This article provides information about security solutions that integrate with Microsoft Defender for Cloud.
Defender for Cloud integrates with both Microsoft services and partner solutions. Integration with solutions helps you to:
- Simplify deployment: Defender for Cloud offers streamlined provisioning of integrated partner solutions. For solutions like antimalware and vulnerability assessment, Defender for Cloud can provision the agent on your virtual machines. For firewall appliances, Defender for Cloud can take care of much of the network configuration required.
- Integrate detection: Security events from partner solutions are automatically collected, aggregated, and displayed as part of Defender for Cloud alerts and incidents. These events are also fused with detections from other sources to provide advanced threat-detection capabilities.
- Unify monitoring and management: Integrated events in Defender for Cloud help you to monitor partner solutions at a glance. Basic management is available, with easy access to advanced setup by using the partner solution.
- Extend capabilities: Some integrations extend Defender for Cloud capabilities. For example:
- Defender for Cloud supports third-party integrations to help enhance runtime security capabilities provided by Defender for APIs.
- Defender for Cloud integrates with ServiceNow to help prioritize remediation of security recommendations, and to create and monitor tickets.
Integrated solutions appear in the Azure portal, in Defender for Cloud -> Management -> Security solutions.
Azure security solutions that are deployed from Defender for Cloud are automatically connected. You can also connect other security data sources, including computers running on-premises or in other clouds.

The Connected solutions section includes security solutions that are currently connected to Defender for Cloud.
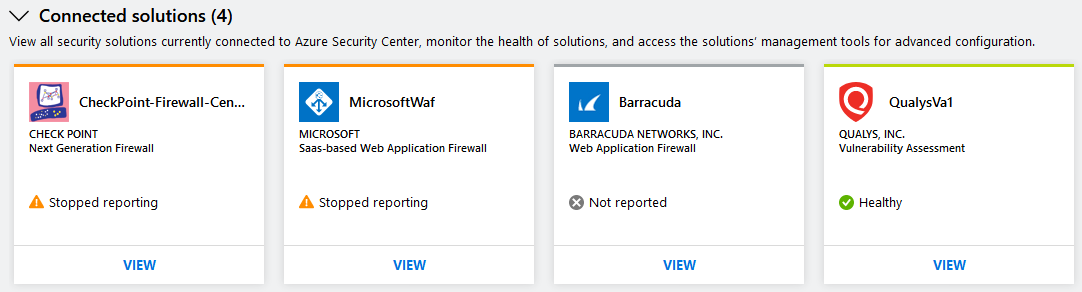
The status of a security solution can be:
- Healthy (green): No health issues.
- Unhealthy (red): There's a health issue that requires immediate attention. If no health data is available and no alerts were received within the last 14 days, Defender for Cloud indicates that the solution is unhealthy or not reporting.
- Stopped reporting (orange): The solution stopped reporting health status.
- Not reported (gray): No health data is available. The solution didn't report anything yet and no health data is available. A solution's status might be unreported if it was connected recently and is still deploying.
If health status isn't available, Defender for Cloud shows the date and time of the last event received to indicate whether the solution is reporting or not.
You can drill down into each solution to manage it.
Defender for Cloud automatically discovers security solutions that are running in Azure but not connected to Defender for Cloud, and displays them in the Discovered solutions section. You can connect solutions as needed to integrate it with Defender for Cloud.
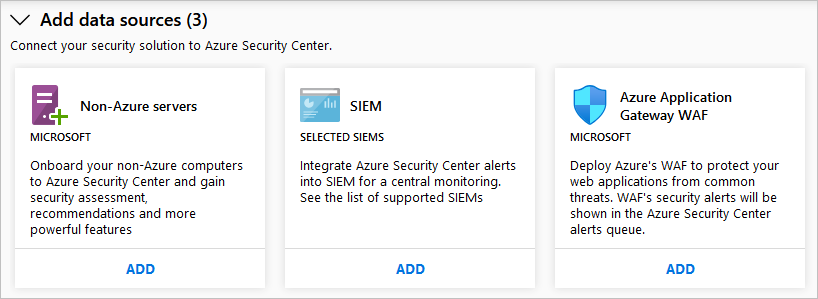
The Add data sources section includes other available data sources that can be connected. For instructions on adding data from any of these sources, select ADD.
Continuously export Defender for Cloud data.


