Azure Security and Compliance Blueprint: PaaS Web Application Hosting for UK OFFICIAL Workloads
Azure Security and Compliance Blueprints
Azure Blueprints consist of guidance documents and automation templates that deploy cloud-based architectures to offer solutions to scenarios that have accreditation or compliance requirements. Azure Blueprints are guidance and automation template collections that allow Microsoft Azure customers to accelerate delivery of their business goals through provisioning a foundation architecture that can be extended to meet any further requirements.
Overview
This Azure Security and Compliance Blueprint provides guidance and automation scripts to deliver a Microsoft Azure platform as a service (PaaS) hosted web application architecture appropriate for handling workloads classified as UK OFFICIAL. This security classification encompasses the majority of information created or processed by the public sector. This includes routine business operations and services, which if lost, stolen, or published in the media, some of which could have damaging consequences. The typical threat profile for the OFFICIAL classification is much the same as a private business who provides valuable information and services. UK OFFICIAL anticipates the need to defend UK Government data or services against threat or compromise by attackers with bounded capabilities and resources such as (but is not limited to) hactivists, single-issue pressure groups, investigative journalists, competent individual hackers, and the majority of criminal individuals and groups.
This blueprint has been reviewed by the UK National Cyber Security Centre (NCSC) and aligns to the NCSC 14 Cloud Security Principles.
The architecture uses Azure platform as a service components to deliver an environment that allows customers to avoid the expense and complexity of buying software licenses, of managing the underlying application infrastructure and middleware or the development tools, and other resources. Customers manage the applications and services that they develop, focusing on delivering business value, whilst Microsoft Azure manages the other Azure resources such as virtual machines, storage and networking, putting more of the division of responsibility for infrastructure management on to the Azure platform. Azure App Services offers auto-scaling, high availability, supports Windows and Linux, and enables automated deployments from GitHub, Azure DevOps, or any Git repository as default services. Through using App Services, developers can concentrate on delivering business value without the overhead of managing infrastructure. It is possible to build greenfield new Java, PHP, Node.js, Python, HTML or C# web applications or also to migrate existing cloud or on premises web applications to Azure App Services (although thorough due diligence and testing to confirm performance is required).
This blueprint focuses on the provisioning of a secure foundation platform as a service web-based interface for public and also back-office users. This blueprint design scenario considers the use of Azure hosted web-based services where a public user can securely submit, view, and manage sensitive data; also that a back office or government operator can securely process the sensitive data that the public user has submitted. Use cases for this scenario could include:
- A user submitting a tax return, with a government operator processing the submission;
- A user requesting a service through a web-based application, with a back-office user validating and delivering the service; or
- A user seeking and viewing public domain help information concerning a government service.
Using Azure Resource Manager templates and Azure Command Line Interface scripts, the blueprint deploys an environment that aligns to the UK National Cyber Security Centre (NCSC) 14 Cloud Security Principles and the Center for Internet Security (CIS) Critical Security Controls. The NCSC recommends their Cloud Security Principles be used by customers to evaluate the security properties of the service and to help understand the division of responsibility between the customer and supplier. Microsoft has provided information against each of these principles to help better understand the split of responsibilities. This architecture and corresponding Azure Resource Manager templates are supported by the Microsoft whitepaper, 14 Cloud Security Controls for UK cloud Using Microsoft Azure. This architecture has been reviewed by the NCSC, and aligns with the UK NCSC 14 Cloud Security Principles, thus enabling public sector organizations to fast-track their ability to meet compliance obligations using cloud-based services globally and in the UK on the Microsoft Azure cloud. This template deploys the infrastructure for the workload. Application code and supporting business tier and data tier software must be installed and configured by customers. Detailed deployment instructions are available here.
This blueprint is a foundation architecture. Our customers can use this blueprint as a foundation for their OFFICIAL classification web-based workloads and expand on the templates and resources with their own requirements. This blueprint builds on the principles of the UK-OFFICAL Three-Tier IaaS Web Applications blueprint to offer our customers both infrastructure as a service (IaaS) and PaaS implementation choices for hosting web-based workloads.
To deploy this blueprint, an Azure subscription is required. If you do not have an Azure subscription, you can sign up quickly and easily at no charge: Get Started with Azure. Click here for deployment instructions.
