activity to Teams.
The results from this policy can be viewed in the activity log:

Here you can review matches to the policy you've set, and make any adjustments as needed, or export the results to use elsewhere.
As mentioned earlier, you can monitor deletion scenarios. It's possible to create a policy that would monitor mass deletion of Teams sites. In this example, an alert-based policy is set up to detect mass deletion of teams in a span of 30 minutes.
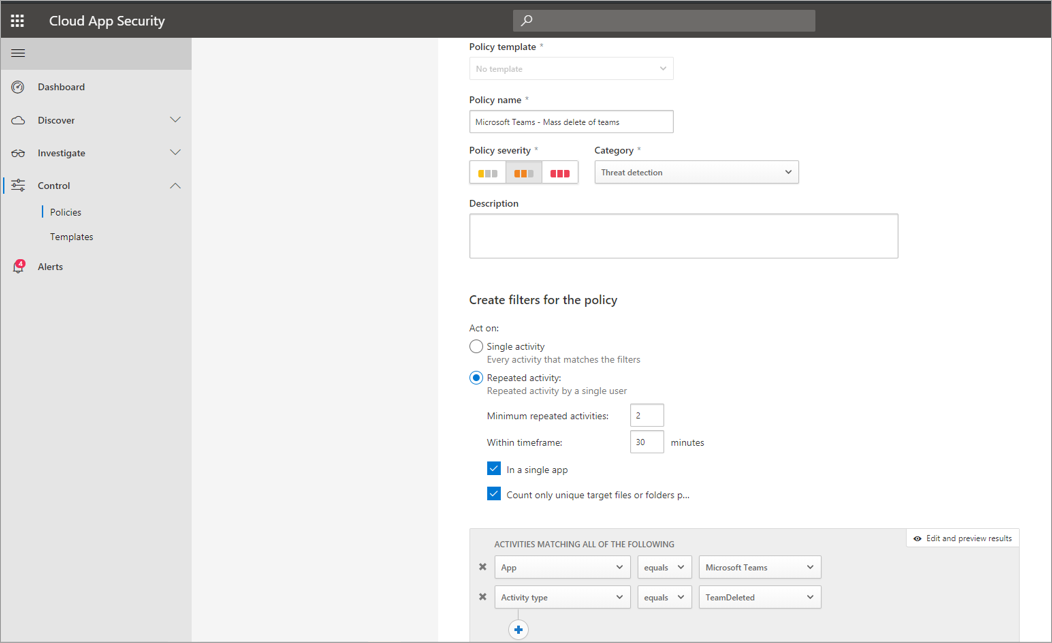
As the screenshot shows, you can set many different parameters for this policy to monitor Teams deletions, including severity, single or repeated action, and parameters limiting this to Teams and site deletion. This can be done independently of a template, or you might have a template created to base this policy on, depending on your organizational needs.
After you establish a policy that works for your business, you can review the results in the activity log as events are triggered:
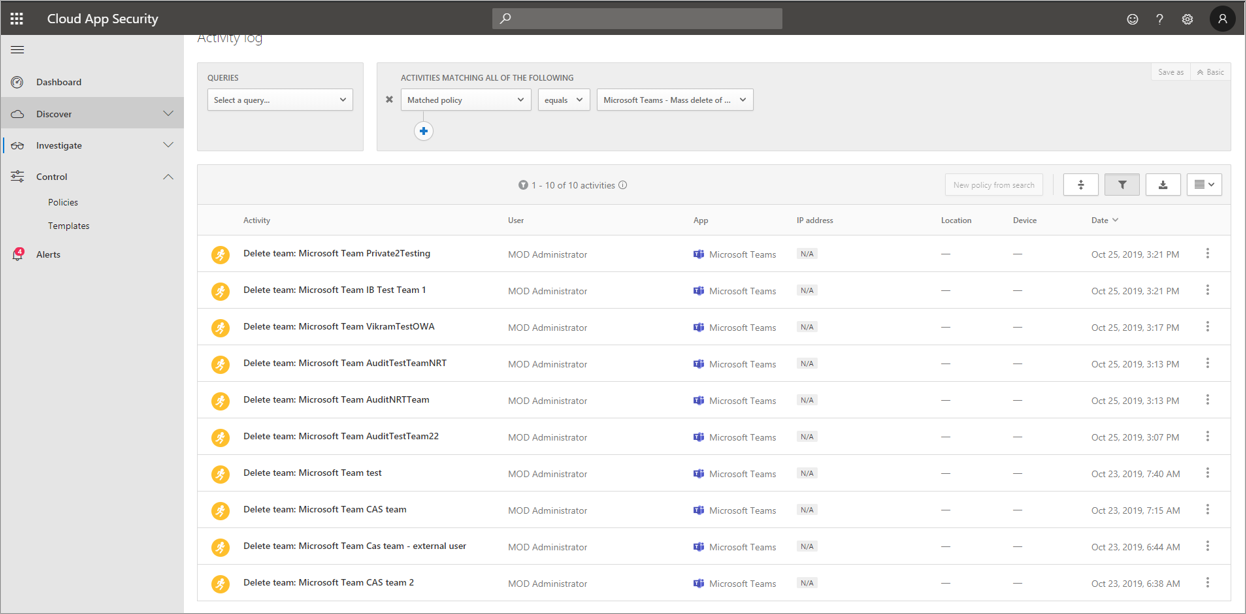
You can filter down to the policy you've set to see the results of that policy. If the results you're getting in the activity log aren't satisfactory (mightbe you're seeing lots of results, or nothing at all), this might help you to fine-tune the query to make it more relevant to what you need it to do.
Alert and governance scenario
You can set alerts and send emails to admins and other users when an activity policy is triggered. You can set automated governance actions such as suspending a user or making a user to sign in again in an automated way. This example shows how a user account can be suspended when an activity policy is triggered and determines a user deleted two or more teams in 30 minutes.

Use Defender for Cloud Apps to set anomaly detection policies
Anomaly detection policies in Defender for Cloud Apps provide out-of-the-box user and entity behavioral analytics (UEBA) and machine learning (ML) so that you can immediately run advanced threat detection across your cloud environment. Because they're automatically enabled, the new anomaly detection policies provide immediate results by providing immediate detections, targeting numerous behavioral anomalies across your users and the machines and devices connected to your network. Additionally, the new policies expose more data from the Defender for Cloud Apps detection engine, to help you speed up the investigation process and contain ongoing threats.
We're working to integrate Teams events into anomaly detection policies. For now, you can set up anomaly detection policies for other Office products and take action items on users who match those policies.




