Audit compliance of Azure container registries using Azure Policy
Azure Policy is a service in Azure that you use to create, assign, and manage policy definitions. These policy definitions enforce different rules and effects over your resources, so those resources stay compliant with your corporate standards and service level agreements.
This article introduces built-in policy definitions for Azure Container Registry. Use these definitions to audit new and existing registries for compliance.
There is no charge for using Azure Policy.
Built-in policy definitions
The following built-in policy definitions are specific to Azure Container Registry:
| Name (Azure portal) |
Description | Effect(s) | Version (GitHub) |
|---|---|---|---|
| [Preview]: Container Registry should be Zone Redundant | Container Registry can be configured to be Zone Redundant or not. When the zoneRedundancy property for a Container Registry is set to 'Disabled', it means the registry is not Zone Redundant. Enforcing this policy helps ensure that your Container Registry is appropriately configured for zone resilience, reducing the risk of downtime during zone outages. | Audit, Deny, Disabled | 1.0.0-preview |
| [Preview]: Container Registry should use a virtual network service endpoint | This policy audits any Container Registry not configured to use a virtual network service endpoint. | Audit, Disabled | 1.0.0-preview |
| Azure registry container images should have vulnerabilities resolved (powered by Microsoft Defender Vulnerability Management) | Container image vulnerability assessment scans your registry for commonly known vulnerabilities (CVEs) and provides a detailed vulnerability report for each image. Resolving vulnerabilities can greatly improve your security posture, ensuring images are safe to use prior to deployment. | AuditIfNotExists, Disabled | 1.0.1 |
| Configure container registries to disable anonymous authentication. | Disable anonymous pull for your registry so that data not accessible by unauthenticated user. Disabling local authentication methods like admin user, repository scoped access tokens and anonymous pull improves security by ensuring that container registries exclusively require Azure Active Directory identities for authentication. Learn more at: https://aka.ms/acr/authentication. | Modify, Disabled | 1.0.0 |
| Configure container registries to disable ARM audience token authentication. | Disable Azure Active Directory ARM audience tokens for authentication to your registry. Only Azure Container Registry (ACR) audience tokens will be used for authentication. This will ensure only tokens meant for usage on the registry can be used for authentication. Disabling ARM audience tokens does not affect admin user's or scoped access tokens' authentication. Learn more at: https://aka.ms/acr/authentication. | Modify, Disabled | 1.0.0 |
| Configure container registries to disable local admin account. | Disable admin account for your registry so that it is not accessible by local admin. Disabling local authentication methods like admin user, repository scoped access tokens and anonymous pull improves security by ensuring that container registries exclusively require Azure Active Directory identities for authentication. Learn more at: https://aka.ms/acr/authentication. | Modify, Disabled | 1.0.1 |
| Configure Container registries to disable public network access | Disable public network access for your Container Registry resource so that it's not accessible over the public internet. This can reduce data leakage risks. Learn more at https://aka.ms/acr/portal/public-network and https://aka.ms/acr/private-link. | Modify, Disabled | 1.0.0 |
| Configure container registries to disable repository scoped access token. | Disable repository scoped access tokens for your registry so that repositories are not accessible by tokens. Disabling local authentication methods like admin user, repository scoped access tokens and anonymous pull improves security by ensuring that container registries exclusively require Azure Active Directory identities for authentication. Learn more at: https://aka.ms/acr/authentication. | Modify, Disabled | 1.0.0 |
| Configure Container registries with private endpoints | Private endpoints connect your virtual network to Azure services without a public IP address at the source or destination. By mapping private endpoints to your premium container registry resources, you can reduce data leakage risks. Learn more at: https://aka.ms/privateendpoints and https://aka.ms/acr/private-link. | DeployIfNotExists, Disabled | 1.0.0 |
| Container registries should be encrypted with a customer-managed key | Use customer-managed keys to manage the encryption at rest of the contents of your registries. By default, the data is encrypted at rest with service-managed keys, but customer-managed keys are commonly required to meet regulatory compliance standards. Customer-managed keys enable the data to be encrypted with an Azure Key Vault key created and owned by you. You have full control and responsibility for the key lifecycle, including rotation and management. Learn more at https://aka.ms/acr/CMK. | Audit, Deny, Disabled | 1.1.2 |
| Container registries should have anonymous authentication disabled. | Disable anonymous pull for your registry so that data is not accessible by unauthenticated user. Disabling local authentication methods like admin user, repository scoped access tokens and anonymous pull improves security by ensuring that container registries exclusively require Azure Active Directory identities for authentication. Learn more at: https://aka.ms/acr/authentication. | Audit, Deny, Disabled | 1.0.0 |