Architecture and components
This blueprint delivers a web application hosting solution in an Azure cloud environment that supports UK OFFICIAL workloads. The architecture delivers a secure environment that leverages Azure platform as a service capabilities. Within the environment, two App Service web apps are deployed (one for public users and one for back-office users), with an API App tier to provide the business services for the web front end. An Azure SQL Database is deployed as a managed relational data store for the application. Connectivity to these components from outside the platform and between all these components is encrypted through TLS 1.2 to ensure data in transport privacy, with access authenticated by Azure Active Directory.
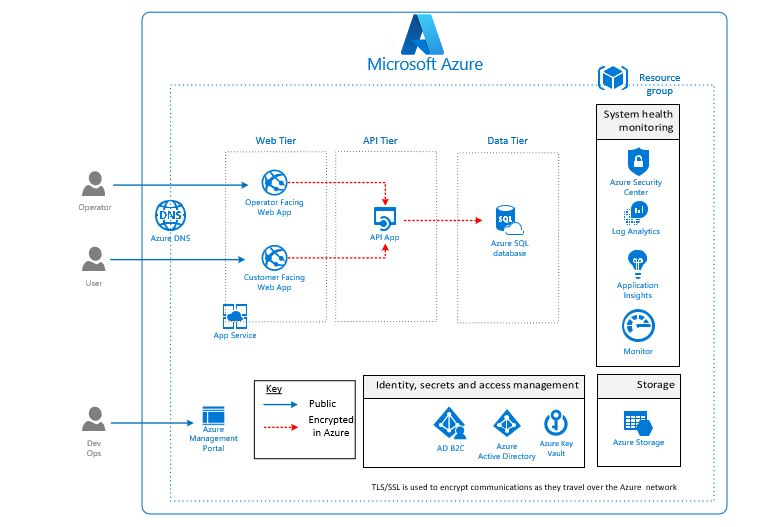
As part of the deployment architecture, secure storage provision, monitoring & logging, unified security management & advanced threat protection, and management capabilities are also deployed to ensure that customers have all the tools required to secure and monitor their environment for this solution.
This solution uses the following Azure services. Details of the deployment architecture are in the deployment architecture section.
- Azure Active Directory
- App Service
- Web App
- API App
- Azure DNS
- Key Vault
- Azure Monitor (logs)
- Application Insights
- Azure Resource Manager
- Azure Security Center
- Azure SQL Database
- Azure Storage
Deployment architecture
The following section details the deployment and implementation elements.
Security
Identity and authentication
This blueprint ensures that access to resources is protected through directory and identity management services. This architecture makes full use of identity as the security perimeter.
The following technologies provide identity management capabilities in the Azure environment:
- Azure Active Directory (Azure AD) is Microsoft's multi-tenant cloud-based directory and identity management service. All users for the solution were created in Azure Active Directory, including users accessing the SQL Database.
- Authentication to the operator facing web application and access for the administration of the Azure resources is performed using Azure AD. For more information, see Integrating applications with Azure Active Directory.
- Database column encryption uses Azure AD to authenticate the application to Azure SQL Database. For more information, see Always Encrypted: Protect sensitive data in SQL Database.
- The citizen facing web application is configured for public access. To allow for account creation and authentication through active directory or social network identity providers Azure Active Directory B2C can be integrated if required.
- Azure Active Directory Identity Protection detects potential vulnerabilities and risky accounts provides recommendations to enhance the security posture of your organization’s identities, configures automated responses to detected suspicious actions related to your organization’s identities, and investigates suspicious incidents and takes appropriate action to resolve them.
- Azure Role-based Access Control (RBAC) enables precisely focused access management for Azure. Subscription access is limited to the subscription administrator, and Azure Key Vault access is restricted only to users who require key management access.
- Through leveraging Azure Active Directory Conditional Access customers can enforce additional security controls on access to apps or users in their environment based on specific conditions such as location, device, state and sign in risk.
- Azure DDoS Protection combined with application design best practices, provides defense against DDoS attacks, with always-on traffic monitoring, and real-time mitigation of common network-level attacks. With a PaaS architecture, platform level DDoS protection is transparent to the customer and incorporated into the platform but it is important to note that the application security design responsibility lies with the customer.
Data in transit
Data is transit from outside and between Azure components is protected using Transport Layer Security/Secure Sockets Layer (TLS/SSL), which uses symmetric cryptography based on a shared secret to encrypt communications as they travel over the network. By default, network traffic is secured using TLS 1.2.
Security and malware protection
Azure Security Center provides a centralized view of the security state of all your Azure resources. At a glance, you can verify that the appropriate security controls are in place and configured correctly, and you can quickly identify any resources that require attention.
