Events
Mar 31, 11 PM - Apr 2, 11 PM
The biggest SQL, Fabric and Power BI learning event. March 31 – April 2. Use code FABINSIDER to save $400.
Register todayThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Applies to:
Azure SQL Database
Azure SQL Managed Instance
Azure Synapse Analytics
If you're limiting access to your storage account in Azure for certain VNets or services, you'll need to enable the appropriate configuration so that Vulnerability Assessment (VA) scanning for SQL Databases or Azure SQL Managed Instances have access to that storage account.
Note
These settings are not required when using Express Configuration.
The SQL Vulnerability Assessment service needs permission to the storage account to save baseline and scan results.
Use SQL Server managed identity:
When you use the Azure portal to save SQL VA settings, Azure checks if you have permission to assign a new role assignment for the managed identity as Storage Blob Data Contributor on the storage. If permissions are assigned, Azure uses SQL Server managed identity, otherwise Azure uses the key method (which is not supported for this scenario).
Note
If you've configured your VA storage account to only be accessible by certain networks or services, you'll need to ensure that VA scans for your Azure SQL Database are able to store the scans on the storage account. You can use the existing storage account, or create a new storage account to store VA scan results for all databases on your logical SQL server.
Note
The vulnerability assessment service can't access storage accounts protected with firewalls or VNets if they require storage access keys.
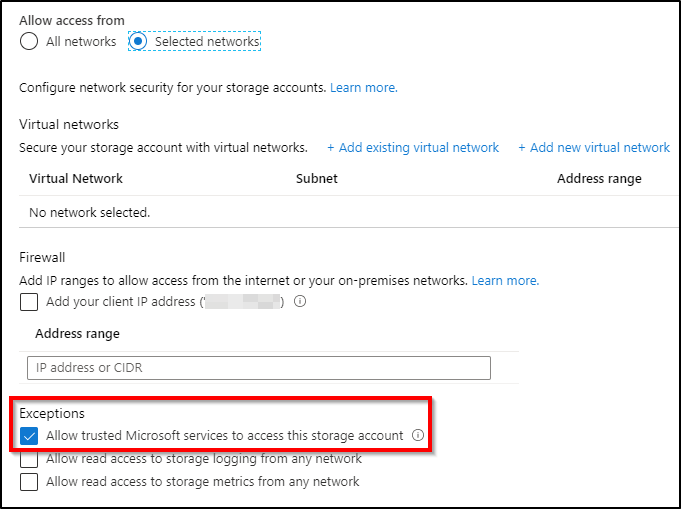
Go to your Resource group that contains the storage account and access the Storage account pane. Under Settings, select Firewall and virtual networks.
Ensure that Allow trusted Microsoft services access to this storage account is checked.
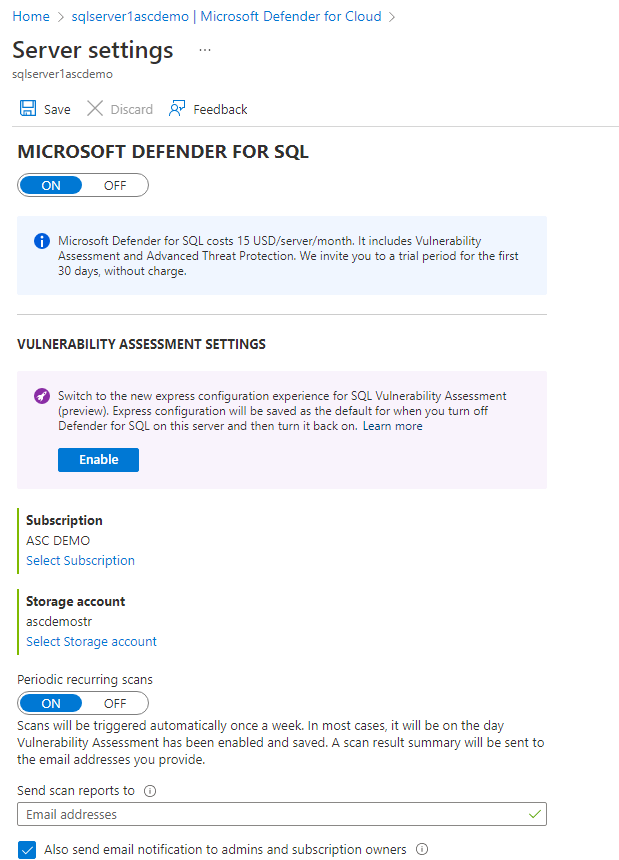
To find out which storage account is being used, do the following steps:
Since Azure SQL Managed Instance isn't a trusted Microsoft Service and has a different VNet from the storage account, executing a VA scan will result in an error.
To support VA scans on Azure SQL Managed Instances, follow the below steps:
Under the Azure SQL Managed Instance's Overview page, note the value under Virtual network / subnet.
Head to the Networking page in the storage account where SQL VA is configured to store the scan results.
Under the Firewalls and virtual networks tab, under Public network access select Enabled from selected virtual networks and IP addresses.
Under the Virtual networks section, click Add existing virtual network and selected the VNET and subnet used by the managed instance that you've noted in the first step.
Troubleshoot common issues related to vulnerability assessment scans.
You might not be able to save changes to vulnerability assessment settings if your storage account doesn't meet some prerequisites or if you have insufficient permissions.
The storage account in which vulnerability assessment scan results are saved must meet the following requirements:
If any of these requirements aren't met, saving changes to vulnerability assessment settings fails.
The following permissions are required to save changes to vulnerability assessment settings:
Setting a new role assignment requires owner or user administrator access to the storage account and the following permissions:
The storage account might not appear in the storage account picker for several reasons:
You might not be able to open a link in a notification email about scan results, or to view scan results if you don't have the required permissions, or if you use a browser that doesn't support opening or displaying scan results.
The following permissions are required to open links in email notifications about scan results or to view scan results:
The Firefox browser doesn't support opening or displaying scan results view. We recommend that you use Microsoft Edge or Chrome to view vulnerability assessment scan results.
Events
Mar 31, 11 PM - Apr 2, 11 PM
The biggest SQL, Fabric and Power BI learning event. March 31 – April 2. Use code FABINSIDER to save $400.
Register today