| Container registries should have ARM audience token authentication disabled. | Disable Azure Active Directory ARM audience tokens for authentication to your registry. Only Azure Container Registry (ACR) audience tokens will be used for authentication. This will ensure only tokens meant for usage on the registry can be used for authentication. Disabling ARM audience tokens does not affect admin user's or scoped access tokens' authentication. Learn more at: https://aka.ms/acr/authentication. | Audit, Deny, Disabled | 1.0.0 |
| Container registries should have exports disabled | Disabling exports improves security by ensuring data in a registry is accessed solely via the dataplane ('docker pull'). Data cannot be moved out of the registry via 'acr import' or via 'acr transfer'. In order to disable exports, public network access must be disabled. Learn more at: https://aka.ms/acr/export-policy. | Audit, Deny, Disabled | 1.0.0 |
| Container registries should have local admin account disabled. | Disable admin account for your registry so that it is not accessible by local admin. Disabling local authentication methods like admin user, repository scoped access tokens and anonymous pull improves security by ensuring that container registries exclusively require Azure Active Directory identities for authentication. Learn more at: https://aka.ms/acr/authentication. | Audit, Deny, Disabled | 1.0.1 |
| Container registries should have repository scoped access token disabled. | Disable repository scoped access tokens for your registry so that repositories are not accessible by tokens. Disabling local authentication methods like admin user, repository scoped access tokens and anonymous pull improves security by ensuring that container registries exclusively require Azure Active Directory identities for authentication. Learn more at: https://aka.ms/acr/authentication. | Audit, Deny, Disabled | 1.0.0 |
| Container registries should have SKUs that support Private Links | Azure Private Link lets you connect your virtual network to Azure services without a public IP address at the source or destination. The private link platform handles the connectivity between the consumer and services over the Azure backbone network. By mapping private endpoints to your container registries instead of the entire service, data leakage risks are reduced. Learn more at: https://aka.ms/acr/private-link. | Audit, Deny, Disabled | 1.0.0 |
| Container registries should not allow unrestricted network access | Azure container registries by default accept connections over the internet from hosts on any network. To protect your registries from potential threats, allow access from only specific private endpoints, public IP addresses or address ranges. If your registry doesn't have network rules configured, it will appear in the unhealthy resources. Learn more about Container Registry network rules here: https://aka.ms/acr/privatelink, https://aka.ms/acr/portal/public-network and https://aka.ms/acr/vnet. | Audit, Deny, Disabled | 2.0.0 |
| Container registries should prevent cache rule creation | Disable cache rule creation for your Azure Container Registry to prevent pull through cache pulls. Learn more at: https://aka.ms/acr/cache. | Audit, Deny, Disabled | 1.0.0 |
| Container registries should use private link | Azure Private Link lets you connect your virtual network to Azure services without a public IP address at the source or destination. The private link platform handles the connectivity between the consumer and services over the Azure backbone network.By mapping private endpoints to your container registries instead of the entire service, you'll also be protected against data leakage risks. Learn more at: https://aka.ms/acr/private-link. | Audit, Disabled | 1.0.1 |
| Enable logging by category group for Container registries (microsoft.containerregistry/registries) to Event Hub | Resource logs should be enabled to track activities and events that take place on your resources and give you visibility and insights into any changes that occur. This policy deploys a diagnostic setting using a category group to route logs to an Event Hub for Container registries (microsoft.containerregistry/registries). | DeployIfNotExists, AuditIfNotExists, Disabled | 1.2.0 |
| Enable logging by category group for Container registries (microsoft.containerregistry/registries) to Log Analytics | Resource logs should be enabled to track activities and events that take place on your resources and give you visibility and insights into any changes that occur. This policy deploys a diagnostic setting using a category group to route logs to a Log Analytics workspace for Container registries (microsoft.containerregistry/registries). | DeployIfNotExists, AuditIfNotExists, Disabled | 1.1.0 |
| Enable logging by category group for Container registries (microsoft.containerregistry/registries) to Storage | Resource logs should be enabled to track activities and events that take place on your resources and give you visibility and insights into any changes that occur. This policy deploys a diagnostic setting using a category group to route logs to a Storage Account for Container registries (microsoft.containerregistry/registries). | DeployIfNotExists, AuditIfNotExists, Disabled | 1.1.0 |
| Public network access should be disabled for Container registries | Disabling public network access improves security by ensuring that container registries are not exposed on the public internet. Creating private endpoints can limit exposure of container registry resources. Learn more at: https://aka.ms/acr/portal/public-network and https://aka.ms/acr/private-link. | Audit, Deny, Disabled | 1.0.0 |
Create policy assignments
- Create policy assignments using the Azure portal, Azure CLI, a Resource Manager template, or the Azure Policy SDKs.