Azure Advisor is a personalized cloud consultant that helps you follow best practices to optimize your Azure deployments. It analyzes your resource configuration and usage telemetry and then recommends solutions that can help you improve the cost effectiveness, performance, high availability, and security of your Azure resources.
Microsoft Antimalware is a real-time protection capability that helps identify and remove viruses, spyware, and other malicious software. This by default is installed on the underlying PaaS virtual machine infrastructure and is managed by the Azure fabric transparently to the customer.
PaaS services in this blueprint
Azure App Service
Azure App Service provides a fully managed web hosting environment for web application developed in Java, PHP, Node.js Python, HTML and C# without having to manage infrastructure. It offers auto-scaling and high availability, supports both Windows and Linux, and enables automated deployments from Azure DevOps or any Git-based repo.
App Service is ISO, SOC, and PCI compliant and can authenticate users with Azure Active Directory or with social login (Google, Facebook, Twitter, and Microsoft authentication.
Basic, Standard, and Premium plans are for production workloads and run on dedicated Virtual Machine instances. Each instance can support multiple applications and domains. App services also support IP address restrictions to secure traffic to trusted IP addresses if required and also managed identities for Azure resources for secure connection to other PaaS services such as Key Vault and Azure SQL Database. Where additional security is required our Isolated plan hosts your apps in a private, dedicated Azure environment and is ideal for apps that require secure connections with your on-premises network, or additional performance and scale.
This template deploys the following App Service features:
- Standard App Service Plan Tier
- Multiple App Service deployment slots: Dev, Preview, QA, UAT and of course Production (default slot).
- Managed identities for Azure resources to connect to Azure Key Vault (this could also be used to provide access to Azure SQL Database
- Integration with Azure Application Insights to monitor performance
- Diagnostic Logs
- Metric alerts
- Azure API Apps
Azure SQL Database
SQL Database is a general-purpose relational database managed service in Microsoft Azure that supports structures such as relational data, JSON, spatial, and XML. SQL Database offers managed single SQL databases, managed SQL databases in an elastic pool, and SQL Managed Instances (in public preview). It delivers dynamically scalable performance and provides options such as columnstore indexes for extreme analytic analysis and reporting, and in-memory OLTP for extreme transactional processing. Microsoft handles all patching and updating of the SQL code base seamlessly and abstracts away all management of the underlying infrastructure.
Azure SQL Database in this blueprint
The Azure SQL Database instance uses the following database security measures:
- Server-level and database-level firewall rules, or through Virtual Network Service Endpoints using virtual network rules.
- Transparent data encryption helps protect Azure SQL Database and Azure Data Warehouse against the threat of malicious activity. It performs real-time encryption and decryption of the database, associated backups, and transaction log files at rest without requiring changes to the application.
- Azure AD authentication, you can centrally manage the identities of database users and other Microsoft services in one central location. Central ID management provides a single place to manage database users and simplifies permission management.
- Use of Azure Active Directory for database administration
- Audit logs to storage accounts
- Metric alerts for failed DB connections
- SQL Threat Detection
- Always Encrypted columns
Azure Storage
Microsoft Azure Storage is a Microsoft-managed cloud service that provides storage that is highly available, secure, durable, scalable, and redundant. Azure Storage consists of Blob storage, File Storage, and Queue storage.
Azure Storage in this blueprint
This template uses the following Azure Storage components:
- Storage Service Encryption
- Only allow HTTPS connections
Data at rest
Through Storage Service Encryption all data written to Azure Storage is encrypted through 256-bit AES encryption, one of the strongest block ciphers available. You can use Microsoft-managed encryption keys with SSE or you can use your own encryption keys.
Storage accounts can be secured via Virtual Network Service Endpoints using virtual network rules.
Detailed information about securing Azure Storage can be found in the security guide.
Secrets management
Azure Key Vault
Key Vault is used to secure application keys and secrets to ensure that they are not accessible by third parties. Key Vault is not intended to be used as a store for user passwords. It allows you to create multiple secure containers, called vaults. These vaults are backed by hardware security modules (HSMs). Vaults help reduce the chances of accidental loss of security information by centralizing the storage of application secrets. Key Vaults also control and log the access to anything stored in them. Azure Key Vault can handle requesting and renewing Transport Layer Security (TLS) certificates, providing the features required for a robust certificate lifecycle management solution.
Azure Key Vault in this blueprint
- Holds the Storage access key, with read access granted to the managed identity of the Customer facing web app
- Holds the SQL Server DBA Password (in a separate vault)
- Diagnostics logging
Monitoring, logging, and audit
Azure Monitor logs
Azure Monitor logs is a service in Azure that helps you collect and analyze data generated by resources in your cloud and on-premises environments.
Azure Monitor logs in this blueprint
- SQL Assessment
- Key Vault diagnostics
- Application Insights connection
- Azure Activity Log
Application Insights
Application Insights is an extensible Application Performance Management (APM) service for web developers on multiple platforms. Used to monitor live web applications it will automatically detect performance anomalies, analyze performance, diagnose issues and to understand how users interact with the app. Application Insights can be deployed on platforms including .NET, Node.js and Java EE, hosted on-premises or in the cloud. It integrates with your DevOps process, and has connection points to a variety of development tools.
Application Insights in this blueprint
This template uses the following Application Insights components:
- Application Insights dashboard per site (Operator, Customer and API)
Azure Activity Logs
Azure Activity Log audits control-plane events for your subscriptions. Using the Activity Log, you can determine the 'what, who, and when' for any write operations (PUT, POST, DELETE) taken on the resources in your subscription. You can also understand the status of the operation and other relevant properties.
Azure Monitor
Azure Monitor enables core monitoring for Azure services by allowing the collection of metrics, activity logs, and diagnostic logs. Azure Monitor provides base-level infrastructure metrics and logs for most services in Microsoft Azure.
Threat model
The data flow diagram for this reference architecture is available for download or can be found below. This model can help customers understand the points of potential risk in the system infrastructure when making modifications.
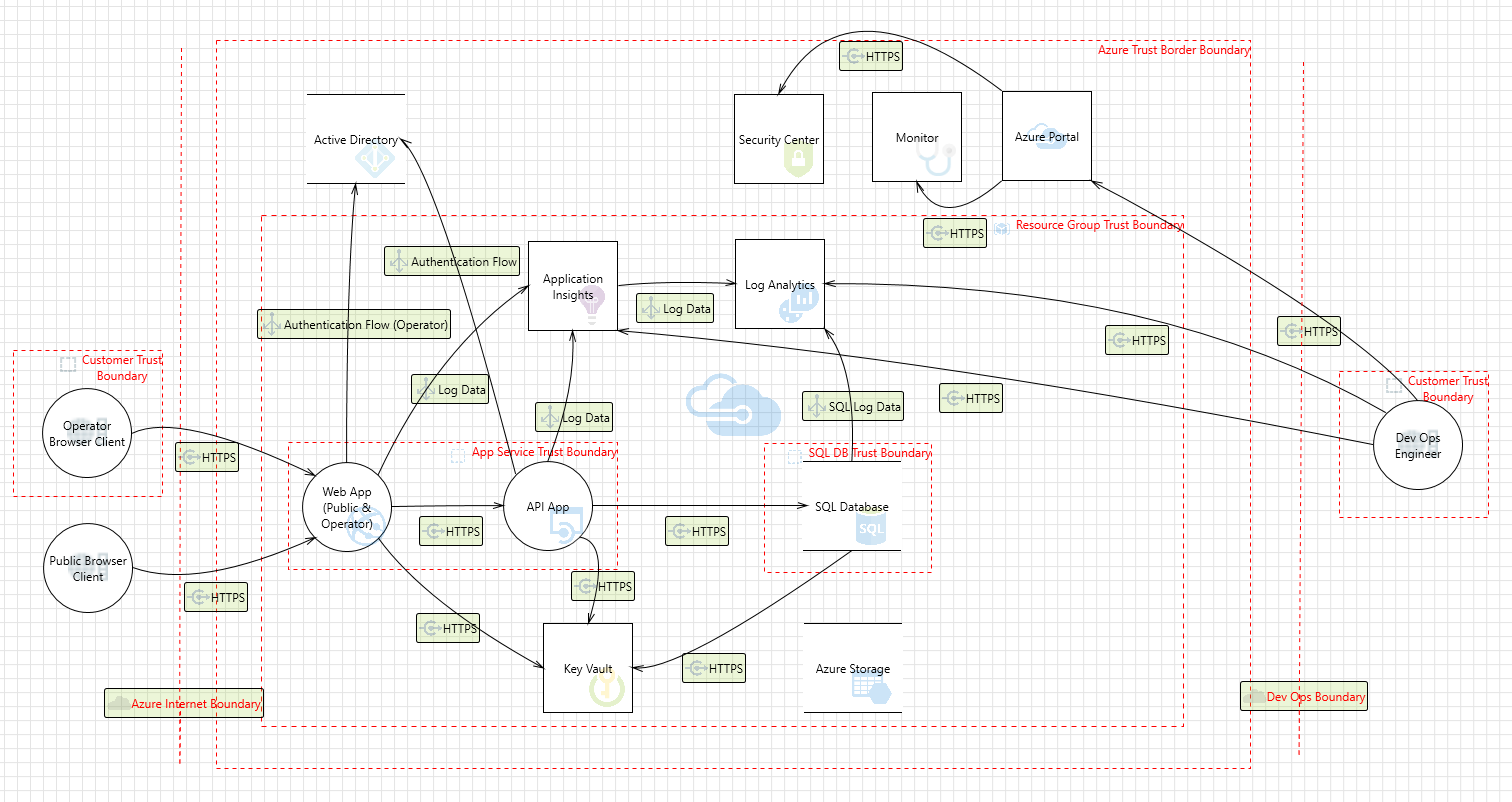
NCSC Cloud Security Principles compliance documentation
The Crown Commercial Service (an agency that works to improve commercial and procurement activity by the government) renewed the classification of Microsoft in-scope enterprise cloud services to G-Cloud v6, covering all its offerings at the OFFICIAL level. Details of Azure and G-Cloud can be found in the Azure UK G-Cloud security assessment summary.