- Scope a policy assignment to a resource group, a subscription, or an Azure management group. Container registry policy assignments apply to existing and new container registries within the scope.
- Enable or disable policy enforcement at any time.
Note
After you create or update a policy assignment, it takes some time for the assignment to evaluate resources in the defined scope. See information about policy evaluation triggers.
Review policy compliance
Access compliance information generated by your policy assignments using the Azure portal, Azure command-line tools, or the Azure Policy SDKs. For details, see Get compliance data of Azure resources.
When a resource is non-compliant, there are many possible reasons. To determine the reason or to find the change responsible, see Determine non-compliance.
Policy compliance in the portal:
Select All services, and search for Policy.
Select Compliance.
Use the filters to limit compliance states or to search for policies.
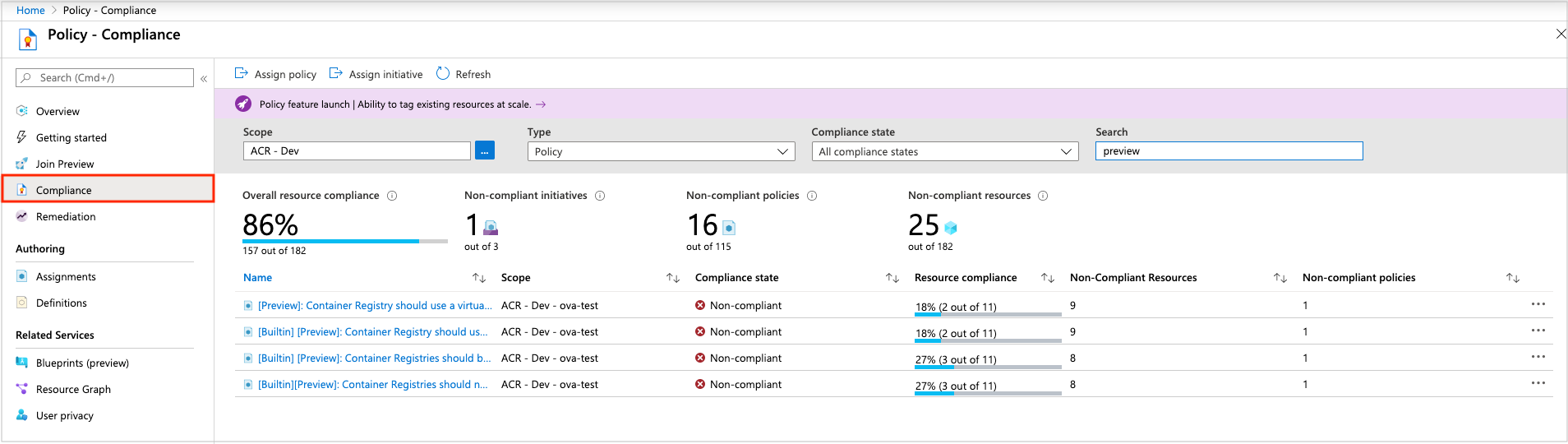
Select a policy to review aggregate compliance details and events. If desired, then select a specific registry for resource compliance.
Policy compliance in the Azure CLI
You can also use the Azure CLI to get compliance data. For example, use the az policy assignment list command in the CLI to get the policy IDs of the Azure Container Registry policies that are applied:
az policy assignment list --query "[?contains(displayName,'Container Registries')].{name:displayName, ID:id}" --output table
Sample output:
Name ID
------------------------------------------------------------------------------------- --------------------------------------------------------------------------------------------------------------------------------
Container Registries should not allow unrestricted network access /subscriptions/<subscriptionID>/providers/Microsoft.Authorization/policyAssignments/b4faf132dc344b84ba68a441
Container Registries should be encrypted with a Customer-Managed Key (CMK) /subscriptions/<subscriptionID>/providers/Microsoft.Authorization/policyAssignments/cce1ed4f38a147ad994ab60a
Then run az policy state list to return the JSON-formatted compliance state for all resources under a specific policy ID:
az policy state list \
--resource <policyID>
Or run az policy state list to return the JSON-formatted compliance state of a specific registry resource, such as myregistry:
az policy state list \
--resource myregistry \
--namespace Microsoft.ContainerRegistry \
--resource-type registries \
--resource-group myresourcegroup
Next steps
Learn more about Azure Policy definitions and effects.
Create a custom policy definition.
Learn more about governance capabilities in Azure.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for