This blueprint aligns to the 14 cloud security principles that are documented in the NCSC Cloud Security Principles to help ensure an environment that supports workloads classified as UK OFFICIAL.
The Azure Security and Compliance Blueprint - UK OFFICIAL Customer Responsibility Matrix (Excel Workbook) lists all 14 cloud security principles and denotes, for each principle (or principle subpart), whether the principle implementation is the responsibility of Microsoft, the customer, or shared between the two.
The Azure Security and Compliance Blueprint - PaaS Web Application for UK OFFICIAL Principle Implementation Matrix (Excel Workbook) lists all 14 cloud security principles and denotes, for each principle (or principle subpart) that is designated a customer responsibility in the Customer Responsibilities Matrix, 1) if the blueprint implements the principle, and 2) a description of how the implementation aligns with the principle requirement(s).
Furthermore, the Cloud Security Alliance (CSA) published the Cloud Control Matrix to support customers in the evaluation of cloud providers and to identify questions that should be answered before moving to cloud services. In response, Microsoft Azure answered the CSA Consensus Assessment Initiative Questionnaire (CSA CAIQ), which describes how Microsoft addresses the suggested principles.
Third-party assessment
This blueprint has been reviewed by the UK National Cyber Security Centre (NCSC) and aligns to the NCSC 14 Cloud Security Principles
The automation templates have been tested by the UK Customer Success Unit Azure Cloud Solution Architect team and by our Microsoft partner, Ampliphae.
Deploy the solution
This Azure Security and Compliance Blueprint Automation is comprised of JSON configuration files and PowerShell scripts that are handled by Azure Resource Manager's API service to deploy resources within Azure. Detailed deployment instructions are available here.
Three approaches have been provided for deployment; A simple "express" Azure CLI 2 suitable for quickly building a test environment; a parameterized Azure CLI 2 approach providing greater configuration for workload environments; and an Azure portal based deployment where the operator can specify the deployment parameters through the Azure portal.
- Clone or download this GitHub repository to your local workstation.
- Review Method 1: Azure CLI 2 (Express version) and execute the provided commands.
- Review Method 1a: Azure CLI 2 (Configuring the deployment via script arguments) and execute the provided commands
- Review Method 2: Azure portal Deployment Process and execute the listed commands
Guidance and recommendations
API Management
Azure API Management could be used in front of the API App Service to provide additional layers of security, throttling and controls to expose, proxy and protect APIs.
Azure B2C
Azure Active Directory B2C may be implemented as a control to allow users to register, create an identity, and enable authorization and access control for the public web application.
Disclaimer
- This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. This document is provided "as-is." Information and views expressed in this document, including URL and other Internet website references, may change without notice. Customers reading this document bear the risk of using it.
- This document does not provide customers with any legal rights to any intellectual property in any Microsoft product or solutions.
- Customers may copy and use this document for internal reference purposes.
- Certain recommendations in this document may result in increased data, network, or compute resource usage in Azure, and may increase a customer's Azure license or subscription costs.
- This architecture is intended to serve as a foundation for customers to adjust to their specific requirements and should not be used as-is in a production environment.
- This document is developed as a reference and should not be used to define all means by which a customer can meet specific compliance requirements and regulations. Customers should seek legal support from their organization on approved customer implementations.